THREAT INTELLIGENCE, RELEVANT TO YOU
AI-Powered Intelligence as a Service, Enhanced by Expert Analysts, Delivering Tailored Insights on Threat Actor Tactics, Techniques, and Procedures (TTPs), Indicators of Compromise (IoCs), and Vulnerability Alerts. Gain insights into emerging threats, vulnerabilities, and attack methods, empowering decision-makers to stay informed and reduce the risk of compromise
Cyber and Geopolitical Threat Intelligence tailored to your unique needs
Threat Intelligence as a Service: Why Choose Our Services?
Tailored Threat Intelligence
Receive insights customized to your industry, region, and technology stack, always through a European lens, reflecting the unique regulatory, geopolitical, and cyber threat landscape of Europe
Proactive Threat Management
Get early warnings and strategic advice to monitor cyber threats and predict supply chain cyber attacks before they affect your organization
Expert Support
Our team combines Sovereign AI Technology with industry expertise and leverages Generative AI in Threat Intelligence to handle the complexities of threat intelligence for you, ensuring trusted, context-rich insights tailored to your needs
Talk to Our Experts Today to learn how our tailored threat intelligence can enhance your security posture and protect your business from evolving threats
Actionable Insights
Curated Intelligence Reports for Proactive Decision-Making
Our service goes beyond basic data feeds by providing curated reports that offer actionable insights. Our intelligence reports are designed to help you make informed decisions, addressing the specific needs of your organization
Expert Analysis
Holistic Intelligence with Economic, Social, and Geopolitical Focus
Our intelligence analysis incorporates a wide range of contexts, including economic, social, and geopolitical factors. This holistic approach ensures that you receive a thorough understanding of the threats and opportunities affecting your organization
Noise reduction
Focus on Relevant Threats with Effective Noise Reduction
Our intelligence services prioritize relevant threats, significantly reducing noise and allowing your team to save time and resources. This targeted approach ensures that you can concentrate on addressing the most critical security issues

Threat Intelligence
Our Finished Threat Intelligence combines data from open and closed sources, refined by intelligence experts to deliver actionable recommendations. QuoIntelligence analysts consider the entity and its economic, social, and geopolitical contexts, ensuring you’re prepared for any threat
Manage Information Overload: Filter out irrelevant data, focusing on threats that matter
Quick Response: Prevent breaches with early detection and actionable recommendations
Skilled Support: Access top-tier threat intelligence experts without the need for in-house teams
Scalable Cyber Resilience: Implement cost-effective, scalable strategies to combat rising cyber threats
Threat Intelligence
Our Finished Threat Intelligence combines data from open and closed sources, refined by intelligence experts to deliver actionable recommendations. QuoIntelligence analysts consider the entity and its economic, social, and geopolitical contexts, ensuring you’re prepared for any threat
Manage Information Overload: Filter out irrelevant data, focusing on threats that matter
Quick Response: Prevent breaches with early detection and actionable recommendations
Skilled Support: Access top-tier threat intelligence experts without the need for in-house teams
Scalable Cyber Resilience: Implement cost-effective, scalable strategies to combat rising cyber threats
The Benefits of investing in Threat Intelligence
In 2022, the world would produce and consume 94 zettabytes. That is almost unimaginable data, which will only compound with the rise of the number of Internet of Things connected devices.
The total amount of data created, captured, copied, and consumed globally is forecast to increase rapidly. Over the next five years up to 2025, global data creation is projected to grow to more than 180 zettabytes.
Our Threat Intelligence allows you to filter out the noise and focus on what is relevant to your organization.
By being aware of which threats are targeting your organization and threat actor tactics, compared to weaknesses within your organization, you are able to prioritize your time and resources on mitigating threats that directly impact you
In 2023, the share of organizations experiencing a shortfall of skilled IT security employees stood at 86.6 percent, up from 84.1 percent in 2022.
The highest share of companies experiencing a shortfall of skilled IT security personnel was registered in 2021, at 87 percent.
Fortunately, for now, you can leave the heavy lifting to our Threat Intelligence experts and simply take advantage of the latest AI technology and highly trained/specialized intelligence analysts via our service and technology
In 2022, the average cost of a data breach has reached a record high of US$4.35 million, according to the 2022 cost of a data breach report by IBM and the Ponemon institute.
However, many experts estimate that average costs could reach $5 million in 2023.
Threat Intelligence allows you to implement the right cyber and operational resilience strategies early on, in order to avoid:
- Exploding ad-hoc costs and high damage control spending
- Unpatched vulnerabilities
- Exposed assets
- Human Errors
- Monitoring gaps
Considering that Cyberattacks are increasing world-wide, with 38% more cyberattacks per week on corporate networks in 2022.
Compared to 2021, yearly costs will continue to rise as well.
The need for a reliable yet cost-efficient cyber resilience strategy is out of the question
Finished Threat Intelligence helps your Organization in each planning phase
Tactical Threat Intelligence
Boost early detection with our Tactical Threat Intelligence, featuring vetted feeds that help you swiftly identify and respond to threats
Operational Threat Intelligence
Receive tailored briefs that inform daily decisions. Our Operational Threat Intelligence clarifies the nature and sophistication of attacks, enhancing your defenses and response strategies
Strategic Threat Intelligence
Our Strategic Threat Intelligence helps executives make informed decisions and mitigate potential threats, guiding strategic decisions and long-term security planning
Geopolitics:
An Essential Aspect of Our Threat Intelligence Analysis
At QuoIntelligence, we take a holistic approach to understanding cyberattacks by integrating technical insights with in-depth analyses of economic, social, and geopolitical contexts. Our comprehensive threat intelligence helps you navigate the complex landscape of cyber threats more effectively



Geopolitics:
An Essential Aspect of Our Threat Intelligence Analysis
At QuoIntelligence, we take a holistic approach to understanding cyberattacks by integrating technical insights with in-depth analyses of economic, social, and geopolitical contexts. Our comprehensive threat intelligence helps you navigate the complex landscape of cyber threats more effectively
Why Geopolitics Matters in Threat Intelligence:
Geopolitical factors often influence the motivations and methods of threat actors. Understanding these factors provides critical context for threat analysis
Incorporating geopolitical analysis helps anticipate potential threats and align your cybersecurity strategies with global developments
A holistic view that includes geopolitical insights enables better-informed decisions and more robust risk management
Our threat intelligence solutions are designed to provide you with actionable insights that consider all relevant factors, including the geopolitical landscape.
Learn more about why geopolitics is an integral part of our threat intelligence analyses
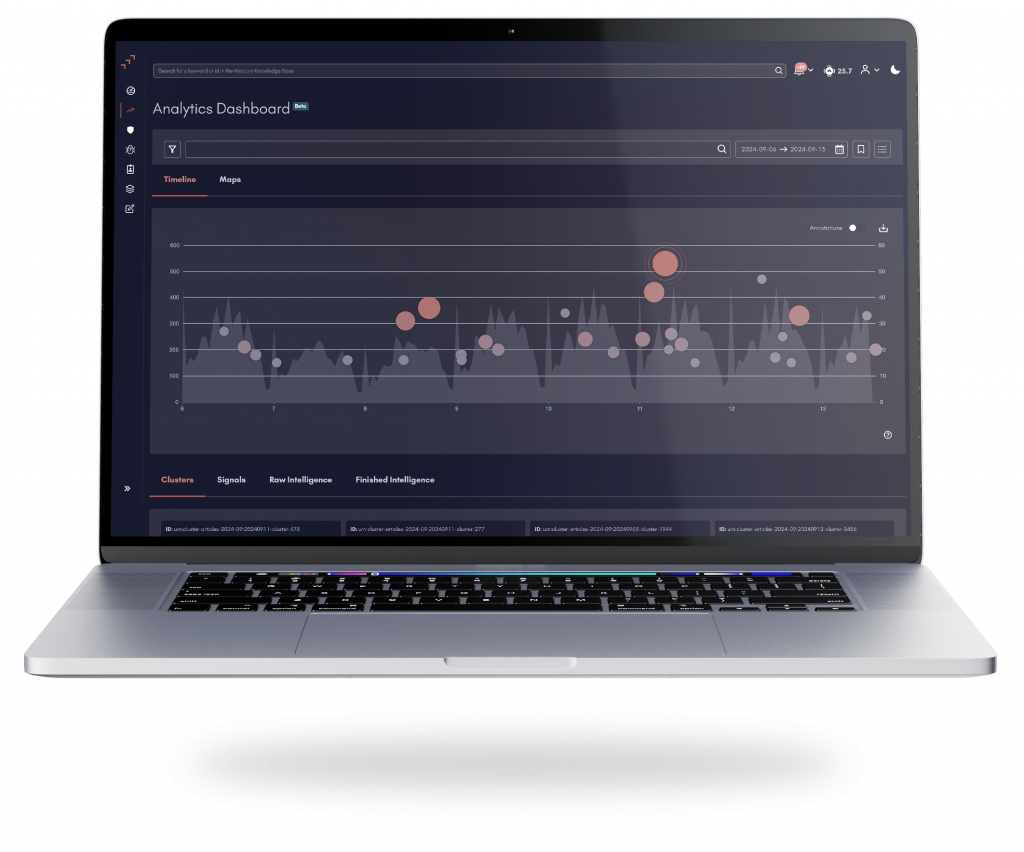
Discover Mercury
Your central hub for Intelligence insight
Mercury grants you access to our threat intelligence services. It not only allows you to view and action alerts relevant to you, but also lets you leverage real-time, interactive, and customizable dashboards and more

Discover Mercury
Your Threat Intelligence Augmented Analytics Platform
Mercury grants you access to our threat intelligence services. It not only allows you to view and action alerts relevant to you, but also lets you leverage real-time, interactive, and customizable dashboards and more
Our work is accredited by:





Stay informed with Our Latest Insights
Get in Touch
with Our Experts and get Access to Personalized Cyber Intelligence
QuoIntelligence experts can help your team understand the evolving threats and provide simple yet comprehensive recommendations so you can focus on what matters.
Do you want to know more about our products and services?
Complete the form and we’ll be in touch shortly!

