On 24 December 2020 the EU and UK reached the Trade and Cooperation Agreement (TCA), which regulates EU-UK relations with the Brexit transition period ending on 31 December of the same year.
The agreement is wide-ranging, and both parties still need to ratify it. Nevertheless, both parties will provisionally apply the deal until 28 February 2021.
While both the EU and UK have welcomed the agreement, as it will avoid the introduction of tariffs and quotas on goods traded between the EU and the UK, there are yet specifics on critical issues to discuss, such as cybersecurity, information-sharing, defense, and foreign policy.
Read on for our analysis on the current state of those critical key issues and learn how they might impact your organization. In the end of the text, you’ll find an infographic summarizing the most important points for you.
Why should you pay attention to the EU-UK Trade Deal?
EU-UK cooperation in critical areas related to cybersecurity, information–sharing, or data protection poses important challenges that the EU and UK will yet need to solve in the coming months or even years after Brexit. Many of the details on how the new arrangements will work are still unclear or need further clarification.
Cutting through the confusion
Our QuoIntelligence Analysts provide you with a summary of the Brexit key issues regarding cybersecurity, security and intelligence cooperation, information-sharing, data protection and GDPR below.
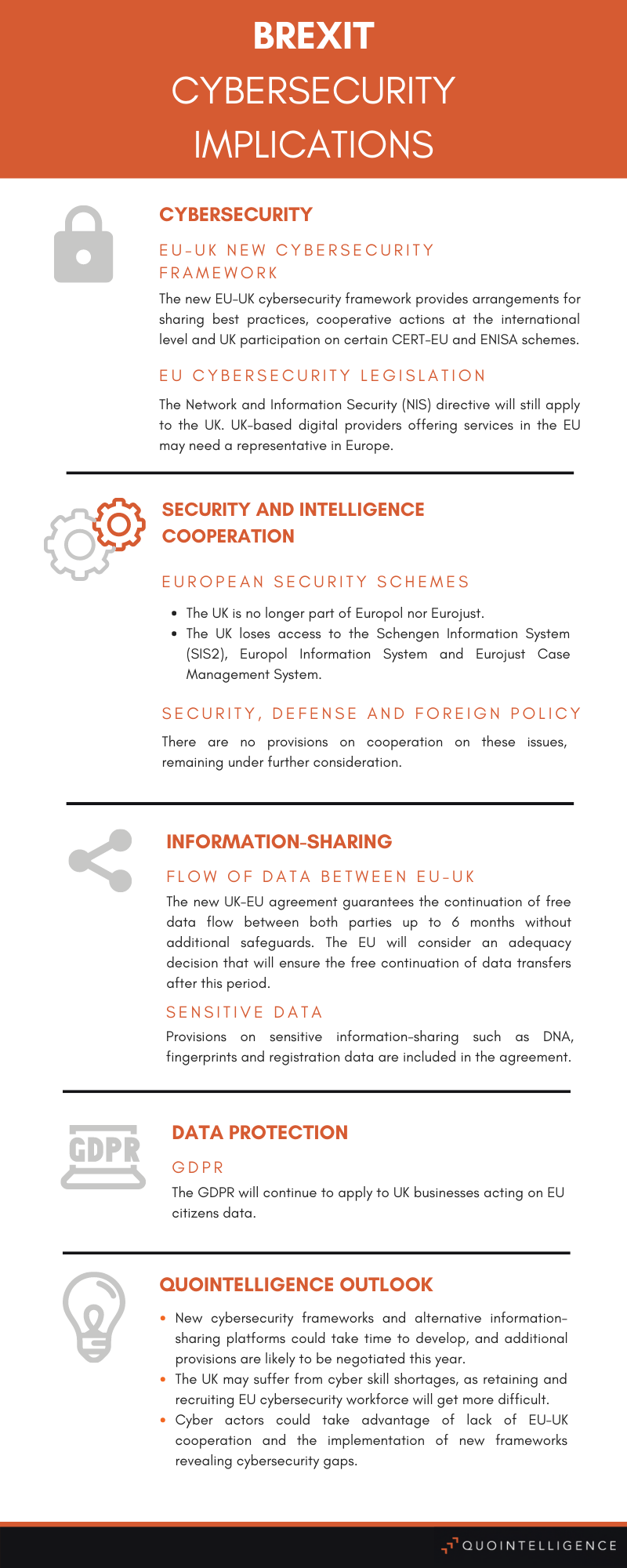
Cybersecurity
The TCA provides a framework for cooperation in the field of cybersecurity, including arrangements to support information–sharing on best practices and cooperative actions at the international level. It also includes provisions on cooperation with EU expert bodies.
Subject to EU invitation, the UK could benefit from CERT-EU information–sharing on cyber tools and methods and participate in certain European Union Agency for Cybersecurity (ENISA) activities.
NIS Directive & Talent Hunt
Regarding EU cybersecurity legislation, the Network and Information Security (NIS) directive will still apply to the UK. However, UK-based digital service providers offering services in the EU may need to appoint a representative in one of the EU member states in which companies offer services.
While the TCA provides a new framework on cybersecurity cooperation to replace some of the collaboration schemes built up over the years, the outline of the framework is not yet defined.
With Brexit leaving a changing and uncertain landscape, cyber actors could take advantage of security gaps during the implementation of new frameworks.
Additionally, the UK may suffer from skills shortages, as retaining or recruiting cyber talent from EU countries gets more difficult. The supply pipeline from UK universities could further weaken without Erasmus exchange programs and a reduced intake of EU citizens.
Security and Intelligence Cooperation
As a so-called third country, meaning a country outside the EU, the UK will no longer be part of Europol and Eurojust. As a result, the UK will not have access to the Europol Information System nor full access to Eurojust’s case management system.
National Security & SIS2
The UK will also lose access to data-sharing agreements due to Brexit, such as the Schengen Information System (SIS2), which provides police with data alerts on criminal suspects, missing people and stolen property.
While international bodies such as Interpol and ad hoc bilateral agreements could fill this gap, the EU and UK appear to have not contemplated creating a substitute system.
Since the British police access the SIS2 system more than 1.65 million times per year, negotiations on maintaining access or developing alternative platforms are likely to continue in the coming months.
Moreover, the UK did not wish to negotiate cooperation on foreign policy, security and defense to address external security threats, as it considered the issues a low priority.
Thus, the UK’s degree of involvement in EU security, defense and foreign policy, such as PESCO projects, remains uncertain.
Information–Sharing, Data Protection & GDPR
With the Brexit transition period ended, data transfers between Europe and the UK constitute a transfer of personal data to a third country.
Nevertheless, the TCA grants the continuation of EU-UK data flows without implementing additional safeguards for up to six months. During this period, the European Commission will consider issuing an adequacy decision, confirming that the UK operates acceptable data protection standards that will ensure the free flow of personal data.
However, the adequacy decision could take in excess of six months. In the absence of a ruling, transfers to the UK will need to comply with EU GDPR restrictions.
Data Flow & Outdated Systems
As a precaution, before this six-month period ends, the UK Information Commissioner’s Office (ICO) recommends that businesses working in the EU and UK take additional safeguards to prevent any interruption of the free flow of data. These measures should be in accordance with the GDPR provisions set for information–sharing with third countries.
Regarding EU data protection regulations, the GDPR will continue to apply, as the EU anyway requires any international trading partner acting on the personal data of EU citizens to respect GDPR. The UK government has also announced that it intends to transpose GDPR into domestic law, but the UK will have the independence to review the framework.
While the agreement also contains provisions on sensitive information–sharing, such as DNA, fingerprints and registration data, it also provides outdated recommendations on how to secure and share information between parties. The agreement provides protocols and standards for encryption using unsupported and insecure technology such as 1024-bit RSA encryption and the SHA-1 hashing algorithm to share highly sensitive information. The agreement also refers to Netscape Navigator, which stopped working in 2008.
While these outdated references are most likely due to the urgency with which the 1000-page agreement was written, it also reflects the need to further review and modify the agreement in critical issues that affect cybersecurity after Brexit.
In Conclusion: Necessary Brexit Arrangements Will Take Much More Time
While crucial aspects on the future of EU-UK relations are still under consideration, it is likely that in the coming year the EU and UK will put the necessary deals and frameworks in place to preserve cybersecurity and information-sharing.
Outdated encryption methods and a lack of alternative intelligence–sharing platforms are critical security issues that evidence the need for further discussion and modifications of the TCA.
However, these arrangements could take time to develop and yet be less efficient than the EU integrated system of which the UK has been formerly part of, as cybercrime activities are best tackled from a cooperative, supra-national perspective.
Cyber actors could take advantage of the new landscape, leveraging any security gap in newly established frameworks and relationships between companies and governments.
Talk to our experts today to learn how this transition evolves, related geopolitical repercussions, and learn the potential risks this transition introduces to your organization.