In recent years, Telegram has emerged as a significant platform for both legitimate communication and illicit activities. Its anonymity features and minimal content moderation have made it particularly attractive to criminals and extremist groups. The arrest and indictment of Telegram’s CEO, Pavel Durov, raises questions about how criminals and the platform’s policies will adapt.
This article examine how various criminal networks leverage Telegram for illegal activities and assess the impact of Pavel Durov’s arrest on the cyber threat landscape.
Key Findings
Our main takeaways and key findings in this article include:
- Telegram’s Features and Policies Attract Criminal Networks: Telegram’s privacy features and minimal content moderation make it a popular platform for illegal activities, including cybercrime, drug trafficking, child pornography, influence operations, and extremist propaganda.
- Bot Automation on Telegram Reduces Entry Barriers for Cybercriminals: Cybercriminals leverage Telegram’s ease of use and Bot API to set up marketplaces, automate phishing, distribute malware, and manage command-and-control operations, lowering the barriers to entry for illicit activities.
- Telegram CEO’s Legal Troubles Unlikely To Cause Immediate Disruption Of Cybercrime Activities On The Platform: Despite the recent indictment of Pavel Durov, in the short term, cybercriminals will likely continue to leverage Telegram for their operations as the platform’s main privacy and security features are expected to remain.
- Child Abuse and Drug Trafficking, Possible Focus Of Expected Moderation Efforts: Telegram’s announced moderation efforts will possibly target child abuse content and drug trafficking, as these are the primary charges brought against Pavel Durov by French authorities.
French Authorities Arrest Telegram CEO Over Malicious Activities Ongoing On the Messaging App
On 24 August, French authorities arrested Telegram CEO Pavel Durov at a French airport. On 28 August, investigative judges filed preliminary charges against Durov for various violations related to Telegram. He was granted conditional release upon posting a bail of EUR 5 million, with the obligation to report to a police station twice a week.
Pavel Durov is accused of refusing to provide information or documents to investigators when legally required, money laundering, as well as breaching laws restricting the provision of cryptographic services without prior and conform declaration. Charges against Telegram CEO also include aiding and abetting in: administration of an online platform enabling illicit transactions for organized crime; possession and diffusion of child pornographic content; acquisition, transport, possession, and transfer of narcotics.
Technical Features and Moderation Patterns Conducive To Criminal Activity
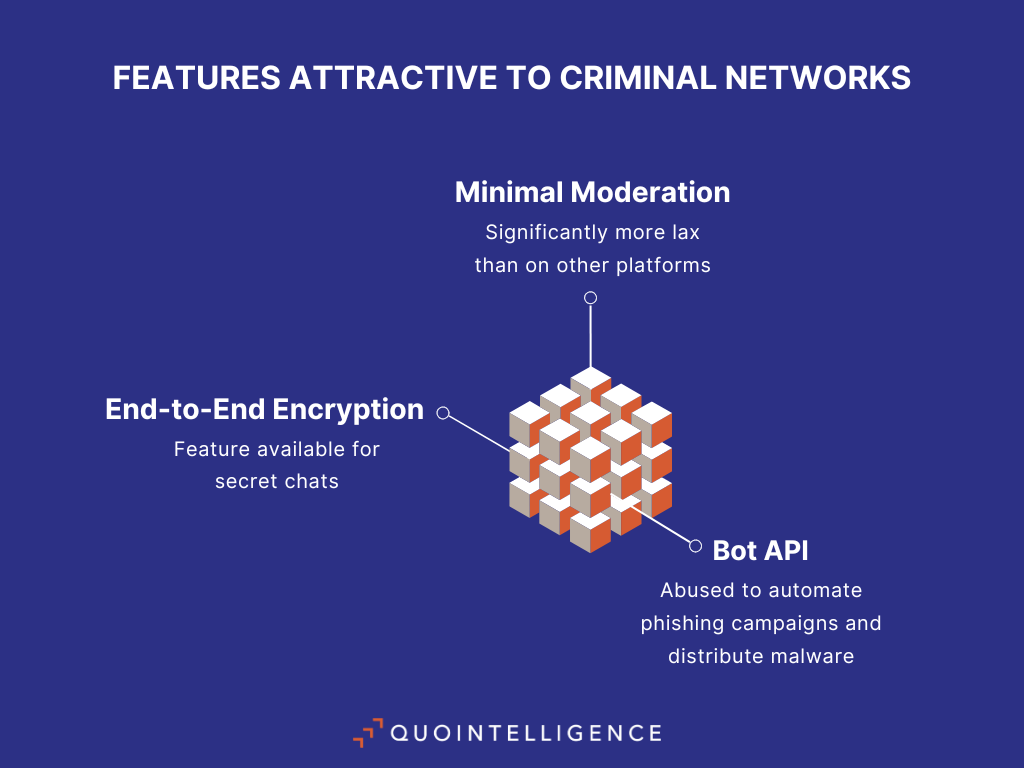
Telegram’s technical features present some beneficial aspects for criminals. The messaging app claims to be designed with a focus on privacy and security. It markets itself as more secure than its competitors, like WhatsApp and Line, due to encryption via the MTProto protocol. Telegram’s MTProto protocol is designed to secure messaging through encryption. It operates by establishing a secure client-server communication channel. Messages are encrypted on the client side using a combination of symmetric and asymmetric encryption methods. This allegedly ensures that only the intended recipient, via the server, can decrypt the messages. MTProto also uses session-based encryption, meaning each session has its unique encryption key. While end-to-end encryption is not enabled by default on the platform, it is provided for secret chats and voice and video calls.
Standard chats are only encrypted between the client and the server. To prevent law enforcement from accessing users’ data from standard chats, Telegram emphasizes that it does store the encryption keys on its servers. Encryption keys are distributed across multiple data centers in different jurisdictions, making it challenging for any single authority to gain comprehensive access.
Additionally, Telegram’s approach to content moderation is more lax than other messaging apps. The platform says it uses a combination of AI-driven and manual moderation for public content, together with processing user reports. Pavel Durov claims Telegram is a “place of complete freedom for the distribution of all information and media.” Consistently, Telegram’s moderation process operates with minimal oversight of chats and an overall lack of transparency.
The platform is also versatile and easily accessible. It is available both as a mobile app and a desktop app. This presents a significant advantage, enabling accounts to reach a broader audience. Furthermore, unlike other platforms, Telegram allows users to create accounts using a virtual phone number, providing a higher degree of anonymity.
Finally, Telegram allows the creation of bots through its Bot API. These bots are automated programs that can interact with users, send messages, and perform tasks within chats. Such bots are leveraged by cybercriminals for illicit activities, including automating phishing campaigns and distributing malware. In phishing campaigns, Telegram bots are often used to collect stolen data and facilitate communication between scammers and victims, allowing cybercriminals to scale their operations efficiently. Threat actors also resort to Telegram bots as command and control mechanisms for information stealers.
Telegram Leveraged For Drug Trafficking, Terrorism, Information Operation, and Cybercrime
Telegram’s technical features and its approach to moderation have made the platform attractive for a wide range of criminal activities.
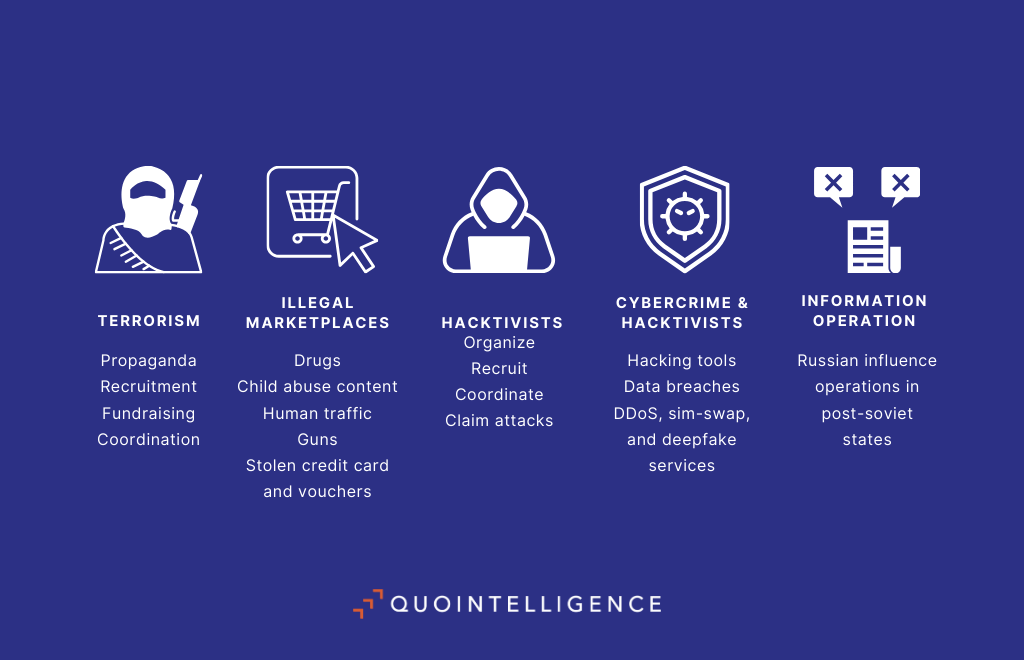
The messaging app is widely used as a marketplace for illegal trades including drugs, stolen credit cards, guns, fake or stolen vouchers and gift cards, child pornographic content, and human traffic.
Terrorist and extremist groups have also used Telegram for propaganda purposes, recruitment, fundraising, and coordinating terrorist activities. In 2015, ISIS members turned to Telegram after increased efforts from Twitter (now X) and Facebook to remove jihadi content from their platforms. Similarly, far-right extremists shifted to Telegram after the social network Parler shut down in 2021.
A growing number of cybercriminals also resort to Telegram to advertise the sale of hacking tools and data breaches, as well as phishing, DDoS, sim-swap, and deepfake services. This use has become even more prevalent with the rise of the as-a-service business model, in which the infection chain is refined into different parts performed by specialized actors. Additionally, Telegram illicit marketplaces are easier to set up and can benefit from a broader audience, therefore lowering the barrier to entry for criminals.
Multiple hacktivist groups with different political motivations also heavily rely on Telegram to organize, recruit, coordinate their activities, connect with their audiences, and publish claims of their attacks. Lately, pro-Russia hacktivist groups and hacktivists from Muslim-majority countries are most active on the messaging app.
Telegram also serves as a platform for influence operations, particularly in post-soviet states where the app is highly popular. Recently, researchers have highlighted the use of Telegram to spread anti-Western and anti-Ukrainian narratives through Kremlin-run channels.
Criminal Networks leverage Telegram for illicit activities
Hacktivist Groups Launch Low-Impact Campaign Targeting French Entities
Following Pavel Durov’s arrest, hacktivist groups promptly announced the launch of a campaign to protest against his detention. We observed both pro-Russia and pro-Palestine hacktivist groups involved in this operation. We identified the following groups: RipperSec, CyberArmyofRussia_Reborn, Usersec, CyberVolk, CyberDragon, Cyberia, GCPLLNET, Godfather, Vulcansec, Overflame, Hacker Council Global, EvilWeb, CGPLLLNET, Stucx Team, Sylhet Gang-SG, RCH-SEC, RADNET64, Evil of Anti DDoS, and Athena. Some of these groups maintain links with Russian intelligence agencies. In April, researchers found that the hacktivist group CyberArmyofRussia_Reborn is linked to Russian state-sponsored threat actor APT44 (aka Sandworm), which pertains to the Unit 74455 of Russia’s Main Intelligence Directorate (GRU). APT44 reportedly used the Telegram channels of these groups to claim responsibility for its wartime disruptive operations.
Targeted entities are mainly French but also include some European institutions. Victims are among public and private organizations. This campaign mainly translated into various waves of DDoS attacks. DDoS attacks carried out by these groups are usually layer 4 (SYN flood attacks) and 7 (high volume POST/GET requests or Slow HTTP requests), due to ease of deployment and effectiveness in the short-term disruption of services.
The impact is usually short-lived. In most cases, disruption lasts between minutes and a few hours and only affects publicly-facing services. Nevertheless, this can have financial repercussions for sales websites. In any case, the impact remains much lower than other types of cyberattacks like ransomware. Anti-DDoS solutions are usually effective in mitigating this type of attack.
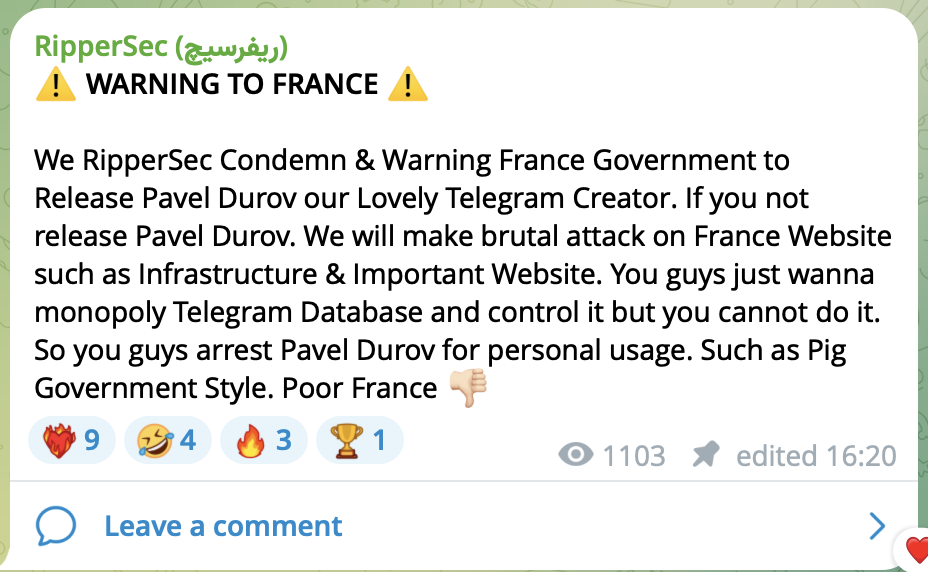
Screenshot of hacktivist group RipperSec’s post on Telegram of 25 August 2024
Impact of Telegram CEO Arrest For The Platform and Illicit Uses
In the short-medium term, the indictment of Pavel Durov is unlikely to significantly disrupt the cybercrime activity ongoing on Telegram.
As encryption keys are spread under different jurisdictions, with some likely located in states unlikely to cooperate with French authorities, we assess that Telegram is very unlikely to share users’ data with French law enforcement. Furthermore, the investigation into the charges and the legal proceedings surrounding them are likely to take years. As such, the Telegram CEO is unlikely to be convicted in the short-medium term.
Following his release, Pavel Durov published a message on its official Telegram account announcing changes in the platform. The app CEO said that his company will focus on turning “moderation on Telegram from an area of criticism into one of praise.” Additionally, Durov announced phasing out two features that have been abused for illicit purposes. New media uploads to Telegraph, the app’s standalone blogging tool, are now disabled and the People Nearby feature has been removed. Additionally, Telegram has reportedly edited the FAQ section on its website, removing language saying private chats are protected and that requests for moderation would not be processed. Instead, Telegram now emphasizes that users can flag illegal content for moderators to review. As charges against Pavel Durov specifically mention drug trafficking and child pornography, the company could concentrate its moderation efforts on these two issues. Despite these announcements, Telegram will likely continue to portray itself as a platform focused on privacy as it plays as a market differentiator. A drastic change in its security policy would drain its number of users.
All other things being equal, in the short term, established cybercrime marketplaces on Telegram are unlikely to shift to other alternatives as the platform still displays attractive features for their activities. Additionally, moving their infrastructure to the dark web would possibly result in a loss of customers. Some marketplaces could test other alternative apps as backups but are unlikely to completely shift their operations in the short term.
23 September Update:
Telegram CEO, Pavel Durov, announced on his Telegram channel updates to the platform’s Terms of Service and Privacy Policy. Telegram will now disclose IP addresses and phone numbers of users who violate its rule in response to valid legal requests. Additionally, the platform has strengthened its moderation, preventing the discovery of problematic content through its search engine. These recent measures undermine Telegram’s identity as a privacy-focused messaging app. Some criminal groups, including cyber threat actors, are already shifting their communications to other platforms. This development is likely to reshape the threat landscape in the medium term, as cybercriminals adapt their infrastructure to avoid operational disruption.





