This article first appeared as a contribution to the ECSO Cybersecurity Awareness Calendar. QuoIntelligence proudly bears the label “Cybersecurity Made in Europe” by the European Cybersecurity Organisation (ECSO).
Business travelers face a unique risk of being targeted by cybercriminals. Not only do they carry multiple devices like business phone, private phone, laptop and tablet. They also find themselves in unfamiliar places, away from the security of their company’s infrastructure, information technology, and potentially exposed to security threats.
This article collects our most valuable tips for your organization’s travel security model. In it we summarize how to keep yourself and your devices secure. Don’t miss out on our infographic.
Travel security risk – isn’t that just about VPN?
When asked about travel security risks, most people think of VPN software. Right?
While a VPN should undoubtedly be part of the protocol, it does not cover the extent of the topic. VPN-based security models work great – as long as everyone is using the VPN software as they should.
However, VPNs can be difficult to use, especially on mobile devices. Often, they hamper employees’ ability to work efficiently because they either slow the device down or their connection is poor.
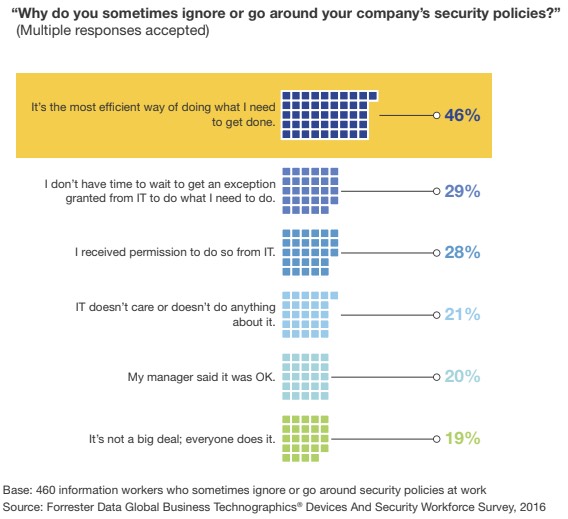
A study by Forrester (paid access only) about business travel risks showed that 46% of all study participants sometimes ignore their company’s security policies (like using the VPN software as soon as they leave the office) because “it’s the most efficient way of doing what I need to get done.”
So, what’s the alternative?
Are you enjoying this story? Subscribe to our newsletter to receive the lastest stories straight into your inbox.
Organizations should address travel security in multiple layers
Ultimately, travel risk security is about organizations doing their best to protect their data and their employees against state- and nonstate-sponsored threat actors with malicious intentions.
Therefore, we recommend our clients to address their travel security multi-layered and in three phases: pre-, during- and post-travel. This way, organizations ensure that all potential risk layers are detected and approached over time.
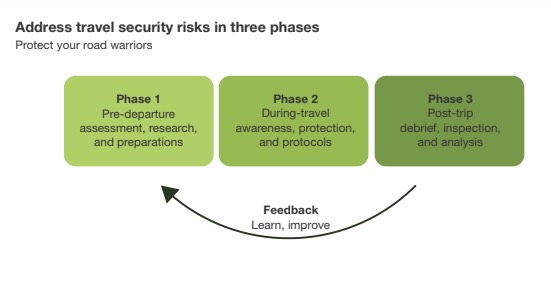
Before Travel: Do your homework
Before the journey begins, organizations should start researching and assessing the destination countries’ potential threats and risk levels.
We advise our clients to monitor the country’s risk fully. That includes any possible interest in your industry or product, which could motivate espionage activities.
Therefore, the pre-departure assessment should not only include the political and economic stability of the destination but should also consider the identity of the traveler itself, the industry sector, and the role they work in.
Fully monitoring a countries’ travel risk means assessing state-sponsored threat actors, relevant national regulations, and domestic policies to prepare for potential risks and understand how to minimize them.

Subscribe to our newsletter to receive the most recent news, research and analysis straight into your inbox.
Implement technological preparations
The next step in your pre-travel framework should be implementing device management and ensuring secure communication methods between employee and employer.
We suggest enabling full disk encryption and VPN access for all devices, disabling USB ports, installing IT management tools that allow remote wiping if needed, and backing the device before departure.
Finally, make sure to educate your employees about the travel risk precautions you’ve made. Enable them to master the technology you’ve equipped them with and help them recognize unusual behaviors.
Ultimately, the success of your travel risk security framework is determined by how well you manage your people, not just their devices.
During Travels: stay vigilant of your surroundings
In 2017, the US temporarily banned electronic devices beyond the size of a mobile phone on carry-on luggage on flights to and from the Middle East. Suddenly, it was not possible anymore to take your laptop into the cabin with you, imposing a real security gap that forced organizations to adapt their travel policies quickly.
Even though the ban has been lifted just a few months later, this example showcases the importance of being prepared for all eventualities during traveling. By that, we don’t just mean the more obvious precautions like using a VPN, staying away from free Wi-Fi or charging stations, backing up your data, and packing a burner device.
The riskiest and most dangerous situations still involve interactions with other people. Most business travel accidents happen beyond device access due to miscalculated human or other surrounding threats. Pickpocketing, theft, or spilling sensitive business information in a conversation with a stranger are often underestimated risks.
Travelers need to stay vigilant about the context of their surroundings and their interactions with third parties, e.g., when crossing borders. Border agents or other government officials often have extensive powers and might even ask you to unlock your phone for them to access it.
Therefore, we recommend considering government and border policies before arrival at the foreign destination. Organizations should advise the business traveler on border procedures specific to the country.
Furthermore, companies should encourage their employees to always carry their devices on them when traveling – even for a drink at the hotel bar.
After Travels: De-Brief, even if everything went smoothly
When arriving back in the office, it is crucial to de-brief with the employee. Even if the employee does not report back about any unusual situations, we recommend running through a list of security actions to eliminate all risks to security.
Make sure to change all passwords and if your organization’s capabilities allow it, run forensic tests with all devices that traveled. Ask your employee about any suspicious behavior on their trip. Did any strangers approach you? Were you asked to hand over your mobile phone or laptop at the border?
Last but not least: Update your policies according to your de-briefing interview. Anything they said might be helpful for the next business traveler.
Update your travel policies
Cybersecurity incidents, like data breaches or espionage, are evolving at an enormous speed. Consequently, make sure you have a good understanding of how policies need to be adapted over time.
When in doubt, request support from professionals who update your travel policies accordingly to continuous regulatory and geopolitical changes.
At QuoIntelligence, we dedicate a full-service branch to travel risk security. Our team of geopolitical cybersecurity analysts constantly updates country risk profiles to include recent events that might impact your travel, updated regulations affecting your destination, and recommended policy to minimize risks.





