Threat Intelligence Snapshot: Week 7, 2026
Exchange URL Rule Failure Sparks Mass Email Quarantine, ZeroDayRAT Spyware, SSH Botnets and DPRK LinkedIn Fraud Expand Global Threat Landscape...
Mercury delivers Predictive Threat Intelligence powered by its AI-technology, supervised by a team of talented analysts, providing real-time insights into cyber and geopolitical risks. Now, it also includes Karla, our AI Cyber Threat Intelligence Agent, bringing intelligence to life through interactive, contextual, and human-like conversations.
Our AI-driven analytics, enhanced by Karla, anticipate threats before they materialize, offering client-relevant intelligence reporting, automated risk scoring, and tailored threat insights available 24/7.

Mercury maintains 22,000+ intelligence tickets analyzed by our Intelligence Analysts for company relevance. It supports compliance with frameworks such as NIS2, DORA, and the Cyber Resilience Act (CRA) by delivering alerts on critical vulnerabilities and potential attacks
Mercury offers 24/7 access to our curated Knowledge Base, customizable searches, ad-hoc reports, and on-demand support from Intelligence Analysts enhancing your cyber defense center with expertise and additional staffing when needed
Mercury offers intuitively presented, vetted Finished Intelligence allowing analysts to focus on operational tasks. It features mapped ATT&CK techniques, validated Indicators of Compromise, and suggestions to close security gaps

Raw intelligence processed
Information sources
Relevancy scoring is based on your location, industry, and technology stack
Information and source reliability ratings increase the confidence of insights
Access our Intelligence Analysts’ complete Knowledge Base and leverage on our API integration
At QuoIntelligence, our mission is to deliver actionable threat intelligence that helps organizations make informed security decisions. But don’t just take our word for it: hear directly from the companies and security teams who rely on our services.






Source: Gartner.com






Exchange URL Rule Failure Sparks Mass Email Quarantine, ZeroDayRAT Spyware, SSH Botnets and DPRK LinkedIn Fraud Expand Global Threat Landscape...
APT28 Targeting Central and Eastern Europe through CVE‑2026‑21509 Exploitation | UK Opens First Investigations Over Breach Of Cyber Sanctions
New Wave of Vishing Campaigns Against Identity Providers Targets Okta, Microsoft, Google, and Cryptocurrency Platforms | France To Ditch US...
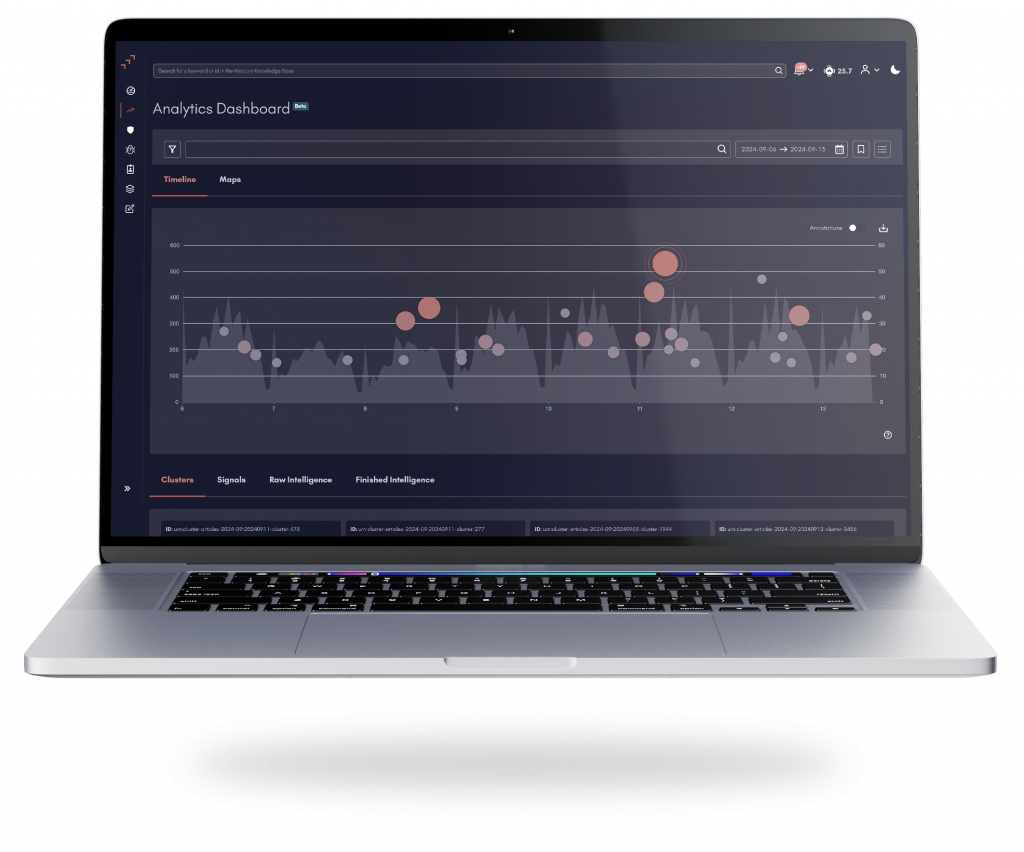
Discover how Mercury empowers your security strategy with Predictive Threat Intelligence. Our AI-powered platform, guided by expert human analysts, delivers real-time insights into cyber and geopolitical risks — before they escalate.
With Mercury, you’ll gain:
Proactive threat anticipation through advanced AI analytics
Client-relevant intelligence reports tailored to your environment
Automated risk scoring to prioritize actions
Strategic threat insights customized for your organization
Leave your details and we’ll be in touch to help you achieve your cybersecurity goals.
