In October, the International Committee of the Red Cross (ICRC) released for the first time rules of engagement for hacktivists amid conflicts. This includes eight international humanitarian law-based rules for “civilian hackers” during war and four obligations for states to restrain them.1
The creation of such rules is a response to the development of hacktivism in the wake of the war in Ukraine. In a previous blog, we forecasted an increased politization of the threat landscape compared to 2022, leading to a rise in hacktivist activity. ICRC finds this trend worrying for three reasons:
- Hacktivism causes harm to civilian populations by targeting civilian objects. Notably, the Red Cross provides the example of KillNet’s attacks against hospitals. Previous reports have shown that the healthcare sector was particularly targeted by pro-Russia hacktivist groups.2 3
- By involving themselves in a conflict, hacktivists expose themselves to cyber or physical attacks. They also make themselves liable for their participation in hostilities.
- Hacktivism in the framework of a conflict is blurring the lines between civilians and combatants, undermining the founding principle of humanitarian law.
The ICRC’s Rules of Engagement
In this context, the ICRC argues that international humanitarian law should apply to hacktivists acting in the context of an armed conflict, through the adoption of the following rules of engagement:
- Do not direct cyberattacks against civilian objects
This includes civilian infrastructure, public services, companies, private property, as well as civilian data. - Do not use malware or other tools or techniques that spread automatically
and damage military objectives and civilian objects indiscriminately. - When planning a cyberattack against a military objective, do everything feasible to avoid or minimize the effects your operation may have on civilians
This rule entails assessing all potential effects of a cyberattack beforehand and refraining from launching it if the harm to civilians risks to be excessive. - Do not conduct cyber operations against medical and humanitarian facilities
- Do not conduct cyber attacks against objects indispensable to the survival of the population such as drinking water installations, or that can release dangerous forces — dams, nuclear electrical generating stations, or chemical plants, etc.
- Do not make threats of violence to spread terror among the civilian population
This point refers to disinformation operations aiming at diffusing terror. - Do not incite or facilitate violations of international humanitarian law
- Comply with these rules even if the enemy does not
The ICRC’s Obligations for States
The ICRC also released four obligations for states based on the UN Group of Governmental Experts’ recommendations on international law and norms of responsible state behavior which says: “States must not use proxies to commit internationally wrongful acts using ICTs, and should seek to ensure that their territory is not used by non-State actors to commit such acts”.4
- If hacktivists act under the instruction, direction or control of a State, that State is internationally legally responsible for any conduct of those individuals that is inconsistent with the State’s international legal obligations, including international humanitarian law.
- States must not encourage civilians or groups to act in violation of international humanitarian law.
- States have a due diligence obligation to prevent international humanitarian law violations by hacktivists on their territory.
- States have an obligation to prosecute war crimes and take measures necessary to suppress other international humanitarian law violations.
Hacktivist Reaction to the ICRC Announcement
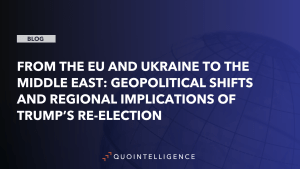
Following the ICRC’s announcement, QuoIntelligence saw some pro-Russia hacktivist groups reacting to the proposal. Notably, on 6 October, KillMilk — founder of KillNet — announced in a Telegram post that KillNet will comply with the ICRC’s rules.
Screenshot of KillMilk’s Telegram post on 6 October, translated automatically
This announcement came after the BBC reported on 4 October that KillMilk allegedly told the media outlet that he planned to ignore the rules.5 KillNet even shared the article in its Telegram channel the following day. This likely shows hacktivist groups struggled at first to address the ICRC’s proposal.
Since the beginning of the conflict, QuoIntelligence has observed KillNet and hacktivist groups involved in the Russia-Ukraine conflict launching DDoS attacks against a wide range of organizations, both in the public and private sectors.
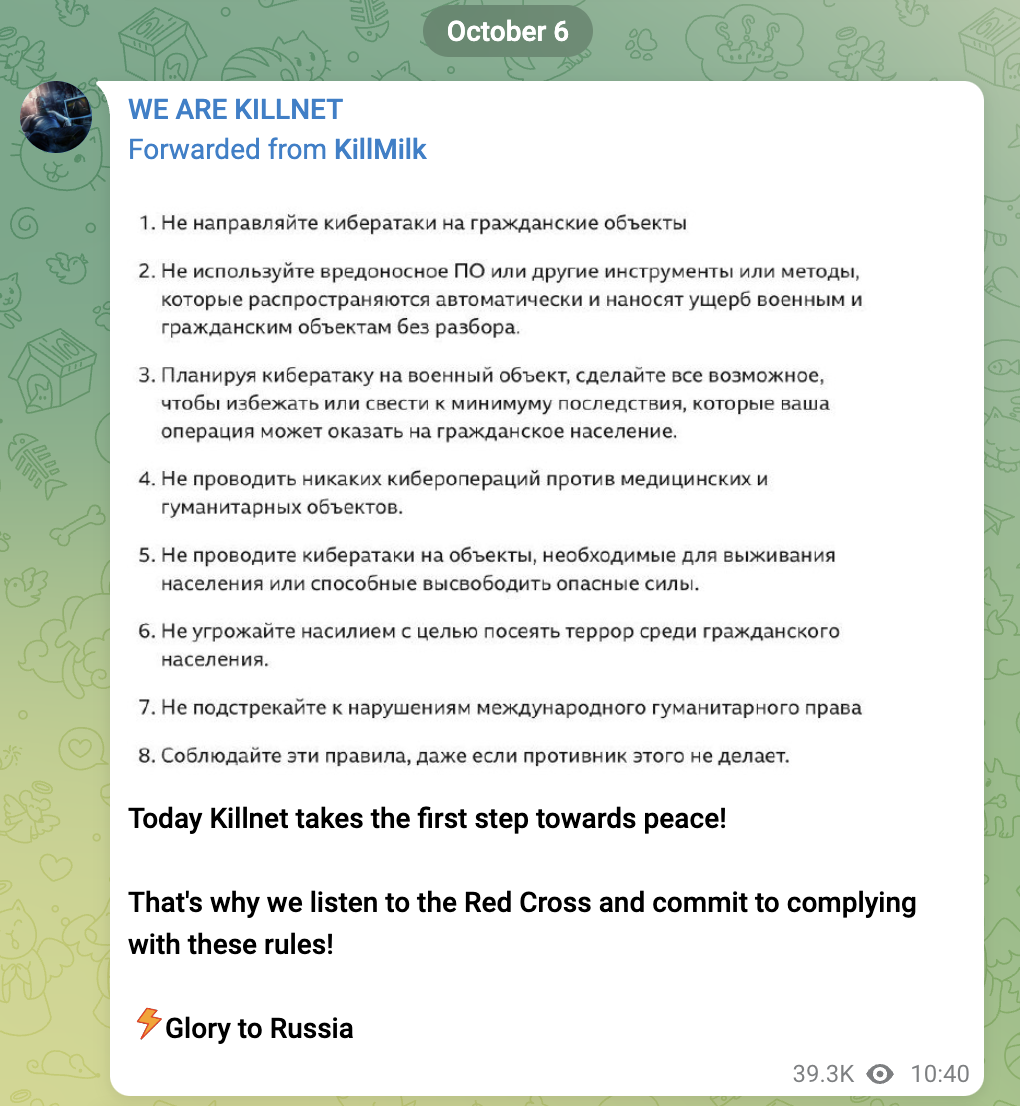
If governmental websites are the most targeted, ‘civilian objects’ are also heavily targeted.6 After KillMilk’s announcement that KillNet will commit to the ICRC’s rules, the group continued to target ‘civilian objects’. In international human rights law civilian objects include business enterprises and their properties, such as banks or transportation infrastructures.7 Civilian government services are also included in this category. KillNet and its subgroup “Legion” have launched DDoS attacks against banks or airports.
Screenshot of Legion’s Telegram post on 8 October, translated automatically
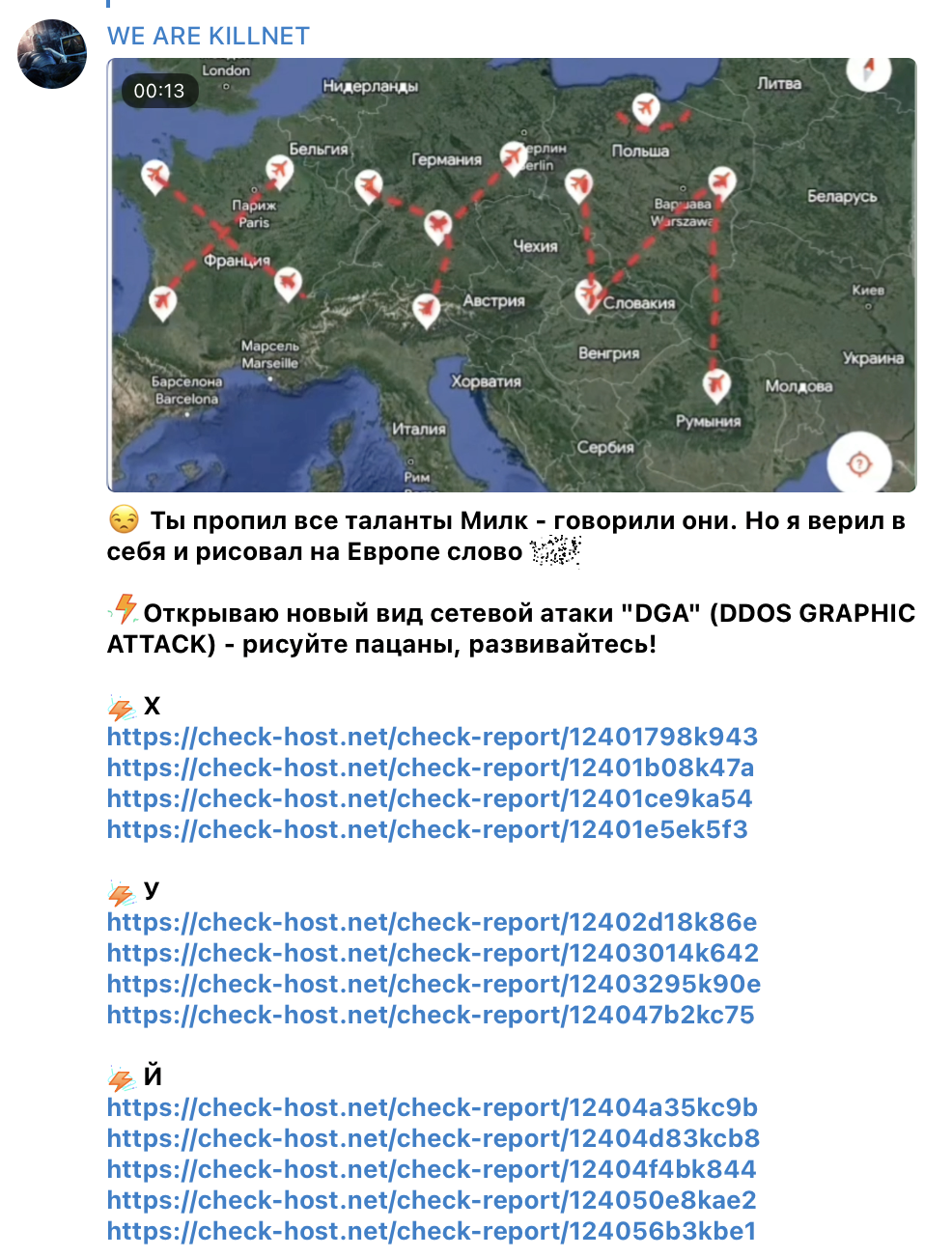
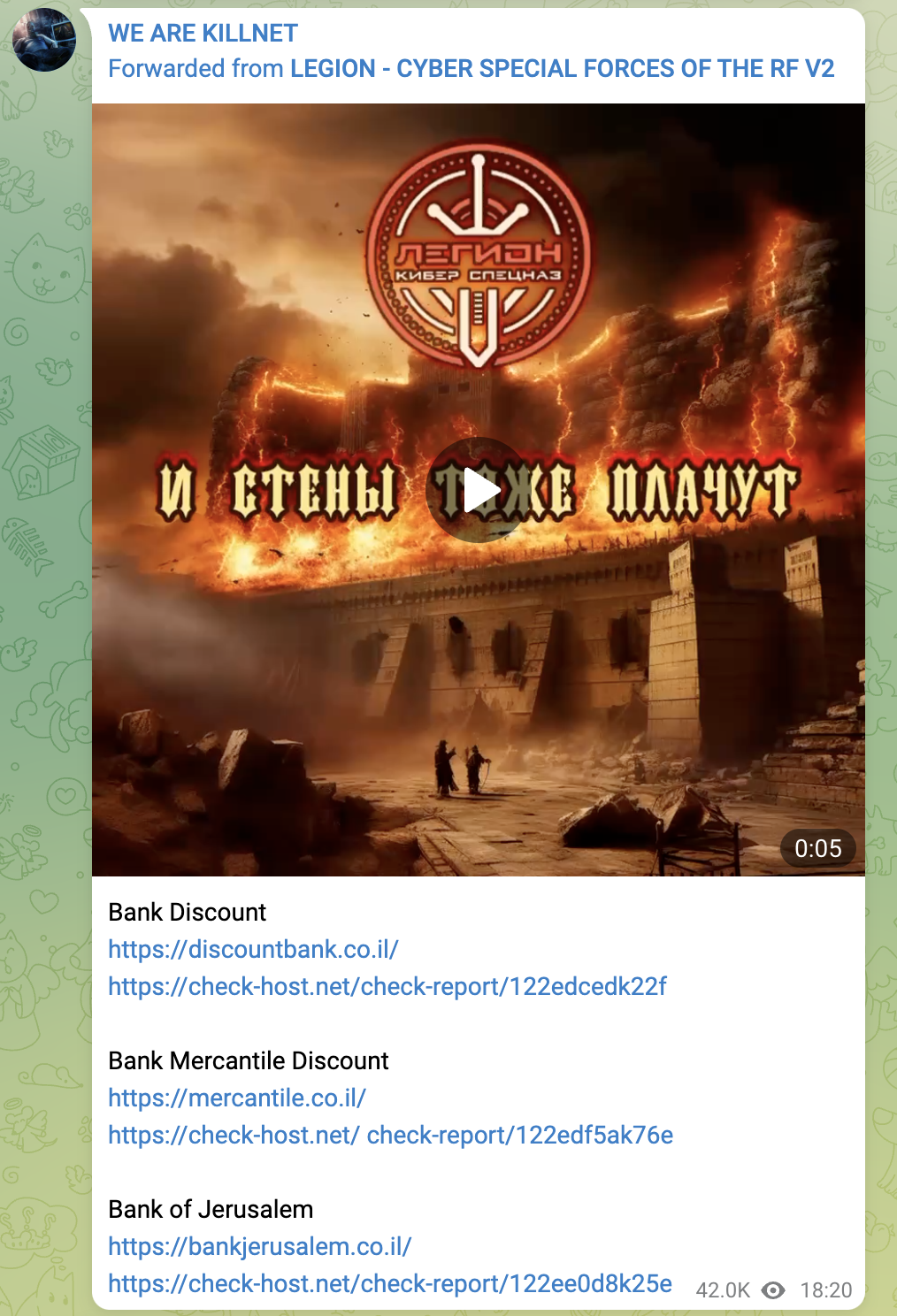
Screenshot of KillNet’s Telegram post on 11 October claiming DDoS attacks against various airports across Europe
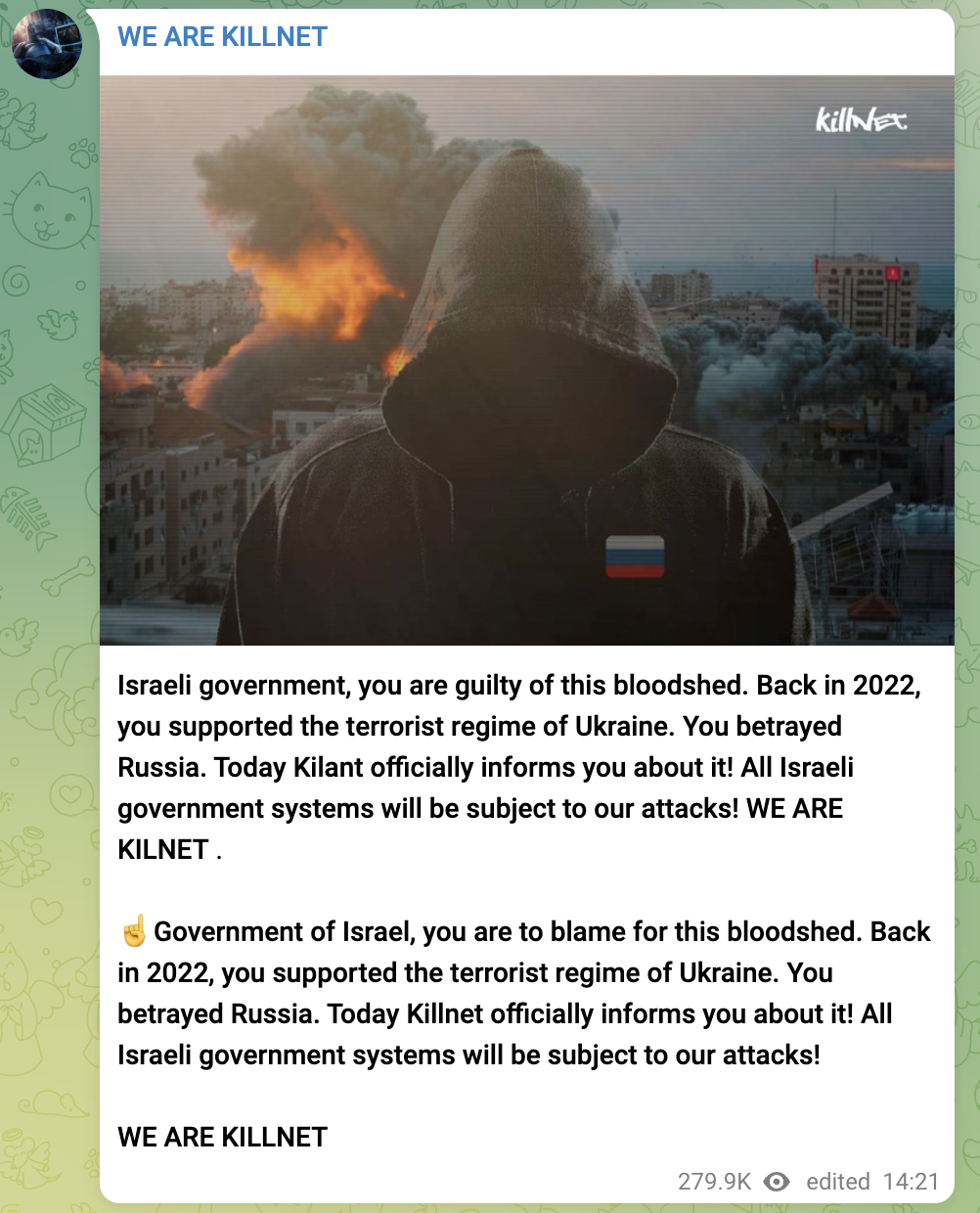
Screenshot of KillNet’s Telegram post on 8 October, translated automatically
Conclusions and Recommendations
QuoIntelligence assesses that despite announcements pledging to obey ICRC rules, the pro-Russia hacktivist group will highly likely continue to target “civilian objects”, including European companies. We assess that KillMilk’s declarations on the ICRC’s rules can be interpreted as another attempt to show off.
Regarding the obligations the Red Cross issued for states, no government has made any public statement acknowledging or commenting on them. Given the lack of enforcement in international humanitarian law, it is very probable that states will continue to sponsor hacktivist groups. Resorting to cyber proxies enables them to generate a climate of anxiety among their adversaries at a relatively inexpensive cost, while benefiting from plausible denial.
QuoIntelligence assesses that conflicts will increasingly translate into operations in cyber space, from grassroots hacktivist groups but also state-sponsored attacks. European medium-size companies will remain interesting targets for hacktivist groups. As such, QuoIntelligence recommends organizations with public-facing services, especially with critical assets, to ensure they have a robust DDoS mitigation strategy to mitigate application-layer attacks.
Keep up to date
To keep up with the latest cyber and geopolitical threats, subscribe to QuoIntelligence’s Weekly Intelligence Newsletter, published every Thursday around 1900 CET.