QuoIntelligence expects cyber extortion to take innovative forms, AI to be at a crossroads, and geopolitics continuing to shape the threat landscape and global economy in 2024.
In early 2023, we released our annual outlook, in which we forecasted that the specialization and professionalization of eCrime would lead to better ransomware proliferation. We also predicted that the polarization of international relations would impact the cyber threat landscape, resulting in new state-sponsored cyber operations. These trends were particularly prevalent throughout 2023 and we expect them to continue this year.
Looking ahead to 2024, QuoIntelligence predicts that threat actors will evolve their tactics, techniques, and procedures (TTPs) to widen extortion efforts and bypass security measures with LockBit remaining the most prolific ransomware group in 2024. QuoIntelligence also anticipates 2024 to be a pivotal year for artificial intelligence (AI), encountering fresh security and legal hurdles. Moreover, the upcoming elections and escalating geopolitical tensions are likely to shape the threat landscape and impact global supply chains. Rising cyber and geopolitical threats, along with climate change, are in turn confronting policy holders with new challenges.
Ransomware continues to be the most critical threat for businesses, with emerging groups and further specialization of the ransomware value chain.
The externalization and specialization of the different stages of ransomware attacks, as well as leaked source code from LockBit but also HelloKitty ransomware continued to fuel the proliferation of ransomware groups throughout 2023. As such, novice ransomware operatives and new variants are increasing, with a direct impact in the number of ransomware attacks. Smaller entities and local administrations are now the focus of established and emerging groups.
In line with the specialization of the ransomware value chain, Initial Access Brokers (IABs) work now directly for – or in collaboration with – ransomware groups, handing off any relevant information about potential victims that satisfies their affiliates’ requirements. Some groups are also developing Ransomware-as-a-Services (RaaS) affiliation programs, proposing fully integrated solutions with a botnet providing access to already breached corporate networks. This system increases efficiency and speed of ransomware operations.
Dual ransomware attacks are on the rise.
These two business models are likely behind the emerging trend of dual ransomware attacks, which involves two or more ransomware variants targeting the same victim in a short span. In fact, it is suspected the ransomware affiliates obtained stolen credentials from IABs or other operatives in the ransomware value chain. In 2024, we expect that the number of operatives in the ransomware value chain will continue to grow, along with their TTPs to increase the efficiency and profitability of their business models.
eCrime actors to develop new sophisticated strategies to extort victims.
QuoIntelligence has also observed a growing trend of multi-point extortion ransomware attacks, with threat actors using several methods to pressure victims into paying the ransom. Notably, ransomware affiliates leverage data protection legislations, such as the EU’s General Data Protection Regulation (GDPR), to threaten victims with fines if they do not pay the ransom and the victims’ data is leaked. Similarly, in November, BlackCat/ALPHV ransomware group lodged an SEC complaint against MeridianLink, alleging failure to disclose a recent data breach. Other extortion techniques reported last year were based on knowledge of insurance coverage and swatting. Ransomware groups will likely continue to refine their extortion methods throughout 2024, with new ways to pressure victims into paying ransoms.
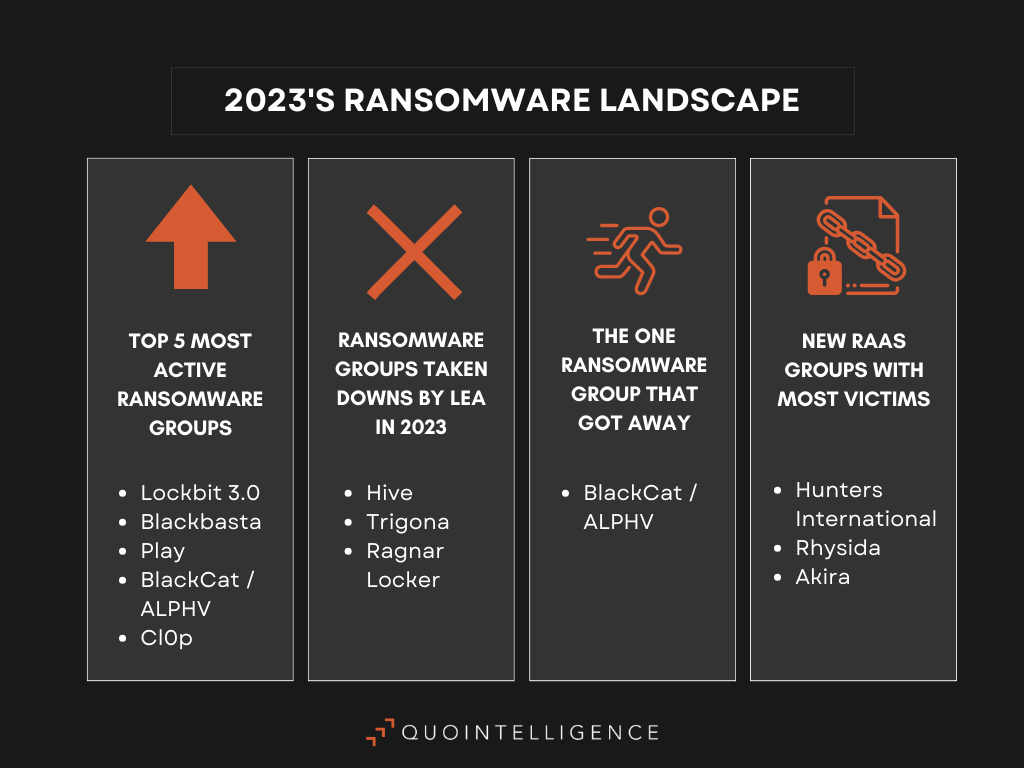
Major Law Enforcement Agencies (LEAs) takedowns and migrations to alternative platforms.
In multiple coordinated international operations throughout 2023, law enforcement agencies (LEAs) have successfully disrupted various cybercrime operations and services. Key ransomware groups and RaaS models such as Hive, Trigona, and Ragnar Locker were effectively neutralized. However, the FBI’s initial seizure of BlackCat/ALPHV group was circumvented by the cybercriminals and their affiliates, who promptly established mirrored websites to continue their activities. Similarly, the takedown of QakBot (Malware-as-a-Service) and the notable BulletProof (Phishing-as-a-Service) platform led to a migration of their clientele to other services like Greatness and EvilProxy. Additionally, the underground carding forum Genesis Market and the forum BreachForums were dismantled through a collaborative effort of multiple LEAs. Despite these successes, we are observing that the affected users and clients are transitioning to alternative platforms, adjusting their techniques as needed in response to law enforcement actions.
Zero-day exploits, supply chain compromises and strategic recruitment reshape the ransomware threat landscape.
Throughout 2023, the LockBit ransomware group maintained its status as the most active ransomware threat and we anticipate its dominance to continue into 2024. Following the FBI’s disruption of BlackCat/ALPHV ransomware group, we observed LockBit strategically recruiting BlackCat/ALPHV affiliates to leverage their advanced technical skills, thereby enhancing LockBit’s operations. While the impact of Cl0p and BlackBasta ransomware groups on the threat landscape is less pronounced compared to that of LockBit, their use of zero-day exploits and supply chain attacks to target a broad range of victims was evident throughout 2023, a strategy that will most likely persist, if not increase, in 2024.
Malware-as-a-Service (MaaS) providers focusing on versatility and obfuscation techniques.
In line with the specialization of the attack chain, for 2024 we expect MaaS providers to continue to refine their functionalities to adapt to their users’ needs. Additionally, MaaS groups are providing their services at a cheaper rate, allowing new entry-level threat actors to start their own illicit businesses. As we anticipated, new services emerged in 2023, with information stealers consolidating their position as a prominent threat. Notably, several information stealer variants discovered in 2023, such as Akira Stealer, have enhanced obfuscation features to remain undetected for as long as possible.
Living-off-the-Land Binaries (LOLBINs) and signed drivers to be increasingly exploited for malicious activities.
We forecast that the use of Living-Off-the-Land Binaries and signed system drivers to circumvent security protocols and facilitate privilege escalation will become prevalent in all future attack chains. Natively pre-installed on every Windows device, they allow system administrators and the operating system itself to carry out maintenance and low-level administrative tasks. As such they are the perfect tools to be misused by attackers. Due to their frequent usage for standard operations and routines performed by operating systems, their abuse will significantly complicate detections faced by analysts and automated systems. Moreover, the elevated privileges required to execute certain binaries provide adversaries with opportunities to exploit these for privilege escalation, thereby enabling the execution of malicious commands or files with high system privilege.
In October 2023, Microsoft announced the complete deprecation of Visual Basic Script (VBS) in future releases of key applications like Excel, PowerPoint, and Word. This decision is likely to push threat actors to explore alternative methods for infection and execution within Windows environments.
Companies will eventually be impacted by a supply chain attack.
Data breaches have repercussions extending beyond the directly impacted organization, posing risks to their supply chains. Given these extensive repercussions, adversaries are progressively focusing on suppliers by exploiting the trust their partners place in them, representing 22 percent of the documented compromise methods used last year. 2023 was marked by several high-profile supply chain attacks. Notably, the mass-exploitation by the Cl0p ransomware group of the MOVEit file transfer software to deploy ransomware to their clients affected more than two thousands victims. North Korean hackers were behind the first ever reported double supply chain attack on internet telephony service provider 3CX, in which attackers successfully infected 3CX by previously compromising their supplier, allowing them to infect customers with a hidden and malicious update. The recent breach affecting the access and identity management giant Okta is also striking because it allowed attackers to access every information about Okta’s customers to be used in spear-phishing attacks.
2024: A Pivotal Year for AI, Navigating Threat Actor Exploits and Legal Turmoil.
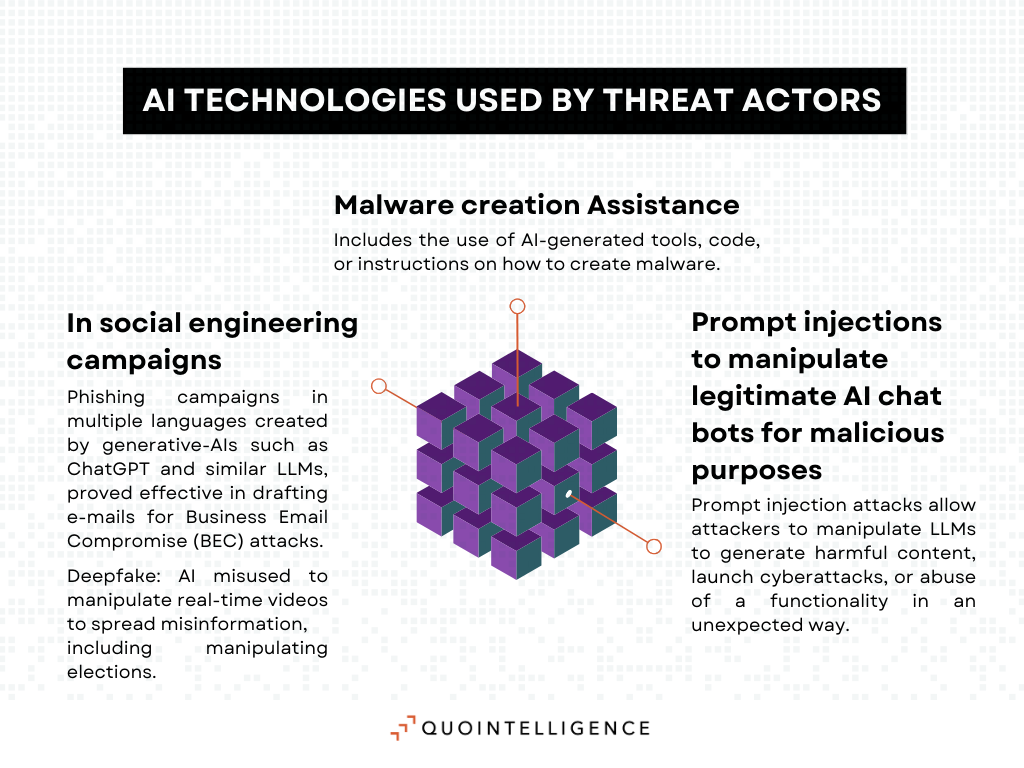
While 2022 was marked by the emergence of widespread generative AI chatbots, 2023 saw the multiplication of controversies over security risks and copywrite issues posed by AI technologies. Social engineering campaigns have benefited the most from generative AI, as threat actors use AI platforms to create deep fake, generate phishing campaigns in multiple languages, and automate conversations in parallel at speed and scale.
Cybercriminals also leverage large language models (LLMs) to support malicious operations. WormGPT is the most notable example of this trend. Accessible on the Dark Web, this AI chatbot is based on the GPTJ language model and has no ethical or legal safeguards. It has proved effective in drafting e-mails for Business Email Compromise (BEC) attacks, while also providing assistance in the creation of malware. Threat actors also manipulate legitimate AI chat bots through prompt injections to generate harmful content, launch cyberattacks, or abuse a functionality in an unexpected way. Researchers have extensively theorized the possible use of AI technologies for malicious purposes, but knowledge about their actual use by threat actors remains limited. In 2024, we expect the CTI community to uncover novel ways in which malicious actors are exploiting AI in offensive operations.
The spread of generative AI tools into business environments has posed new challenges for companies exposed to data privacy and confidentiality issues. In May 2023, Samsung banned the use of AI platforms after engineers accidentally leaked internal source code by uploading it to ChatGPT. Major tech and financial companies, such as Amazon, Apple, or Deutsche Bank, followed the move.
Generative AI tools raise copyright concerns, including AI-generated work ownership, using copyrighted content in training data without license, and user rights to use copyrighted and trademarked works without creator consent. Multiple lawsuits were filed throughout 2023 against major AI service providers, with the most notable lawsuit filed by the New York Times against OpenAI and Microsoft for unauthorized use of the newspaper’s articles to train their AI technologies. Judges in the US are expected to hear and decide on some of these cases in 2024. Rulings and new copyrights legislation will weigh heavily on the future of AI technologies and the emerging industry that stems from them.
Geopolitics and elections are likely to be catalysts for the evolution of the cyber threat landscape in 2024.
As we anticipated in last year’s blog, geopolitical tensions worldwide continued to translate into activity in the cyberspace throughout 2023. Pro-Russia hacktivist groups continued to carry out DDoS attacks against Western entities in the framework of the war in Ukraine. The hacktivism landscape was also marked by the conflict opposing Hamas and Israel. TTPs of hacktivists groups operating in this content are similar to those of pro-Russian groups, but with little to no impact on European organizations.
Information operations to promote selected narratives were on the rise last year. Notably, researchers discovered that the hacktivist group Anonymous Sudan was likely created in the framework of a Russian information operation to destabilize Sweden by hindering Turkey’s approval for Sweden’s NATO application.
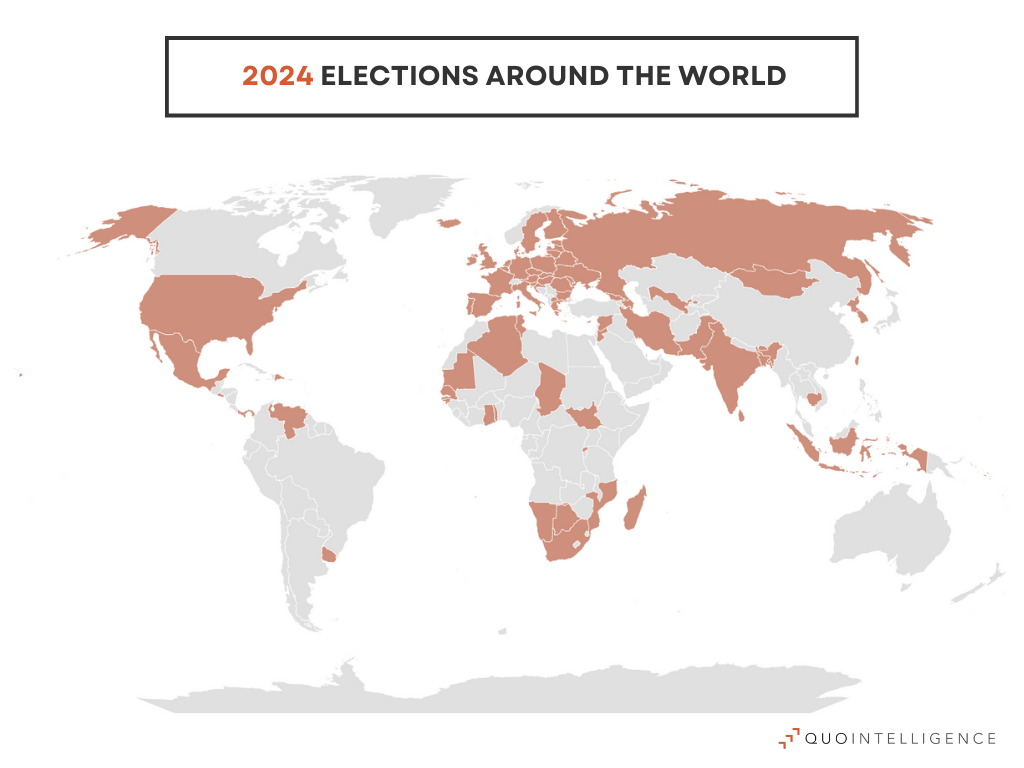
With more than 60 elections around the globe in 2024, information operations are likely to grow significantly this year. We expect threat actors engaged in information operations to leverage AI technologies in electoral contexts. Notably, deepfakes can be used to manipulate real-time videos and spread misinformation. Additionally, elections in Taiwan, Russia, South Korea, and the US are likely to fuel the politization of the threat landscape, with some outcomes possibly affecting alliances and power balance.
Continued support by Russia-Nexus groups in the Ukraine conflict.
In 2023, Russia-nexus activities continued to be impacted by the war in Ukraine and related targeting. In June, Microsoft identified a new activity group associated with Russia’s military intelligence dubbed Cadet Blizzard. The group is responsible for a range of destructive operations in the framework of the war in Ukraine, including wiper deployments. Cadet Blizzard is also likely behind the breach of IT services providers in Europe for the purpose of intelligence gathering. Notably, the group engages in long term operations, maintaining access for months and exfiltrating data prior to disruptive actions. In general, last year, Russian nexus groups conducted operations against Ukraine and NATO members, with government and NGO entities being their primary targets, followed by education, IT, and intergovernmental organizations. As the war in Ukraine drags on, this line of targeting will remain to support Russia’s kinetic efforts on the ground and its intelligence needs.
China nexus activity to mirror Beijing’s geopolitical ambitions in 2024.
As QuoIntelligence predicted in 2023’s outlook, tensions in Asia have escalated over the past year, with China being particularly aggressive in asserting its territorial claims in the South China Sea. This translated into cyber campaigns targeting multiple Asian countries as well as the US to collect intelligence and support Beijing’s global influence goals. Most notably, Volt Typhoon group conducted operations against communication infrastructure on Guam, a key logistical hub for US military operations in the Pacific. Europe has not been spared by Chinese cyber operations as Mustang Panda continued to target European governmental organizations for intelligence collection. Further targets also included China’s partners involved in the Belt and Road Initiative. A notable trend is the targeting of telecoms companies, probably to gain vantage points allowing persistent collection and direct access to telecommunication infrastructure. As such, governmental organizations and telecoms operators in Asia, the US, and Europe are most at risk from China-Nexus group activities in 2024.
Additionally, sophisticated groups are more often exploiting edge devices to maintain foothold in the environment and covertly hide communications with attackers. Edge devices, such as Endpoint Detection and Response (EDR) agents, are commonly preferred targets due to the lack of security applications and coverage. Their exploitation enables increased dwell times and more resilient operation setup.
Global shipping to navigate through escalating geopolitical tensions affecting key waterways.
Geopolitics have taken a hit on global shipping last year, with Yemen’s Houthis rebels persistently targeting merchant vessels in the Red Sea since November 2023. Amid the war in Gaza, the movement backed by Iran is using its strategical position on the Bab-el-Mandeb strait to leverage global shipping and put pressure on Israel’s allies. The degradation of the security situation in the Red Sea and Arabian Sea has led major shipping companies to avoid the waterway to the Suez Canal to instead sail around Africa. This route is significantly longer, incurring higher fuel costs and delays. Since 12 percent of world trade usually passes through the Suez Canal, global supply chains are taking a rough hit. As the crisis drags on, surge in ocean freight rates will likely impact industrials, retailers, and finally end buyers.
Further escalation cannot be ruled out, as Iran appears eager to get directly involved, with a possible risk to oil and liquefied natural gas (LNG) supply transiting though the Gulf of Oman. The Houthis are now playing a strategic role in the geopolitics of the Middle East. They will probably continue to take advantage of this new status in the future in the context of the Israeli-Palestinian conflict, but also for other crises affecting the region. Additionally, the example set by Houthis’ attacks on merchant vessels could influence other armed groups or movements located on other strategic waterways.
Growing cyberthreats, geopolitical unrest and climate change will pose unprecedented challenges for policyholders in 2024.
Since 2020 insurers significantly increased premiums for cyber insurance coverage, catching up with the rising number of cyberattacks. High cost cyberattacks have also led insurers to introduce expansive exclusions. In fact, a growing number of insurance companies are considering that the cyber risks for critical infrastructure are too large to be insurable. Insurance policies also generally exclude coverage for losses that arise from war-related activities. In the context of cyber insurance, insurers have invoked such restrictions to argue that state-sponsored cyberattacks are not covered under their policy. However, in May 2023, the New Jersey Superior Court ruled that Merck’s insurance must cover NotPetya cyberattack damages as the insurer failed to prove that the attack qualified as a warlike action. This ruling led insurance companies to tighten their policy by excluding state-sponsored cyberattacks from their coverage.
Insurance coverage for physical threats faces a similar issue. Following the Russian invasion of Ukraine, insurers were confronted with the growing risk of physical attacks on businesses leading them to reconsider the extent and scope of their covers in potential conflict zones. The outburst of the Hamas-Israel crisis in October last year has deepened this dynamic. Similarly, climate change is worsening the risk of extreme weather events, causing premiums to rise. In California, the largest home insurance company in the state stopped selling coverage to homeowners altogether.
As 2024 is set to be an election year, defined by geopolitical stakes, insurance premiums in regions facing diplomatic tensions are likely to remain high. Similarly, policyholders can expect a continuous increase in cyber insurance premiums.
Here are QuoIntelligence’s main takeaways for 2024:
- e-Crime in 2024: Bracing for advanced extortion tactics and a surge in victims. Ransomware groups will develop new tactics for broader extortion, exploiting data protection laws, insurance coverage, or any relevant factors to pressure victims into paying, while also resorting to dual ransomware and supply chain attacks to reach more victims. The use of zero-day exploits and supply chain attacks will likely continue to target a broad range of victims.
- Malware evolution: Refining functionalities and enhanced features to avoid detection. MaaS providers are likely to continue to refine their functionalities and provide services at a cheaper rate, in addition mew info stealer variants with enhanced features to avoid detection will appear. Living-Off-the-Land Binaries and signed system drivers will likely circumvent more often security protocols and help privilege escalation.
- Increase in offensive use and legal hurdles to shape AI in 2024. We anticipate an escalation in the misuse of AI technologies for offensive purposes, as threat actors increasingly adopt AI tools in their kill chain process. Concurrently, the AI sector will face legal hurdles, particularly concerning copyright issues. These challenges will test the boundaries of AI technologies development and use.
- Tense geopolitical climate impacting cyber space and global economy. Key elections, along with increasing geopolitical tensions among great powers, are set to influence the overall threat landscape this year. We anticipate this scenario to result in more state-sponsored activity, including information operations, and to affect the global economy with significant ripple effects on supply chains and insurance. Finally, sophisticated groups will likely exploit edge devices more often.
Keep up to date
To keep up with the latest cyber and geopolitical threats, subscribe to QuoIntelligence’s Weekly Intelligence Newsletter, published every Thursday around 1900 CET.





