Research and article by Eduardo González Hernández.
Audience-Role: Security Leadership | Sector: Government
Disinformation campaigns to attempt to disrupt or influence European elections continue. A recent example in Spain shows how they can be structured to target niche groups.
The recent years have seen an increase in information operations aimed at interfering with the election processes in Europe. These operations are designed to spread disinformation and manipulate public opinion to influence the outcome of elections. While these campaigns tend to exploit the widest demographics to maximize impact, some threat actors are willing to dedicate resources to reach niche populations.
In this article, we provide an overview of a recent campaign that targeted the Russian-speaking population in Spain.
In truth, the focus on the Russian-speaking population in Spain likely had a limited effect on the overall general election result. The population of Russian citizens in Spain was around 80,000 people in 2021, and over 100,000 short-term visas were issued in 2022. This number is low compared to the total election turnout of over 24 million and doesn’t take into account the fact that the majority of Russian-speaking residents were not able to vote.
However, it demonstrates that disinformation operations can target demographics of any size — in this case Russian-speaking people in Spain — to increase the effectiveness of their operations. The goal of the threat actors is not clear, but it is likely that they are attempting to steer the targeted population to spread false information, such as allegations of incoming terrorist attacks, among their local communities in Spain. Furthermore, it demonstrates that these types of tailored disinformation campaigns challenge assumptions of what groups of voters are susceptible to election conspiracies and their distrust in voting systems.
Background
On 22 July, a day before Spanish General Elections were held, the association of Free Russians in Spain announced through its Twitter account that it received reports from Russians living in Spain about Telegram messages discouraging them from taking part in elections due to coming terrorist attack. The messages contained a link to the alleged website of the Community of Madrid with information about terrorist organization ETA planning a series of attacks. The message encouraged recipients to skip the elections to avoid risk to their lives.
Analysis
From a technical perspective, the campaign showed basic but well-applied methodology with proper use of language, selection of targets, and preparation of disinformation materials. The campaign:
- Messages contained a link to a fake website that mimicked the legitimate website of the Community of Madrid, which provided information about an alleged coming terrorist attack. The message encouraged recipients to skip the elections to avoid risking their lives.
- Used Telegram for reach. The operation’s infrastructure indicates the adversary used a popular Russian bulletproof hosting provider — an internet hosting service providing technical infrastructure resilient to complaints of illicit activities —associated with multiple campaigns.
- Used fewer delivery mechanisms than other campaigns that have relied on copied or fake news sites, and did not use massive social media campaigns to spread its message.
- Displayed moderate capabilities with properly formatted messages used to deliver narrative, domain names using proper syntax and Spanish Top Level Domains, and cloning of the legitimate website layout.
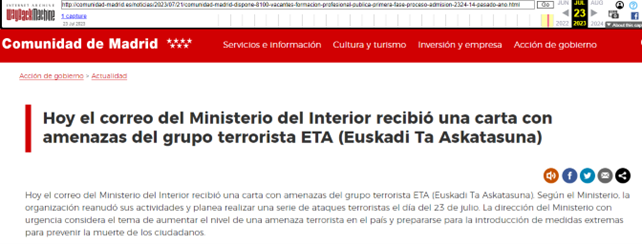
Malicious website impersonating the Comunidad de Madrid site
An overview of the campaign using the Diamond Model for Influence Operations Analysis:
| Narrative | Terrorist attack planned for during the 2023 Spanish Elections |
| Influencer | Not known |
| Audience | Russian population permanently living in Spain |
| Capabilities | Russian language messages Delivery of messages through Telegram Cloning legitimate websites Typosquatting domains Use of country specific narrative |
| Infrastructure | Use of bulletproof hosting in Russia |
The campaign represents moderate capabilities with the ability to properly format messages used to deliver the narrative, a domain name using proper syntax and ES TLD, and using cloning of layout of the legitimate website.
Screenshot of the original message

Figure 1 – Telegram message to discourage participation in the elections
Message translation:
“Hi. You don’t know me, but I have important information to give you! If you are in Spain now, then read. Watch out! ETA is back and planning attacks! Don’t go to the polls! Don’t put your life in danger! Pass this to your friends, family and loved ones! Even on the Spanish Ministry of Interior’s website they write about it! It’s all very serious… http://comunidad-madrid[.]es/”
The link impersonated the legitimate site of the Community of Madrid. At the time of analysis, the website was offline, however it has been captured by the Internet Archive and is available for analysis. The malicious website was an exact copy with fake information about the Ministry of Interior warning about a planned series of ETA attacks.
Based on the content of news articles from the legitimate website and comparing it against articles on the malicious ones, the site was created between 10:08 and 11:46 on 21 July, 2023, Spanish time (UTC+2).
The domain was hosted on the IP address 185.251.88[.]12. This address belongs to Sprinthost.ru LLC, a Russia-based hosting provider. Its WHOIS records contains:
| organisation: | ORG-SL311-RIPE |
| org-name: | SPRINTHOST.RU LLC |
| country: | RU |
| org-type: | LIR |
| address: | ul. Staroderevenskaya, d. 11, korp. 2, office 300 |
| office 300 address: | 197374 |
| address: | Saint-Petersburg |
| address: | RUSSIAN FEDERATION |
Analysis of passive DNS response data reveals the following list of domains hosted using the same resources:
interior-gov[.]es
comunidad-madrid[.]es
lamodka[.]site
xn—–6kcc1badjcdxfsuukj[.]xn--p1ai
servicecenter-verifizieren[.]com
vps-hosts[.]ru
jetzt-verifizieren[.]com
kundencenter-verifizierung[.]com
kundencenter-verifikation[.]com
trallafittiinnarutoskitty[.]com
ueberpruefung-beginnen[.]com
verifikation-vorgang[.]com
servicecenter-verifikation[.]com
validation-beginnen[.]com
kefunden[.]com
validierung-prozess[.]com
starte-ueberpruefung[.]com
vhost-vps[.]ru
support-validierung[.]com
verifikation-jetzt-abwickeln[.]com
support-authentifikation[.]com
authentifikation-vorgang[.]com
verifizierung-starten[.]com
veri-vorgang[.]com
servicecenter-validierung[.]com
dediccloud[.]ru
verifizierung-online-starten[.]com
validierung-starten[.]com
center-verifikation[.]com
kundensicherheit-ueberpruefung[.]com
kunden-verifikation-sofort[.]com
validation-center[.]com
verifikation-fuer-kunden[.]com
center-ueberpruefung[.]com
kunden-validierung[.]com
sicherheit-kunden[.]com
kunden-sicherheit[.]com
sicherheit-center[.]com
kundencenter-hilfe[.]com
support-kunden[.]com
konto-verifizieren[.]com
host-file-host6[.]com
4strapi[.]site
www[.]4strapi[.]site
Beyond the original website, we noticed the domain interior-gov[.]es that also attempts to impersonate the Spanish official website (domain of the Ministry of Interior “interior.gob.es”) and has likely been registered by the same threat group. This is further supported by the fact that we observed domains active within days of each other (on the 22 and 23 July). This domain, however, has not been observed in any other campaign and it is not possible to determine whether the threat actors abandoned it to focus on the comunidad-madrid[.]es site, or planned to use it in different campaigns.
The second major group of domains is multiple German language-themed created in December 2022. All the domains use naming schemes alluding to the verification and authentication process and were marked by multiple vendors as phishing on VirusTotal — as such these were likely registered in preparation for a phishing campaign. However, we could not confirm this assertion with the discovery of actual websites. Given the dates of observed domain resolutions, it is likely the campaign using German domain names was separate from the influence operation.
Few of the observed domains had a naming convention related to VPS and file hosting services likely indicating another Command-and-Control infrastructure creation.
The infrastructure is represented in the following figure. Notably, the authentication-themed domains are a significant majority of all found domains:
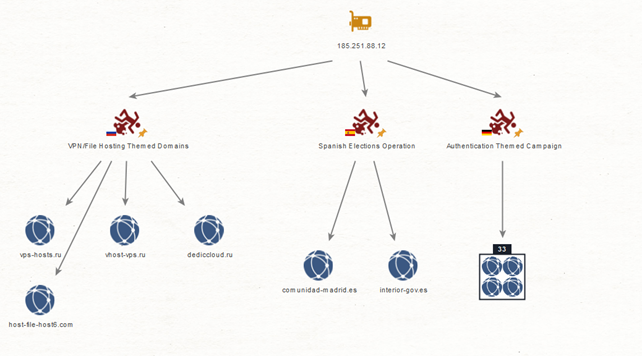
Figure 2 – Domains related to 185.251.88.12 IP
Sprinthost is considered a “bulletproof” hosting provider associated with multiple malware and phishing campaigns.* Therefore, the infrastructure was likely selected to limit the possibility of website takedown through law enforcement requests.
Notably, as the campaign was targeting the election period and election turnout the adversary had to maintain the infrastructure for less than a week, making it difficult to take effective action limiting its reach. For the same reason use of a hosting provider also used by malware and phishing campaigns made it difficult to link infrastructure to other campaigns. Given that the efforts were targeting private persons, drawbacks related to potential blocking domains hosted by suspicious registrars through enterprise security solutions are limited.
*SilentPush, C2, 7 January 2022, USPS phishing on a bulletproof hosting network
DISARM Framework**
| Technique | Procedure |
| T0043.001 “Use Encrypted Chat Apps” |
Telegram messaging application used to deliver message to targets |
| T0072.002 “Demographic Segmentation” |
Russian-speaking population in Spain targeted |
| T0130.002 “Utilize Bulletproof Hosting” |
Disinformation website hosted on Sprinthost, a provider |
| T0098.001 “Create Inauthentic News Sites” |
Legitimate news sites of the community of Madrid copied to create inauthentic version of it |
| T0085.003 “Develop Inauthentic News Articles” |
Fake news from the Ministry of Interior created warning of coming ETA attacks |
| T0003 “Leverage Existing Narratives” |
Campaign narrative used history of ETA terrorist activity |
**DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis, and coordinating effective action. The Framework has been developed, drawing on global cybersecurity best practices. It is used to help communicators, from any discipline or sector, gain a clear, shared understanding of disinformation incidents and to immediately identify available defensive and mitigation actions.
Implications for CISOs and CIOs
The use of Telegram messages and fake websites shows that the threat actors were willing to dedicate resources to reach even niche populations. The limited delivery mechanisms used by the campaign and its focus on a specific demographic likely resulted in minimal impact.
However, the campaign is part of an effort to target directly selected populations to increase the effectiveness of operations. CISOs and CIOs should be aware of the prevalence of information operations aimed at interfering with the election process in Europe and ensure that their organizations have robust security measures in place to protect against disinformation campaigns and other types of cyber threats.
Concrete countermeasures include:
- Be aware of the prevalence of information operations aimed at interfering with the election process in Europe and the potential impact on your organization. These include destabilization through loss of trust in government and institutions, damage to reputation, economic impact, and security risks.
- Ensure that your organization has robust security measures in place to protect against disinformation campaigns and other types of cyber threats, including social media monitoring and analysis, collaboration with government agencies, and establishing incident response plans.
- Educate your employees about the risks of disinformation campaigns and how to identify and report suspicious activity.
- Stay up-to-date with the latest threat intelligence and share this information with your team to ensure that you are prepared to respond to any potential threats.
Conclusion
It is not possible to attribute the activity with high confidence to any threat actor, given the limited technical footprint. However, correlation with techniques used earlier in Russian-led campaigns described by Meta, and the specific targeting of the Russian population indicates with low confidence that the operation was linked to the Russian nexus of information operations.
What is almost certain is that information operations aiming to disrupt political processes in EU countries will continue. This is based on the high prevalence of similar efforts seen across Europe, the low cost of carrying out such operations, and the continuous political tensions driving the national goals that are behind these operations.
CISOs and CIOs must be vigilant and proactive in protecting their organizations from these threats. While implementing robust security measures, educating employees, and staying informed about the latest threat intelligence are essential, it’s important to recognize that no company is completely secure all the time.
QuoIntelligence
We provide the cyber and geopolitical intelligence critical for organizations to maximise security and minimize risk, with a specific focus on Europe. If you would like to have an informal discussion with one of our Threat Advisory experts, please book a call here: Talk to an Expert
Keep up to date
To keep up with the latest cyber and geopolitical threats, subscribe to QuoIntelligence’s Weekly Intelligence Newsletter, published every Thursday around 1900 CET.


