Android trojans continue to proliferate and evolve. And the threat nowadays is even more pronounced due to the use of On-Device Fraud (ODF). ODF-capable trojans commit fraud without the need to interact with criminals.

The trojan sends fraudulent transaction requests from the device instead of exfiltrating credentials. These transactions look legitimate to financial institutions, as they come from a previously used device.
These capabilities extend to crypto fraud by replacing destination wallet addresses with the threat actor’s wallets. Android trojans target a multitude of banks and cryptocurrency companies, being spread through the Google Play Store or phishing websites. Once they have infected a device, they take over complete control, hiding from the victim and making it hard to remove them.
Android malware continues to target users throughout Europe, Australia and the US, with Spain, Turkey and Poland being the most targeted countries as noted by Threat Fabric in their 2022 mobile threat landscape update.
One of these trojans, ERMAC, has been observed to be the third most active during the second quarter of 2022. ERMAC’s functionality includes several advanced techniques to target cryptocurrency owners, but is also able to capture credentials from over 400 banking applications and circumvent Multi-Factor Authentication, making it one of the most dangerous Android threats currently in circulation.
QuoIntelligence came across a post on Twitter by @malwrhunterteam detailing a supposedly malicious apk.
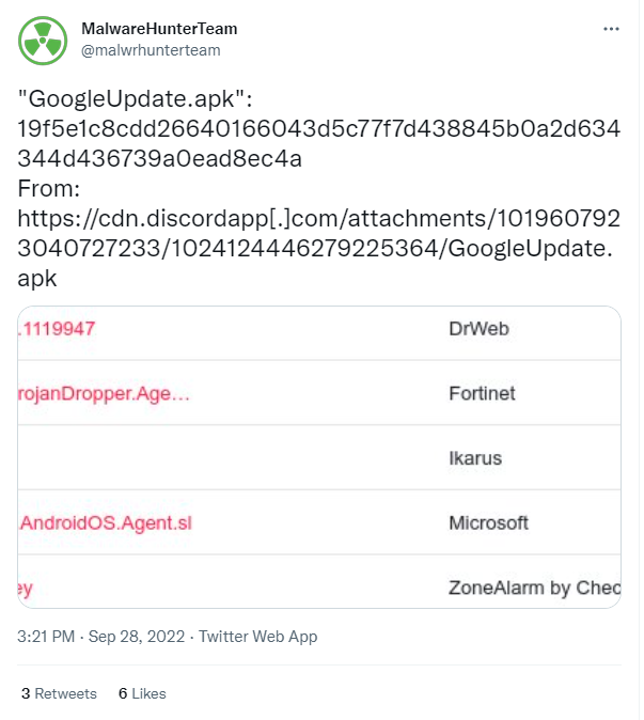 Figure 1: MalwareHunterTeam Tweet
Figure 1: MalwareHunterTeam Tweet
Want to read more on this and other stories? Subscribe to our newsletter to access the complete Weekly Intelligence Snapshot. Don’t miss out on more intelligence!

On further analysis, this Android application turned out to be a slightly updated version of ERMAC 2.0 as described by Intel471 and Cyble. ERMAC 2.0, like its predecessor ERMAC, is based on Cerberus; however, it now implements several advanced functionalities, an updated communication protocol, and several new commands for added control.
Targeting over 400 banking applications using webfakes, ERMAC 2.0 has advanced functionality to circumvent multi-factor authentication (MFA), be it over SMS, email, or dedicated MFA apps. These come in the form of commands that ERMAC 2.0 implements.
Functionality overview
ERMAC 2.0 comes with a dedicated panel to control the bots that also function as a C2 server.
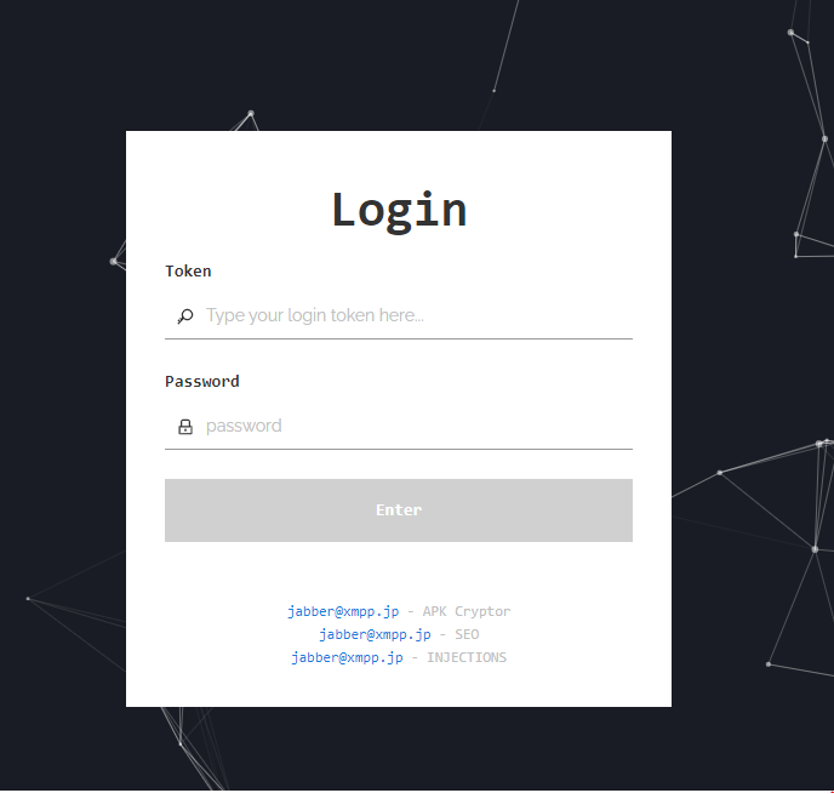
Figure 2: ERMAC 2.0 Admin Panel login page
Upon installation of the malicious apk, ERMAC masquerades as Chrome Update.
When victims open the application, ERMAC asks for accessibility services under the guise of needing this to install the update.
ERMAC includes functionality to mimic several legitimate applications, these include Telegram, Facebook, Instagram, Chrome, YouTube, WhatsApp, Contacts, Gmail, Google Play and TikTok. While the text contained in this analyzed application was originally in Turkish, ERMAC uses Google Translate to transpose the text with the translated one, based on the victim’s language. The application will bombard the user with notifications and take them back to the accessibility services screen until they accept.
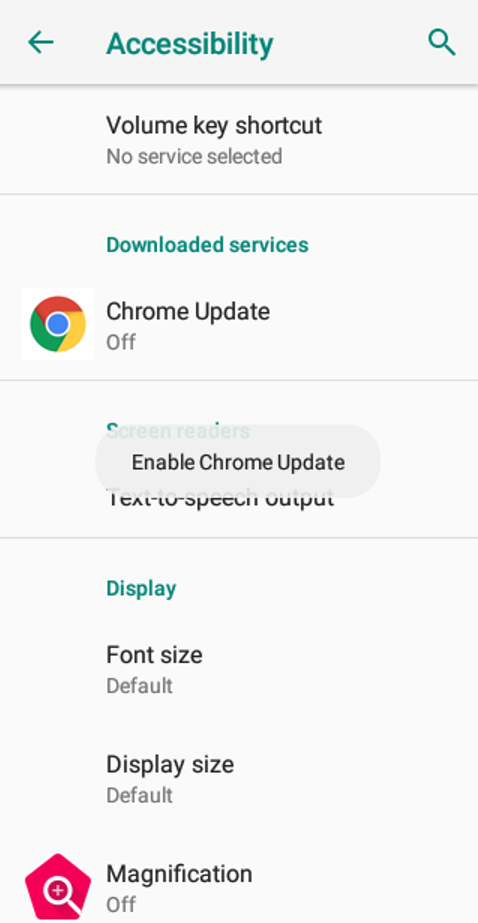
Figure 4: Accessibility Services permissions
As soon as the victim enables the accessibility services for ERMAC, the trojan no longer needs user interaction and will give itself the permission it needs. It also removes its icon, in this case the Google Chrome icon, from the home screen and will prevent the victim from uninstalling the app through settings by exiting every time the settings app is opened.
Technical analysis
Banking fraud functionality
ERMAC’s main functionality consists of overlay attacks on targeted banking applications. When an infected victim opens a banking application, ERMAC retrieves the associated web fake, an HTML page, and displays it to the victim. Once the victim has entered their banking credentials, ERMAC exfiltrates these to the attacker. These web fakes masquerade as the legitimate application. Example overlays are presented below:
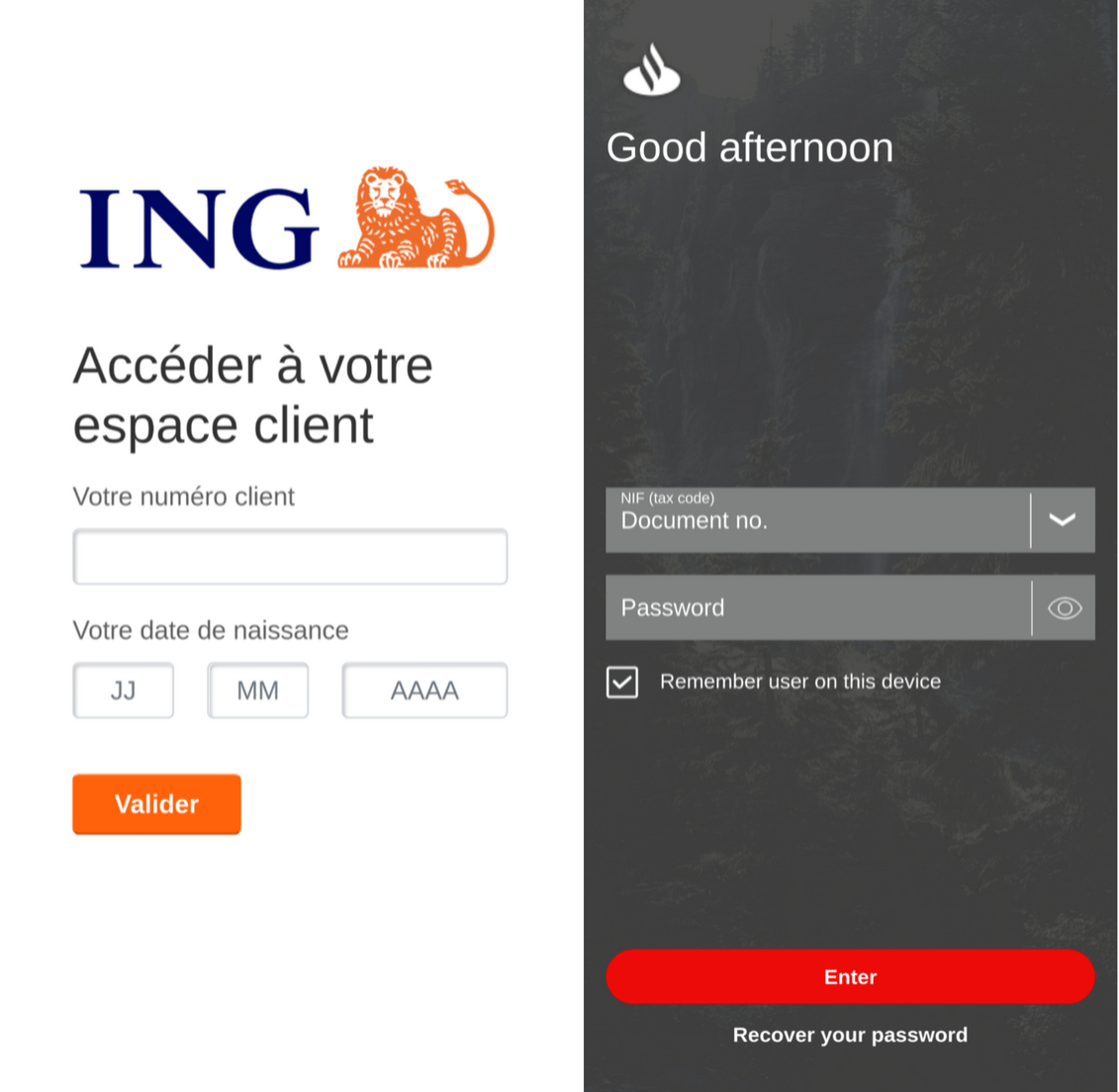
ERMAC mimics banking apps perfectly
Due to the widespread adoption of MFA, ERMAC 2.0 has implemented several measures to circumvent it. These include capturing SMS messages containing the one-time password (OTP), extracting emails asking for confirmation and even grabbing OTPs from the Google Authenticator app. ERMAC will also recognize when an Ethereum or Bitcoin address is saved in the clipboard (ie copied) and will replace it with one of two set addresses that belong to the threat actor’s wallets.
- Bitcoin address: bc1ql34xd8ynty3myfkwaf8jqeth0p4fxkxg673vlf
- Ethereum address: 0x3Cf7d4A8D30035Af83058371f0C6D4369B5024Ca
Commands
ERMAC implements several commands that the threat actor can use to control the infected device. These are divided into settings that change the behavior of the trojan and commands that are one-off actions.
The implemented settings are:
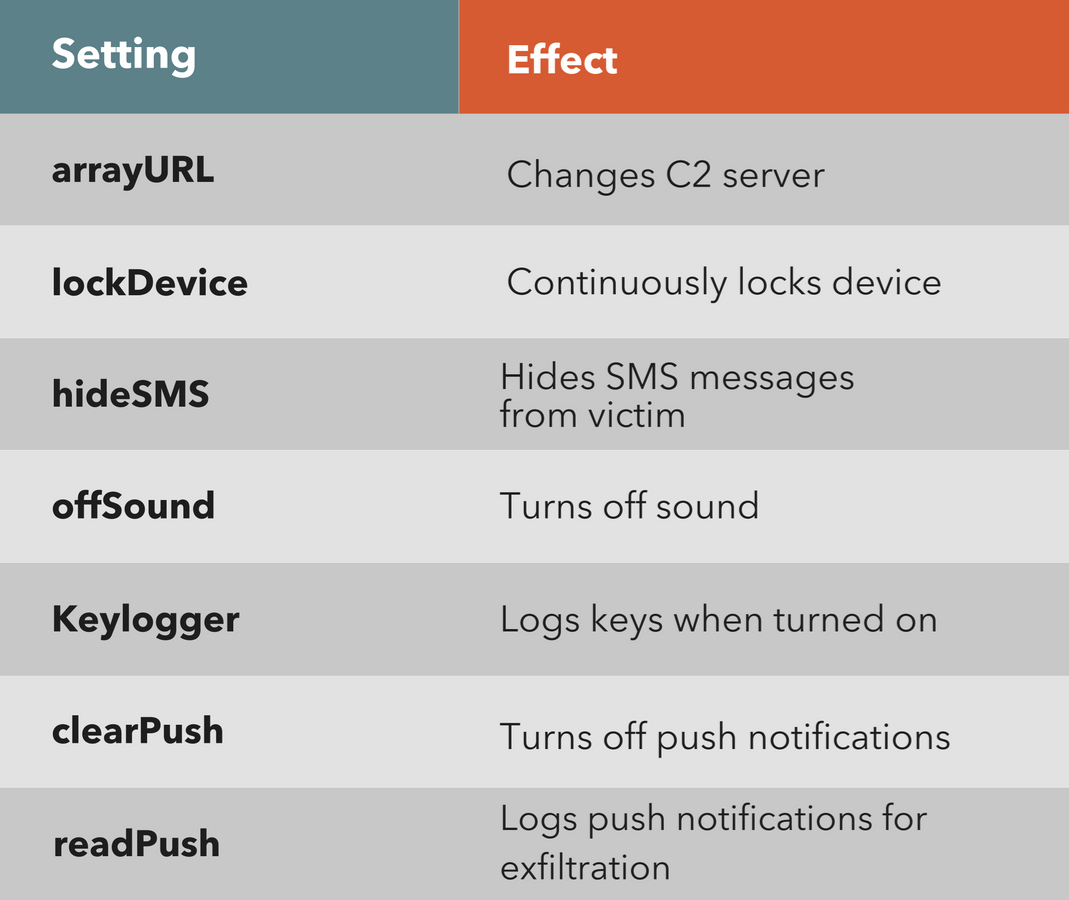
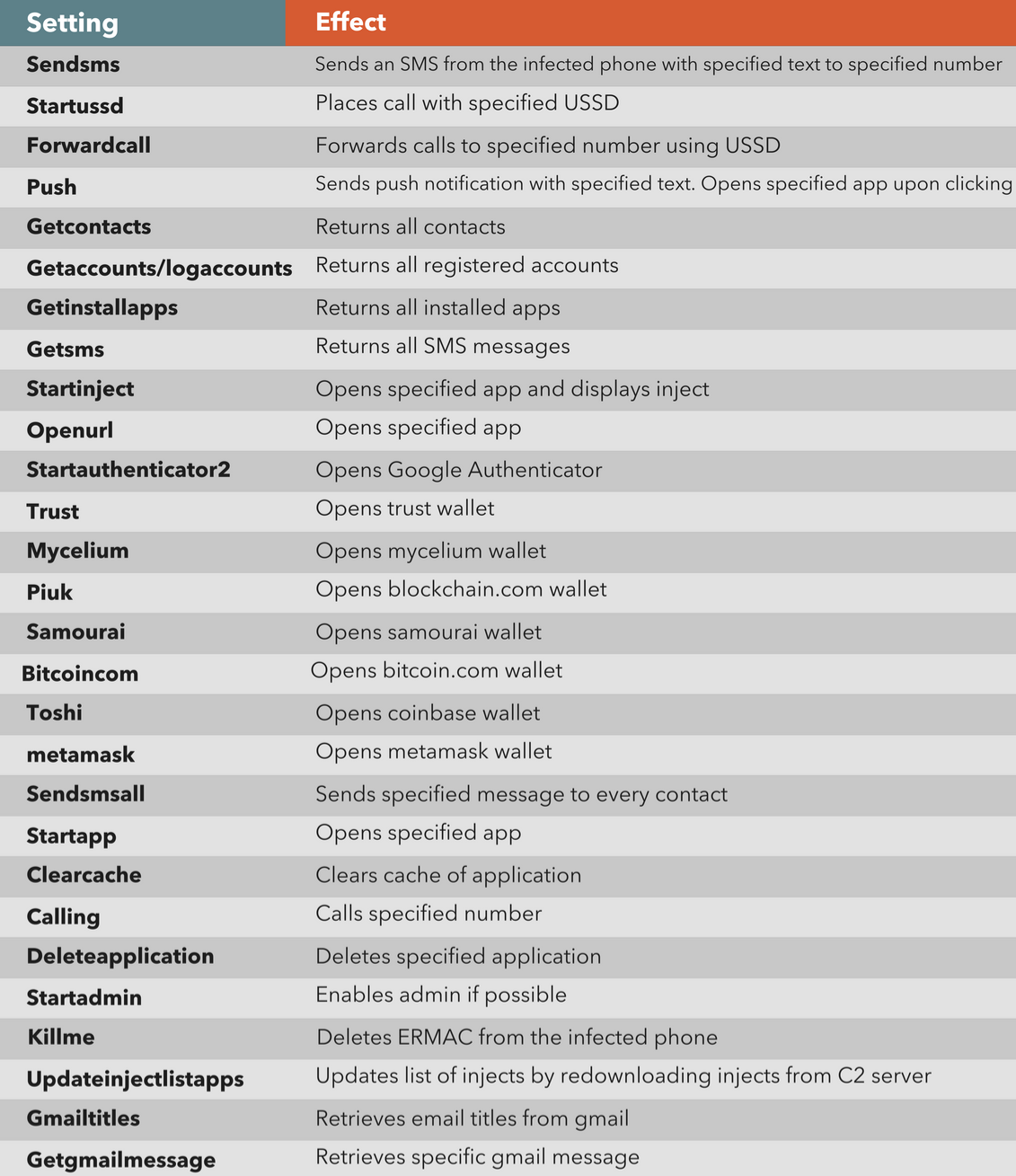
The implemented commands are:
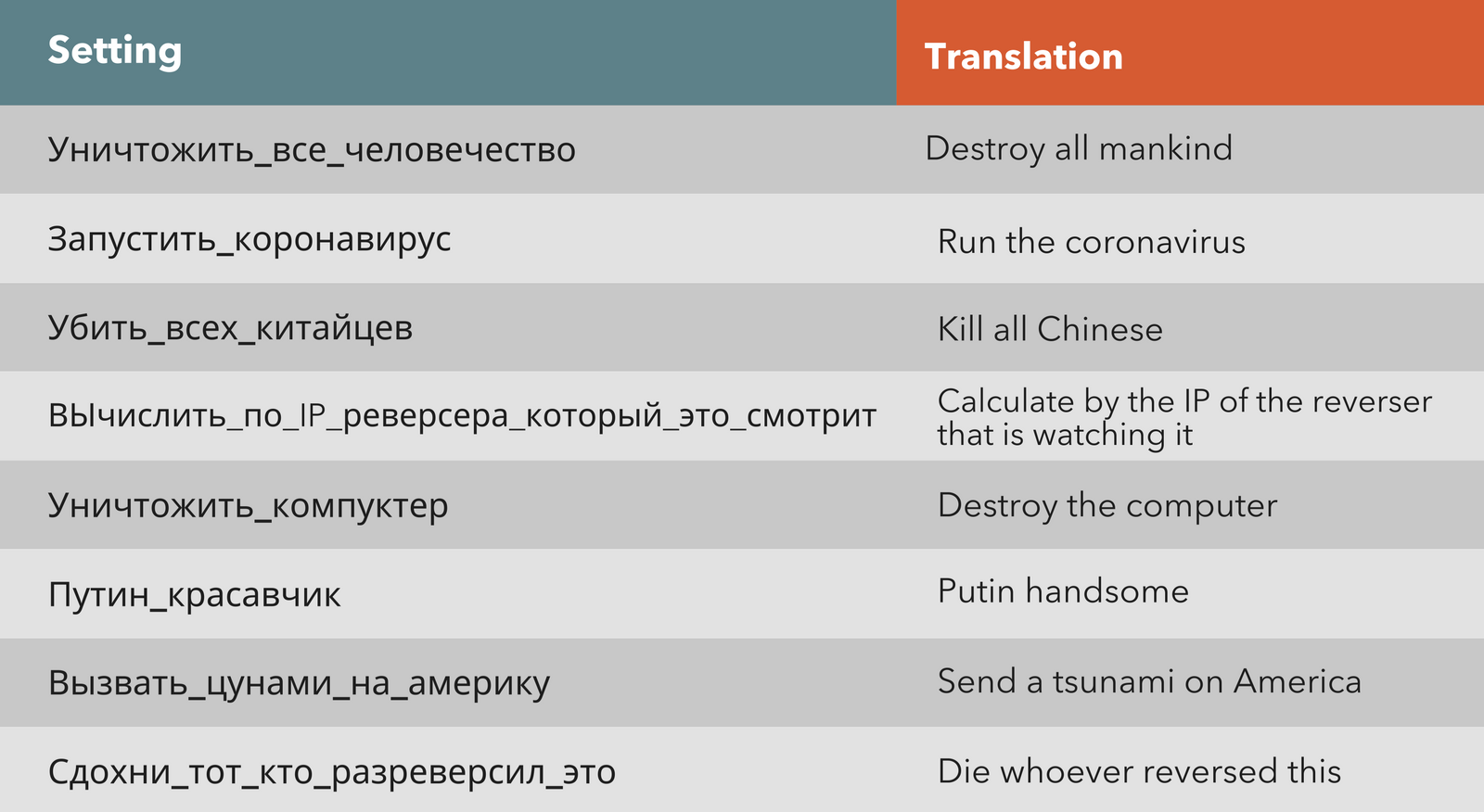
ERMAC 2.0 also includes a set of 8 commands in Russian language that have no functionality, but can help with profiling malware samples:
Communication
ERMAC 2.0 employs symmetric encryption to obfuscate its communication with the C2 server. The base payload is usually json. The registration payload looks like this:

This payload gets encrypted using AES-CBC with 1A1zP1eP5QGefi2DMPTfTL5SLmv7Divf as key and 0123456789abcdef as IV, base64 encoded, and sent to the C2 server on any .php endpoint using a POST request. Answers from the C2 server are encrypted in the same way.
Analysis
ERMAC’s capabilities in relation to MFA circumvention only fall short when it comes to allowing transactions through push notifications or specific external applications. Since many banking applications have this setup turned on by default, ERMAC might evolve in a way to automatically approve these requests, taking over the entire transaction process.
The developers of ERMAC have established a fleshed-out product that they can rent to criminals that don’t want to program their own trojan. The ecosystem that ERMAC provides – panel and trojan – constitutes one of the most sophisticated setups on the market today and the active support that they provide could make it the best choice for criminals wanting to enter the mobile banking fraud scene. Furthermore, malware binaries are packed, which leads to lower detection rates by antivirus engines.
- QuoIntelligence recommends not to download mobile applications from untrusted sources as ERMAC relies on unsuspecting victims downloading it from fake browser update websites and mimicking legitimate apps
- While ERMAC has not been observed being distributed through official mobile application stores, caution needs to be taken when installing applications asking for extensive permissions. When banking, make sure to only use the official applications and check with your bank if you have any doubts
- Lastly, unless you need it, never activate Accessibility Services as this will give an application full access to your device

Appendix
IoCs
Applications:
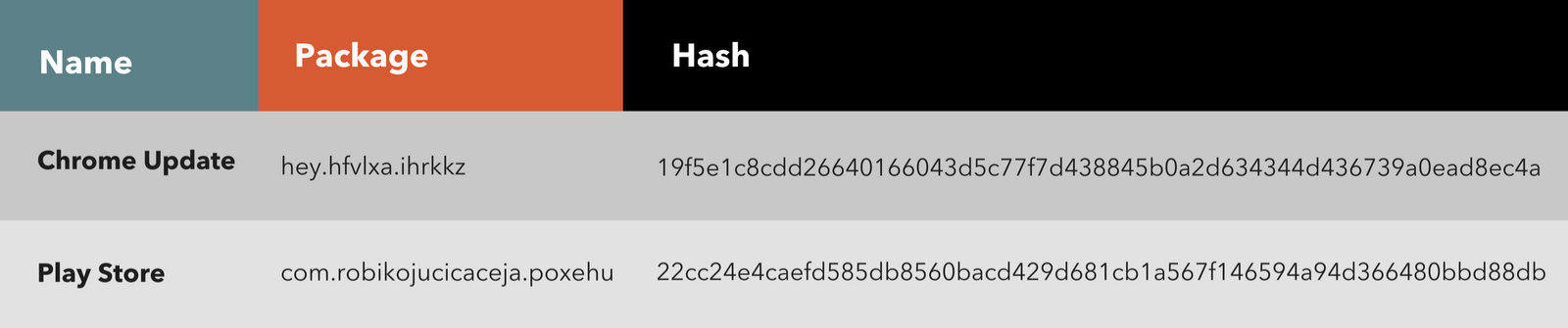
Network:
http://193.106.191.116:3434/
http://193.106.191.116/
Mitre Attacks:
- T1456: Drive-By Compromise
- T1624.001: Broadcast Receivers
- T1626.001: Device Administrator Permissions
- T1628.001: Suppress Application Icon
- T1628.002: User Evasion
- T1629.001: Prevent Application Removal
- T1629.002: Device Lockout
- T1630.001: Uninstall Malicious Application
- T1516: Input Injection
- T1406.002: Software Packing
- T1517: Access Notifications
- T1417.001: Keylogging
- T1417.002: GUI Input Capture
- T1418: Software Discovery
- T1426: System Information Discovery
- T1616: Call Control
- T1636.003: Contact List
- T1636.004: SMS Messages
- T1409: Stored Application Data
- T1437.001: Web Protocols
- T1521.001: Symmetric Cryptography
- T1509: Non-Standard Port
- T1646: Exfiltration Over C2 Channel
- T1582: SMS Control
Want to read more on this and other stories? Subscribe to our newsletter to access the complete Weekly Intelligence Snapshot. Don’t miss out on more intelligence!
QuoIntelligence uses phrases such as we judge, we assess, and we estimate — and probabilistic terms such as probably and likely — to convey analytical assessments and judgments. Such statements are not facts, proof, or knowledge. In addition to conveying judgments rather than certainty, our analysts’ estimative language also often conveys our assessed likelihood or probability of an event.


