DORA is a EU’s regulation establishing a comprehensive framework on digital operational resilience for EU financial entities. It is lex specialis to the NIS Directive and to the Critical Entity Resilience (CER) Directive. The regulation harmonizes the rules for a wide range of financial entities, including insurance and their Information and Communication Technology (ICT) providers. DORA aims to address a critical security gap in the EU financial system resulting from the lack of a resilience framework for ICT incidents that cannot only be addressed with the allocation of capital to cover losses. DORA was approved on 14 December 2022, published in the EU Official Journal on 27 December 2022. The regulation then entered into force on 16 January 2023 and started to apply on 17 January.
This analysis offers a comprehensive overview of DORA, highlighting impacted entities, the main requirements it introduces, non-compliance penalties, and most relevant deadlines.
Key Insights
- The Digital Operational Resilience Act (DORA) is an EU regulation aimed at strengthening the digital resilience of financial entities by standardizing Information and Communication Technology (ICT) risk management, addressing gaps in cybersecurity, and ensuring operational continuity in the face of cyber threats.
- DORA applies to 20 categories of financial entities and their ICT service providers, including banks, insurance providers, financial market infrastructure, and crypto service providers.
- Under DORA, financial entities must implement a harmonized ICT risk management framework, assess risks associated with their ICT service providers, conduct resilience tests, and report major ICT incidents.
- Regulators can impose inspections, remedial actions, and financial penalties, including fines of up to 2 percent of global turnover for financial entities and up to EUR 5 million for their critical ICT service providers. They can also suspend or put an end to existing contracts between financial entities and their ICT service providers.
- DORA fully applies from 17 January 2025. Financial entities must identify their critical ICT service providers and submit contractual information to regulators by April 2025.
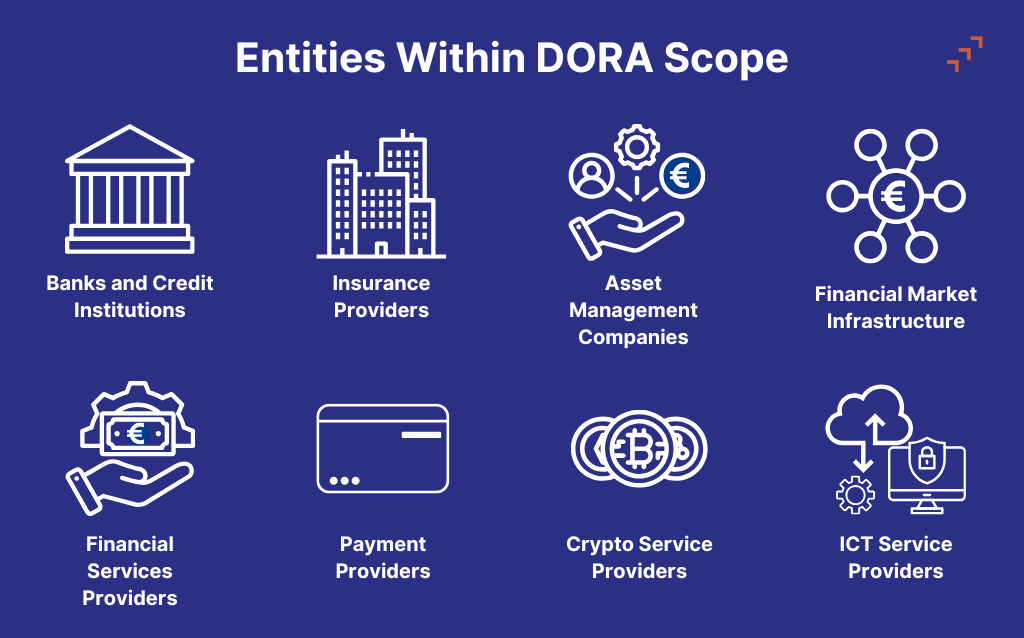
DORA’s Scope: Impacted Entities:
DORA applies to 20 different types of financial entities and their ICT service providers falling under the following categories:
DORA’s Six Pillars Explained:
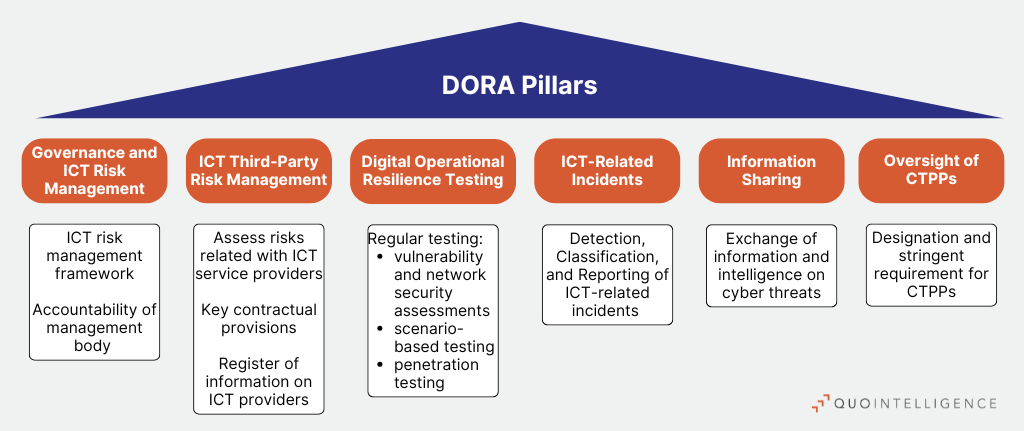
DORA improves digital resilience processes to foster financial entities ability to withstand, respond to, and recover from all types of ICT related disruptions and threats around six pillars:
- Governance and ICT Risk Management: DORA imposes an ICT risk management framework which includes the identification and classification of critical functions, protection and prevention, backup and restoration policies, learning and training, that should be reviewed once a year. Organizations should also identify their critical or important functions and map their assets and dependencies. Notably, DORA foresees that the management body of financial entities is accountable for ensuring ICT risk strategies, policies, and controls.
- ICT Third-Party Risk Management: Financial firms are required to assess risks associated with their third-party ICT service providers, including determining the nature, scare, complexity, and importance of their ICT dependencies and the potential impacts of ICT-related incidents on service continuity and quality. In addition, they have to ensure that their contracts with third parties include mandatory contractual elements set under DORA such as risk management, security, and operational resilience.
- Digital Operational Resilience Testing: The regulation mandates the regular conduct of resilience tests by independent parties, including vulnerability and network security assessments, scenario-based testing, and penetration testing.
- ICT-Related Incidents: DORA requires entities to establish and implement incident management processes to detect, classify, and report any major ICT-based incidents to authorities. Significant incidents must be reported to national regulators and, in some cases, to the European Supervisory Authorities (ESAs). The European Banking Authority has proposed to align the time limits for reporting with NIS2. As such, initial notification should be completed within 4 hours after classification and 24 hours after detection of the incident, 72 hours for the intermediate report, and 1 month for the final report.
- Information Sharing: DORA encourages establishing information-sharing agreements between financial institutions to exchange cyber threat intelligence. This includes tactics, techniques, and procedures (TTPs), and recurrent alerts. Information sharing itself is not mandatory, but financial entities are required to inform regulators on how they participate in information sharing.
- Oversight of Critical Third-Party Providers (CTPPs): DORA foresees the designation of certain ICT providers as critical and subjects them to direct oversight by regulators. CTPPs must meet stringent compliance, resilience, and risk mitigation requirements.
DORA’s Enforcement and Penalties:
Financial entities and CTPPs that fail to meet the regulation’s requirements may face administrative and remedial measures, as well as financial and criminal penalties.
Under DORA, regulators have the authority to:
- Request remedial actions from financial entities and CTPPs.
- Conduct inspections and audits to ensure compliance.
- Issue binding recommendations for rectifying deficiencies in ICT risk management and operational resilience.
- Suspend ICT service agreements or prohibit financial entities from contracting a specific CTPP if risks are not adequately addressed.
DORA foresees financial penalties for non compliance for both financial entities and CTPPs:
- Financial entities can face fines of up to 2 percent of their total annual worldwide turnover. Maximum fine for an individual is set at 1,000,000€
- CTPPs can face fines of up to 5,000,000€ and 500,000€ for individuals. Providers can be fined every day for up to six months until they achieve compliance and up to 1 percent of their average daily turnover worldwide. The competent authorities may publicly disclose DORA breaches, therefore leading to reputational damage for the affected entities.
Additionally, article 52 of DORA foresees the imposition of criminal penalties at the discretion of each member state and in coordination with judicial authorities.
DORA Timeline:
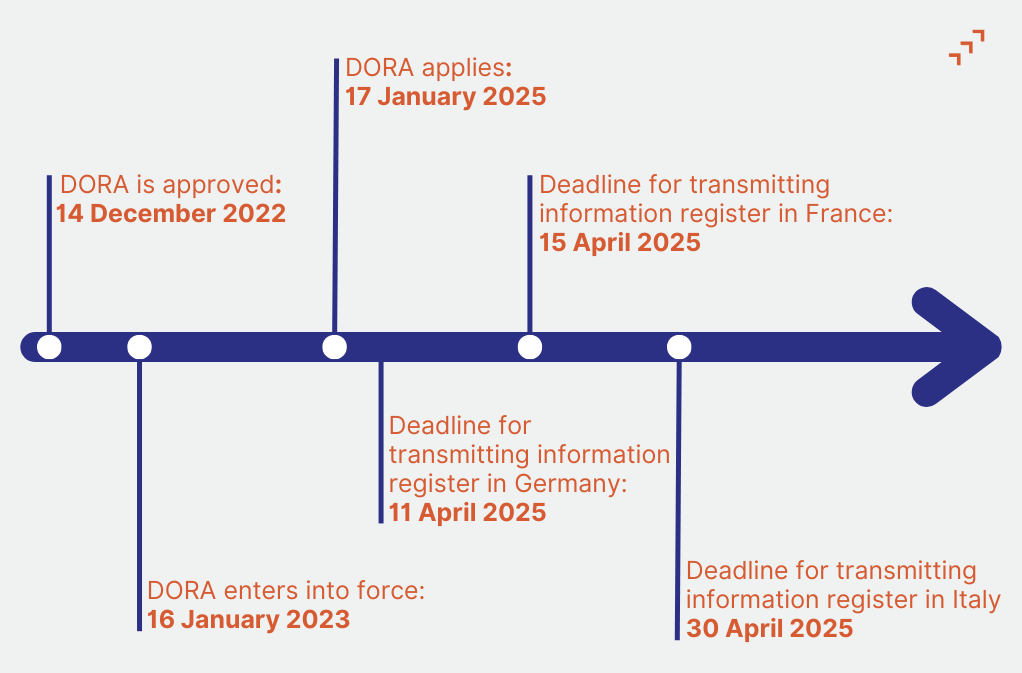
DORA applies to all financial entities in the scope of the regulation since 17 January 2025. Regulators are to start their oversight activities this year. Notably, in the first months of 2025, financial entities need to designate their CTPPs. The European Supervisory Authorities (ESAs) set on 30 April 2025 the deadline for national authorities to report the registers of information on contractual arrangements of the financial entities with ICT third-party service providers. However, some national authorities have established an anticipated deadline for the collection of information register, before transmission to the ESAs. For instance, in France, the Prudential Supervision and Resolution Authority (ACPR) requires French financial entities to handoff their information register by 15 April. In Germany, this process must be done by 11 April. For its part, Banca d’Italia requires financial entities in DORA scope to send all information by 30 April.
QuoIntelligence’s advanced threat intelligence and risk protection services provide financial entities with the insights and tools needed to meet DORA’s stringent requirements.
1. ICT Risk Management
DORA requires financial entities to establish a comprehensive risk management framework to detect, assess, and mitigate ICT-related risks.
How We Can Help:
✅ Threat Intelligence & Risk Intelligence – We provide continuous monitoring and assessment of cyber threats targeting your organization, helping you proactively mitigate risks before they impact operations.
✅ Digital Risk Protection – Our AI-powered intelligence detects exposed assets, such as leaked employees or clients’ credentials and VIP personally identifiable information, allowing you to act swiftly to protect critical systems.
✅ Strategic and Tactical Risk Reports – Our tailored reports offer detailed insights into your organization’s attack surface, threat landscape, and security gaps, enabling informed risk management decisions.
2. Incident Detection, Reporting & Response
DORA mandates financial institutions to establish mechanisms for detecting, reporting, and responding to ICT-related incidents in a timely manner.
How We Can Help:
✅ Continuous Underground Monitoring – Our tools scan for data leaks, credential exposures, and cybercriminal discussions related to your organization.
✅ Adversarial Profiling – We offer in depth analysis of threats, providing context on attacker motives, techniques, and potential impact, allowing for efficient incident response.
3. Third-Party Risk Management
DORA introduces strict requirements for ICT third-party risk management.
How We Can Help:
✅ Supply Chain Intelligence – We provide continuous monitoring of your third-party providers, identifying potential cybersecurity threats and weaknesses before they pose a threat.