The Cyber Threat Intelligence landscape in 2020 was defined by the COVID-19 pandemic, the continuing threat of ransomware attacks, as well as highly sophisticated espionage campaigns.
QuoIntelligence expects these major trends to evolve even further in 2021. While the COVID pandemic and related developments will continue impacting the cyber threat landscape, opportunistic attackers will expand their tactics to force entities to pay ransom.
In addition, we expect a rise in industrial and government espionage. APT groups will focus even stronger on industrial and government espionage, given the considerable impact such campaigns can have on companies and governmental entities alike.
In the following blog post, we will provide an overview of the major cyber trends observed over 2020 and provide an outlook into potential developments in the coming year. Namely, we will address the ongoing COVID-19 threat, ransomware and phishing trends and especially focus on the increasing threat QuoIntelligence sees in industrial, political and military espionage for 2021.
COVID-19 and the Cyber Threat Intelligence Landscape
The COVID-19 pandemic shaped every aspect of 2020, including the cyber threat landscape. During the early stages of the pandemic, cyber actors leveraged the fear, uncertainty, and doubt surrounding the new virus to target victims in phishing campaigns.
We predicted early on that cyber actors will likely leverage the sudden shift to remote working to target organizations by exploiting vulnerabilities in telework technologies and abusing already strained bandwidths with Distributed Denial of Service (DDoS) attacks.
Our prediction has proven itself true: as the pandemic continued, health care providers became increasingly targeted, followed by vaccine-related research entities.
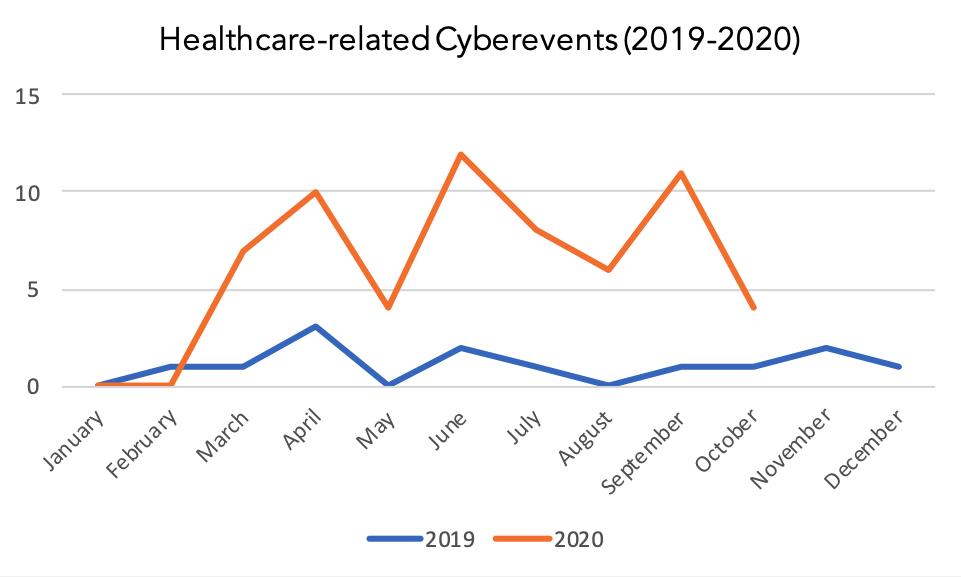
Graph 1: Comparison of healthcare-related cyber incidents recorded by QuoIntelligence in 2019 and 2020
COVID-19 will remain on the cyber threat landscape in the coming year, and cyber actors will proactively adapt their Tactics, Techniques, and Procedures (TTPs) to target victims.
In 2021, vaccines will be rolled out on a large scale, and cyber actors will highly likely continue targeting the infrastructure surrounding vaccine research and distribution. In addition, unknowns on the evolution of the virus and possible vaccine shortages will encourage cyber actors to conduct espionage campaigns trying to control and remain in-step with changing circumstances.
APTs will likely keep exploiting the increased attack surface created by extended remote working conditions, such as unsecured cloud environments or unpatched remote working technologies.
Additionally, threat actors will continue to leverage the pandemic by resorting to social engineering techniques with vaccine-related themes as an entry point for their targeted organizations.
Potentially further worsening the situation could be a recession in the coming year, which might lead to cuts in cybersecurity budgets, further limiting the ability of organizations to counter these cyber threats. As of a recent study by the (ISC)², already 65% of organizations are reporting a shortage in cyber security staff.
Ransomware and Phishing
Apart from COVID-19-related cyber activity, the SIX Group’s annual Cyber Threat Report identified that phishing and ransomware were the top cybersecurity threats in 2020. QuoIntelligence and SIX partnered up for this report: SIX Group operates the infrastructure for Switzerland’s financial sector, and QuoIntelligence contributed to the analysis of the Cyber Threat report. The report surveyed Swiss CISOs on the current and potential future threats their institutions are facing.
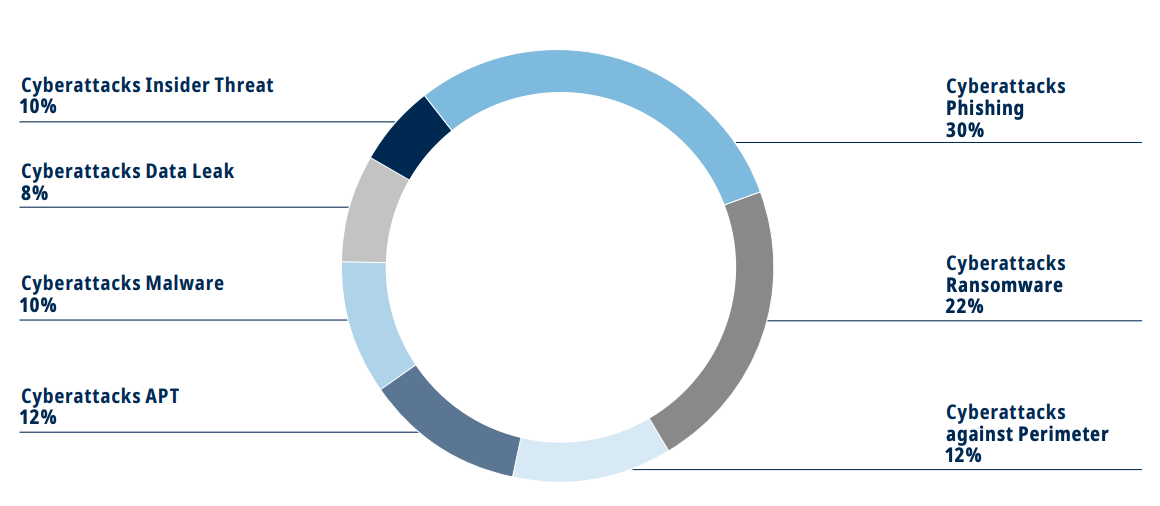
Graph 2: Types of Cyberattacks Identified as Top Threats to the Swiss Financial Sector; Source: SIX Cyber Threat Report 2020
The surveyed CISOs identified that increasing digitization, the difficulty of retaining a skilled cyber security workforce, and the ability to ensure third–party risk management as the main challenges in 2020. However, these specific challenges were not unique to Switzerland.
QuoIntelligence observed, that phishing emails spreading malware and ransomware were the most frequently recorded attack vectors in 2020.
We recorded a spike in the number of reported ransomware and extortion campaigns with increasing ransom demands, with the highest demand observed thus far peaking at EUR 30 Million in December. Ransomware operators have shifted their tactics to stealing data from company networks and threaten to publish it to coerce the company into paying a ransom.
We expect that this trend will continue and potentially increase, as it remains a lucrative activity for cyber actors. In addition, even the disruption of the notorious TrickBot network operation in October, the lull in Emotet activity, and the announcement of Maze Group to retire has not had any considerable effect on slowing the spread of ransomware.
New ransomware operator groups, such as Egregor, were quick to fill any voids. While we expect to see increasing scrutiny by law enforcement agencies to prevent payment to ransomware operators, threat actors will highly likely continue their extortion tactics to enforce payments, such as publicly releasing stolen files.
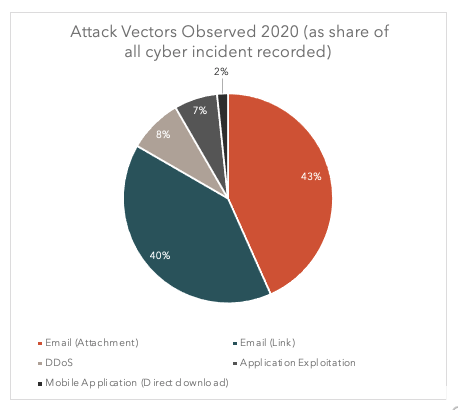
Graph 3: Attack vectors observed in 2020 (as shared of cyber incident recorded); Source: QuoIntelligence
Advanced Persistent Threat Groups (APT) and Espionage in 2021
What are APT Groups? By definition, APT groups are highly advanced cyber actors that use sophisticated techniques to target their victims. Threat actors conduct espionage operations to steal sensitive data, such as intellectual property or military intelligence, which can lead to significant competitive advantages in the geopolitical and economic spheres. In many cases, nation-states sponsor these groups to conduct operations.
Learn more about how governments utilize cyber groups and the interaction between geopolitics and cyber.
While nation-states can utilize cyber actors for various means – including for acts of sabotage in times of conflict – APT groups are frequently engaged in espionage activities, which are often long running and stealthy.
APTs and Industrial Espionage
In the previous year, QuoIntelligence observed various industrial espionage campaigns, for example Chinese espionage APT Winnti Group targeting German industrial organizations. The US, Germany, and the UK previously have warned over industrial espionage by Chinese APT groups.
QuoIntelligence expects to see continued corporate espionage campaigns by Chinese APT groups, as geopolitical and domestic developments will likely further encourage China’s push for accelerating their economic development. In terms of geopolitics, tensions between China and the US resulted in trade restrictions with Chinese companies and excluded Chinese companies from the US and European markets in 2020.
In order to reduce critical dependencies on imports and accelerate self-reliance, China’s government has pushed for accelerated development in key sectors. These high-priority industry sectors are outlined in China’s policy briefs, such as the Made in China policy and include the high-tech sector, the semiconductor industry, autonomous vehicles, AI and machine learning, as well as new materials.
In March 2021, the latest Five-Year economic plan is scheduled to be released, which also highlights China’s development in the high-tech sector as crucial.
Given the potential advantage that spying on intellectual property provides to nations, other emerging states might increasingly use cyber activity in the future. For example, APT groups attributed to Vietnam have been observed increasingly targeting organizations globally, correlating with Vietnam’s government interests.
Political and Military Espionage
The CISOs surveyed for the SIX report also voiced their concerns over being able to adequately ensure third party and supply chain security. The threat of supply chain attacks became an urgent concern in December after FireEye reported on the SolarWind backdoor. Thousands of companies worldwide, including US and European government entities, were impacted. However, the true extent of SolarWind’s massive cyber breach is not yet clear, as further analysis is needed to understand which organizations and systems were impacted and how. The incident highlighted the incredible capability of APT groups and the massive damage they can cause.
Geopolitical tensions and developments are frequently mirrored in cyberspace, and nation-states utilize their APT groups to conduct espionage campaigns to further their knowledge on their adversaries. In 2021, QuoIntelligence expects to see cyberactivity related to several key regions:
Russia: Media agencies quickly attributed the SolarWinds supply chain attack to Russia, and while no evidence to substantiate the claim is yet publicly available, it falls within the pattern of previous Russian cyber activity. Tensions between Russia, the US, and Europe worsened over the previous year, especially due to sanctions on Russia for cyberattacks targeting EU member states. Therefore, Russian APT groups are likely to continue targeting US and European governmental entities in the coming year. In addition, we expect to continue observing campaigns targeting governments in Russia’s spheres of interest, such as the South Caucasus and the Middle East.
Iran: The election of Joe Biden as US president will potentially change the current tensions in the Middle East, depending on President-elect Biden’s stance toward Iran. Iran’s President Rouhani has called on President-elect Biden to rejoin the Iranian nuclear deal and ease sanctions on Iran in return for curbing Iran’s uranium enrichment program, which could potentially ease tensions in the region. However, it remains to be seen how the recent normalization of diplomatic between Israel and several Gulf states will impact the power dynamics in the region. While Iranian sponsored cyber campaigns are not as sophisticated as those from China or Russia, Iranian APTs– such as APT34, APT33, APT35, and MuddyWater– have actively targeted industries in Israel, the US, and Europe, showcasing their ability to conduct disruptive attacks.
Conclusion
The COVID-19 pandemic will continue shaping the cyber threat landscape in the coming year, and opportunistic cyber actors will likely evolve their TTPs to ensure their victims are pressured into paying ransoms. In addition, APTs will keep following their nation-state’s agendas by engaging in industrial espionage to further the state’s economic interests or by utilizing cyberspace as result of geopolitical tensions.
APTs will likely evolve their TTPs to avoid detection and increasingly utilize supply chain attacks to infiltrate targeted organizations by abusing established trust relationships.
QuoIntelligence continues monitoring the threat landscape and geopolitical developments to detect potential motivation early on and forecast likely future outcomes. In order to track threat actor evolutions and stay ahead of their operations, we continuously update our QuoIntelligence knowledge base, which includes our Threat Actor catalogs.
The catalog entries include descriptions of past and current activities, the groups’ motivations and intentions, up to date information on their TTPs, which are mapped to the MITRE ATT&CK Framework to enable automatic detection and tagging efforts, and more!





