As Donald Trump prepares for his second term as the 47th President of the United States, the cybersecurity landscape is poised for significant evolution. With a Republican majority in both the Senate and House, his administration is positioned to implement a swift and assertive policy agenda. While cybersecurity enjoys bipartisan support, ensuring some stability, organizations must prepare for nuanced shifts in priorities and an ever-evolving threat landscape.
In this analysis, we explore the projected cybersecurity policies under Trump’s leadership and assess the key global cyber threats from state actors and hacktivist groups, and identify the sectors most at risk.
Key Insights
Our main takeaways and key findings in this article include:
- Bipartisan support for cybersecurity suggests minimal policy shifts under a second Trump administration, with a focus on reducing government involvement in cyber regulation and combating disinformation.
- QuoIntelligence expects a rise in politically-motivated cyber activity, including hacktivism and state-sponsored attacks.
- Trump’s re-election is unlikely to significantly impact general cybercrime trends, with continued growth and increasing sophistication among cybercriminals.
- China is likely to increase economic espionage and may ramp up disinformation and infrastructure infiltration if tensions with the US rise.
- We expect Russian threat actors to maintain political espionage and cyberattacks supporting military operations, including potentially targeting European entities involved in aiding Ukraine.
- Iran and North Korea will likely continue political espionage and cyber operations to support their military and nuclear programs.
- Hacktivist groups, especially pro-Russia and pro-Muslim, are expected to continue targeting Western entities, regardless of diplomatic shifts.
Cybersecurity Policy Under Trump 2.0: Stability Amid Deregulation
One of the hallmarks of cybersecurity policy in the US is its bipartisan backing, meaning significant changes are unlikely. As such, Donald Trump’s second term will likely continue reinforcing the security and resilience of critical infrastructure to address increasing threats from Chinese and Russian APT groups. We expect the new administration to refine existing frameworks with a focus on deregulation and reduced government intervention in the fight against disinformation. Key anticipated trends include:
- Diminished Government Oversight in Cyber Regulation: Trump’s approach leans towards deregulation, favoring public-private partnerships to fortify cybersecurity rather than heavy-handed government mandates. This includes likely efforts to roll back Biden-era AI regulations, which the Republican platform criticizes as stifling innovation andimposing radical left-wing ideas on the technology’s development.
- Reevaluation of CISA’s Role: The Cybersecurity and Infrastructure Security Agency (CISA), created during Trump’s first term, may face reduced influence. Recommendations from conservative think tank Heritage Foundation’s Project 2025 suggest narrowing its mission, potentially limiting its involvement in election security and disinformation countermeasures claiming they amounted to censorship. Although Trump has not officially endorsed Project 2025, many contributors are closely aligned with his campaign, suggesting these recommendations may shape future policies.
- Threat Disruption To Focus on China and Iran: With Trump’s hardline stance on China, we expect an aggressive posture towards Chinese economic espionage, particularly in advanced tech sectors. Similarly, the Iranian regime is also likely to face increased scrutiny after recent reports indicated that an Iranian threat actor breached the Trump campaign and offered information to Democratic operatives.Conversely, public attribution of Russian cyber operations may become less frequent, as Trump’s rhetoric on Russia and Vladimir Putin suggests a potential shift away from „name and shame“ tactics employed by US intelligence agencies.
- Leadership Shifts: Leadership changes, such as replacing Biden-appointed officials like CISA Director Jen Easterly, are anticipated. This may lead to a recalibration of priorities, particularly in areas like disinformation and AI regulation.
Trump’s Re-election To Fuel Politically-Motivated Cyber Activity
The return of Donald Trump to the presidency is expected to bring significant shifts in US foreign policy, reshaping geopolitical dynamics. As a result, QuoIntelligence anticipates an uptick in politically-motivated cyber activity, such as state-sponsored cyber operations and hacktivism, targeting Western entities. In contrast, the broader cybercrime landscape is unlikely to experience substantial changes directly linked to Trump’s re-election, with continued growth in cyberattacks and an ongoing professionalization and adaptation among cybercriminals.
Adapting to Trump’s Return: Shifts in State-Sponsored Cyber Activities from China, Russia, Iran, and North Korea:
The evolution of state-sponsored cyber activity will likely reflect shifts in the global geopolitical landscape. China, Russia, Iran, and North Korea are expected to adapt their operations to safeguard their interests within this changing environment.
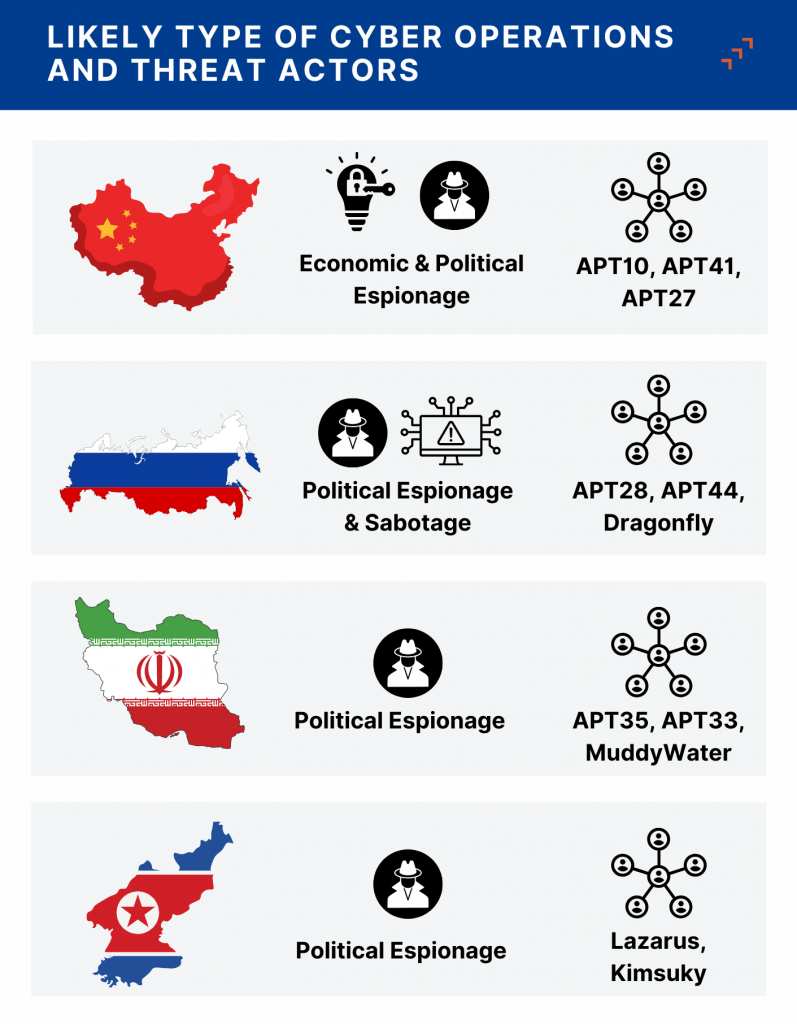
- China To Target Advanced Tech and Critical Infrastructure Amid Rising Tensions: China will likely intensify economic espionage efforts to mitigate the impact of expected increases in tariffs and export controls. APT groups such as APT10, APT41, and APT27 are expected to target companies and research institutions working on advanced technologies, including semiconductors, AI, and quantum computing. Additionally, Chinese political espionage may increase as China seeks to anticipate Trump’s foreign policy stance. Disinformation campaigns and potential infiltration of critical infrastructure may also escalate if Sino-American relations deteriorate further.
- Consistent Russian Cyber Activity: Russia is unlikely to scale back political espionage activities, despite possible warming of diplomatic relations with the US. Similarly, Russian state-sponsored threat actors will continue to support Russian military operations in Ukraine, which may include targeted cyberattacks against European entities involved in backing Ukraine’s war effort. Russian state-sponsored APT groups APT28 (aka Fancy Bear), APT44 (aka Sandworm), and Dragonfly would likely engage in such operations.
- Iran and North Korea To Focus on Espionage: Both Iran and North Korea are expected to continue political espionage efforts to gather intelligence on potential changes in US foreign policy toward their regimes. Additionally, Tehran and Pyongyang may also pursue cyber operations to advance their military and nuclear programs, securing leverage for potential negotiations with the US.
Projected Continuation of Anti-Western Hacktivism:
We expect hacktivists groups to continue to engage in disrupting activities against Western entities, reacting to anti-Western discourse and geopolitical developments. Distributed denial-of-service (DDoS) attacks are expected to continue to dominate due to their low technical barriers. While typically short-lived and preventable through anti-DDoS measures, these attacks can still cause significant financial and reputational damage to organizations with critical, public-facing assets, impacting their ability to serve clients.
- Continued Targeting of Western Entities By Pro-Russia Hacktivist Groups Amid Anti-Western Narratives: Pro-Russia hacktivist groups are likely to persist in cyberattacks against Western targets, fueled by anti-Western narratives. We expect this activity to continue even if diplomatic relations between the US and Russia improve, or if Kyiv and Moscow reach a resolution. The Kremlin is unlikely to shift away from the ideological discourse criticizing perceived Western decadence and immorality. Moreover, as Europeans may play a bigger role in supporting Ukraine in its war against Russia, European organizations will continue to be prime targets for pro-Russia hacktivist groups.
- Pro-Muslim Hacktivist Activity Responding to US Support For Israel: Given Trump’s strong support for Israel, pro-Muslim hacktivist groups may react to statements regarding the Middle East and unfolding events on the ground. These groups are expected to primarily target Israeli and US organizations. European businesses operating in the region and institutions from nations supporting Israel are also facing potential risks, although to a lesser extent.
Conclusions
- QuoIntelligence’s findings suggest that bipartisan support for cybersecurity in the US makes significant policy changes unlikely, creating a stable and predictable environment for cybersecurity strategies.
- Organizations in critical sectors, such as information technology, defense, and energy, as well as those operating in or near conflict zones, should actively prepare for heightened cyber risks stemming from shifts in the cyber threat landscape following Trump’s re-election.
- Companies should anticipate more sophisticated and persistent attacks from politically motivated adversaries, including state-sponsored groups and hacktivist actors.
- We anticipate European entities to face heightened risks from Russian APT groups and pro-Russia hacktivists, as European support for Ukraine’s defense efforts is expected to intensify to offset a potential US drawdown under a new Trump administration.