October marked the deadline for EU member states to transpose the NIS2 Directive into national law, a significant step in the evolution of Europe’s cybersecurity landscape. But what exactly is NIS2, and how does it impact organizations across various sectors? NIS2, an update to the original Network and Information Security Directive, expands the scope of cybersecurity regulations, imposing stricter requirements on a broader range of entities. In this post, we will explore the key aspects of NIS2, including which sectors are affected, what new obligations companies must meet, and the penalties for non-compliance.
Key Takeaways
- The NIS2 Directive significantly expands the scope of the 2016 directive on security of network and information systems, introducing new critical and highly critical sectors, such as Chemicals, Goods Production and Processing, and Public Administration.
- The directive mandates that in-scope entities follow strict incident reporting protocols. This includes an early warning within 24 hours of an incident, a detailed report within 72 hours, and a final report within one month.
- Under NIS2, entities must implement a broad range of mandatory security measures, such as risk analysis, business continuity planning, multi-factor authentication, and supply chain security.
- The legislation holds top management directly and personally responsible for ensuring compliance with cybersecurity requirements.
- NIS2 introduces stronger enforcement mechanisms, including administrative fines of up to EUR 10 million or 2 percent of global turnover for essential entities. National authorities are also granted broader regulatory powers, such as the ability to conduct on-site inspections, audits, and security scans.
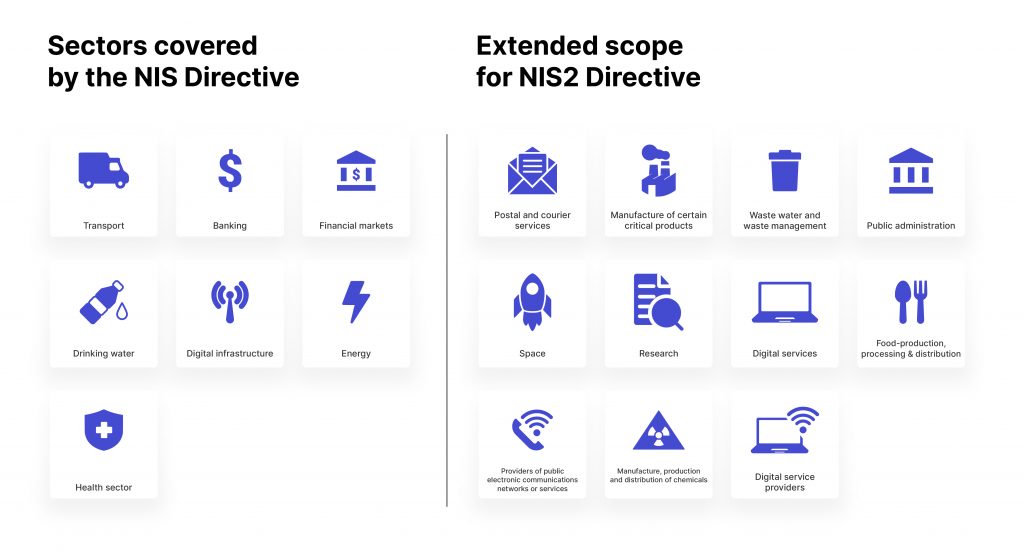
Broader Scope and Sector Inclusion
The revision extends significantly the scope of application of the NIS Directive by introducing new sectors subject to the legislation. These sectors are stratified into two main categories: highly critical and critical sectors. The distinction is based on the importance of these sectors for societal and economic stability, with highly critical sectors being subject to more intense regulatory scrutiny.
Stringent Incident Reporting Obligations
Under the NIS2 Directive, essential and important entities are required to notify the competent authority or national Computer Security Incident Response Team (CSIRT) of any incident of significant impact without undue delay. The reporting timeline foresees three reporting obligations:
- Within 24 hours, entities are required to provide an early warning
- After 72 hours, entities are required to provide a full notification report which includes an assessment of the incident mentioning its severity and impact as well as indicators of compromise
- After 1 month, entities are required to provide a final report.
Strengthening Resilience By Implementing Mandatory Security Measures
The NIS2 Directive imposes entities to take appropriate and proportionate technical, operational, and organizational measures to manage the risks that threaten the security of the networks and information systems. As such, the directive requires entities to implement the following measures:
- Risk Analysis and Information Systems Security: Entities must perform continuous risk analysis to identify and assess vulnerabilities in their information systems.
- Incident Response and Management: NIS2 mandates that businesses have well-documented incident response plans to promptly identify, contain, and mitigate cybersecurity incidents.
- Business Continuity Plan: Organizations must ensure that they have business continuity in place for critical services to continue or quickly resume operations in the event of a cyberattack or system failure.
- Personnel Security, Access Control, and Facility Management: NIS2 requires entities to establish strict personnel security protocols, including access control measures and facility management.
- Vulnerability Management: Businesses must proactively identify, assess, and mitigate vulnerabilities in their software and hardware systems.
- Cryptography and Encryption: NIS2 mandates the use of encryption and, when applicable, cryptography to protect sensitive data in transit and at rest.
- Supply Chain Security: Under NIS2, businesses must ensure their suppliers and service providers comply with cybersecurity standards by conducting risk assessments of third-party vendors and verifying that they implement proper security practices, preventing vulnerabilities from affecting the primary business systems.
- Cybersecurity Training: Employees, especially those with access to sensitive information, must undergo regular cybersecurity awareness and training programs.
- Multi-factor Authentication and Continuous Authentication Solutions: To strengthen access control, businesses should implement identity verification procedures like multi-factor authentication (MFA).
- Evaluation of Cybersecurity Effectiveness: NIS2 mandates continuous assessment and testing of cybersecurity measures, including through regular audits, security assessments, and reviews.
Expanding Corporate Accountability To Top Management
The NIS2 Directive requires top management to approve and oversee the implementation of cybersecurity requirements defined by the directive. Corporate management will also have to undergo frequent training on cybersecurity risk management. Most notably, top managers will be personally liable for NIS2 non-compliance, exposing them to penalties and a temporary ban from management roles. This level of accountability extends beyond technical teams, making cybersecurity a board-level concern.
Tougher Enforcement: Introducing Significant Penalties and Broader Regulatory Powers For National Authorities
Violations of risk management measures or incident reports can be penalized as detailed below:
- Essential entities can be penalized with administrative fines of up to EUR 10,000,000 or at least 2 percent of the total annual worldwide turnover in the previous fiscal year of the company to which the essential entity belongs, whichever amount is higher.
- Important entities can be penalized with administrative fines of up to EUR 7,000,000 or at least 1.4 percent of the total annual worldwide turnover in the previous fiscal year of the company to which the important entity belongs, whichever amount is higher.
Under NIS2 Directive, national authorities are granted expanded regulatory powers to ensure compliance with cybersecurity requirements, including through:
- On-Site Inspections
- Audits
- Security Scans
- Random Checks and Investigations
- Requests for Information and Data Access
Deadlines
| 17 October 2024 | April 2025 |
| By this date, Member States must transpose and publish the directive into their national legislations. As of 17 October, the majority of EU countries have not yet transposed the NIS2 Directive into national laws. | By 17 April 2025, Member States must identify and establish a list of essential and important entities under the NIS2 Directive. This list will determine which entities are in-scope and subject to the directive’s cybersecurity requirements. |
By this date, entities must register themselves in the applicable Member States where they provide services or are operational. From this point onward, in-scope entities must start applying the obligations of the directive.
How QuoIntelligence Helps You Stay Compliant with NIS2
QuoIntelligence offers comprehensive intelligence services that ensure compliance with NIS2’s requirements in key areas such as risk analysis, incident response, vulnerability management, and overall security strategy.
Our risk intelligence solutions enable proactive cyber threat management and continuous risk evaluation, aligning with NIS2 mandates. For incident response, we provide actionable intelligence that improves detection, response, recovery, and regulatory reporting. In vulnerability management, we offer updates on emerging threats and tailored patch management advice to help prioritize and address vulnerabilities based on risk exposure.
Leverage our real-time intelligence and strategic guidance to strengthen your organization’s resilience and meet NIS2’s stringent cybersecurity standards.


