With the Olympic Games Paris 2024 set to be one of the most significant sporting events of 2024, the cybersecurity community is preparing for a marked increase in disruption attempts, cyber-attacks, and nation-state involvement. Reflecting on past incidents, many organizations are proactively developing various incident response scenarios and updating their internal playbooks. Nevertheless, one persistent threat remains: fraudulent schemes targeting viewers worldwide.
December 2023 was the date QuoIntelligence saw a noticeable increase in discussions related to the Olympics to be held in Paris, both on the Internet as well as the underground:
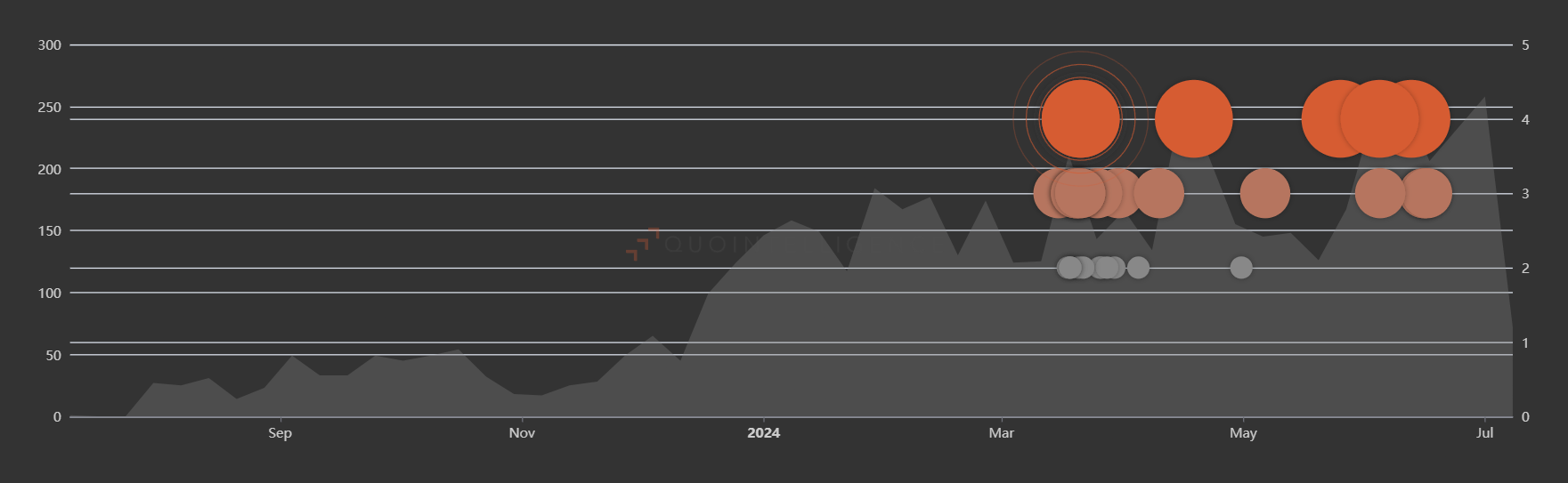
Figure 1 – Internal telemetries with mentions to the Olympics. Source: Mercury by QuoIntelligence.
The Olympics have always been used as a tool for geopolitical influence. This aspect of the games will be particularly significant this year due to the polarization of the international landscape, with conflicts such as the war in Ukraine and the Israeli-Palestinian conflict. In March, the International Olympic Committee decided to ban Russian and Belarusian athletes from participating in the games under their nation’s flags. This move further positions the Paris 2024 Olympics in the geopolitical arena and increases the likelihood of diplomatic tensions, as well as state-sponsored and hacktivist attacks against the organization of this sporting event.
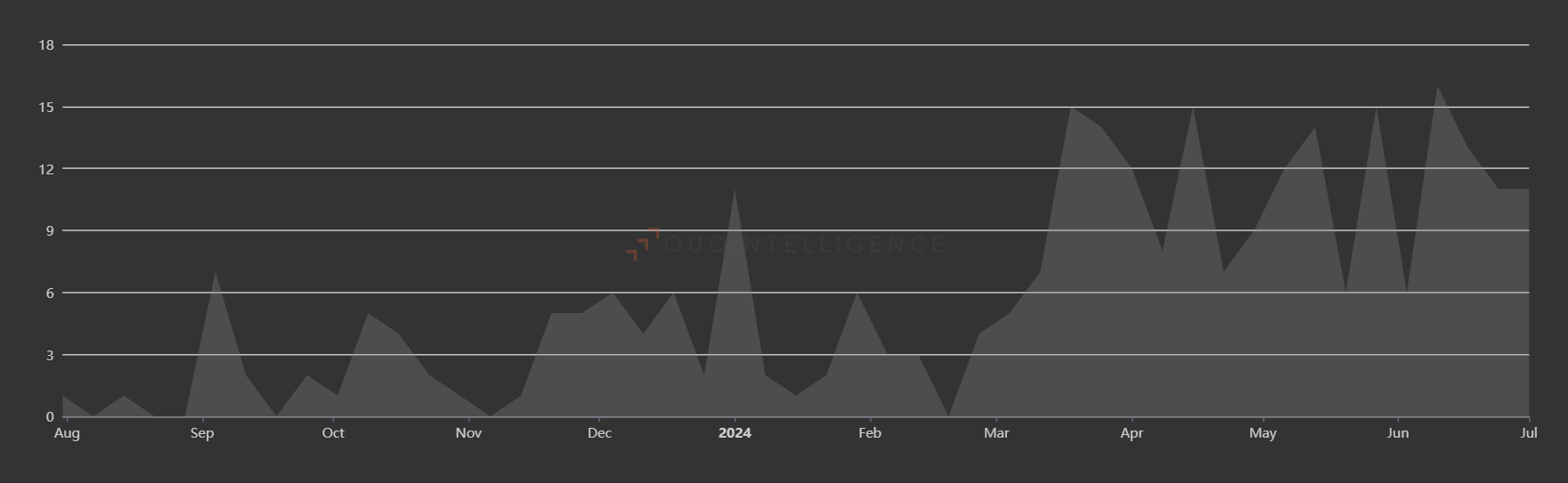
Figure 2 – Internal telemetries categorized as “Diplomatic Tensions”. Source: Mercury by QuoIntelligence.
This article examines an ongoing, yet undetected, fraudulent campaign internally tracked as Ticket Heist directed at Russian-speaking users, several Eastern European countries and as well as English-speaking individuals for specific sport events. Additionally, there is an outlier detection targeting English-speaking, Chinese-speaking, and Russian-speaking individuals seeking to purchase tickets for the Olympics. QuoIntelligence initiated an investigation after identifying multiple domains impersonating the official ticketing website of the Olympics. Through detailed analysis, we uncovered a broader network of 708 fraudulent domains that have been active since 2022, with their activities escalating throughout 2023 and maintaining a steady pace into 2024 towards sporting events and festivals.
Key Findings
Our main takeaways and key findings in this article include:
- As of July 2024, QuoIntelligence identified 708 domains linked with Ticket Heist campaign targeting mainly Russian-speaking individuals across the globe.
- The Olympic Games Paris 2024 and UEFA EURO 2024 events are at the highest level of risk at the time of reporting given multiple domains part of Ticket Heist luring users into buying tickets from untrusted and unofficial platforms.
- The impacts of such campaign are multifaceted, impacting both individuals and event organizers with financial losses, reputational damage and loss of trust.
- The fraudulent ticket sales extend beyond sporting events to various activities, including musical festivals featuring famous musicians.
Initial Pivoting Point: the Olympics
Given the rising number of fraudulent activities targeting sporting events, particularly the Olympics this year, QuoIntelligence has initiated an investigation to catch attackers setting up their infrastructure to lure victims.
After several weeks of consistent monitoring of commonly used keywords in domain registrations, we observed an intriguing pattern of keywords and IPs used to resolve these domains. This analysis led to the identification of our first true positive, which became the cornerstone of uncovering this fraudulent campaign:
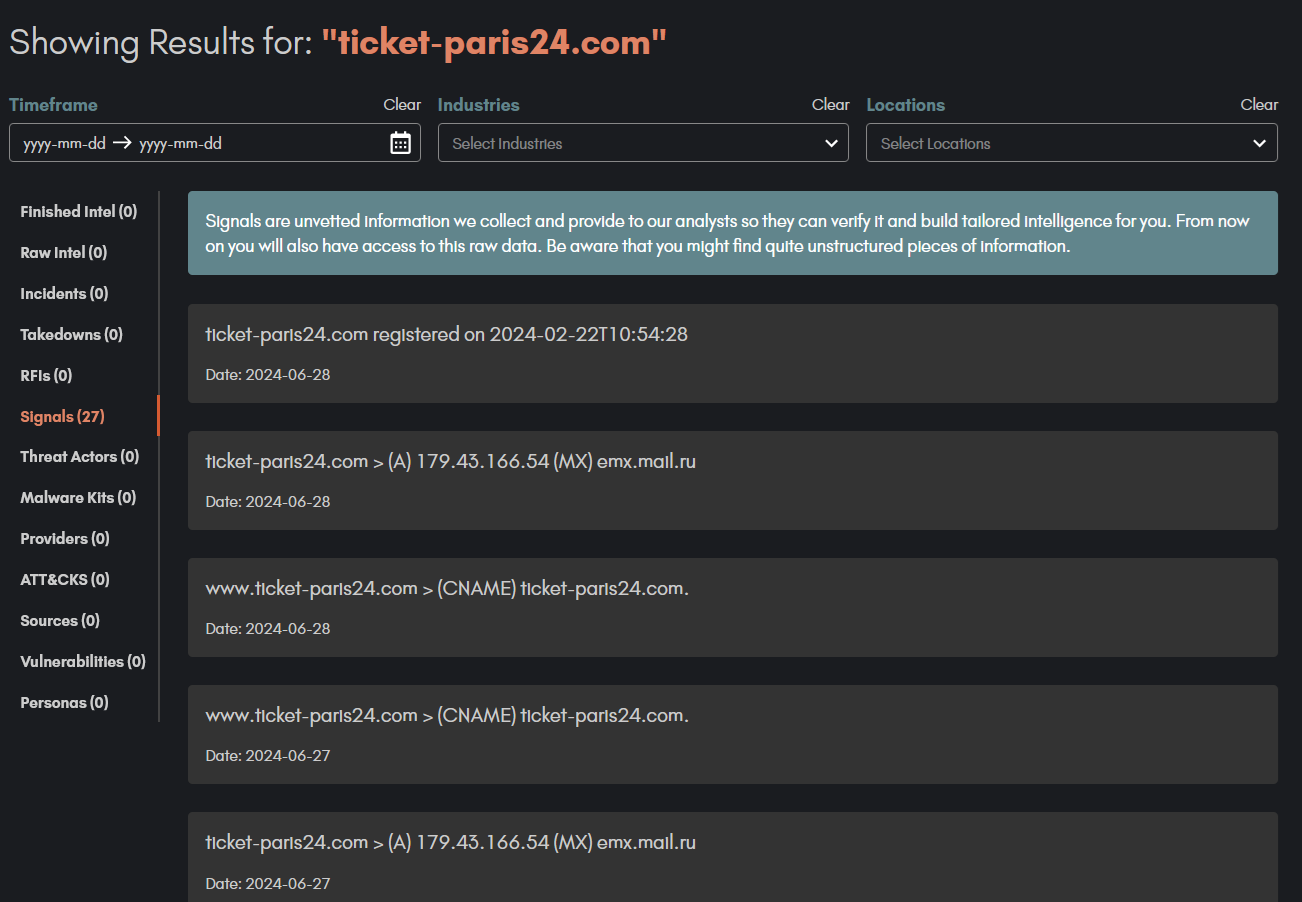
Figure 3 – First detection date of the domain ticket-paris24[.]com. Source: Mercury by QuoIntelligence.
At the time of detection, the domains ticket-paris24[.]com and its clone tickets-paris24[.]com were hosting a highly convincing website that allowed users to purchase tickets for their preferred events during the Olympics, select their preferred seats, and choose accommodation in Paris. Despite minor spelling and grammar mistakes, likely due to direct translation from Russian to English, the website and its user experience were comparable to those of a high-end site. The sophistication observed in these fraudulent websites was unexpected, suggesting a high level of motivation and meticulous attention to detail by the attackers behind this campaign. This indicates their intent to maximize the success of their fraudulent activities targeting fans.
Upon visiting the websites, users were greeted with a landing page inviting them to scroll down and select their desired event to purchase tickets for. This initial interaction was designed to appear legitimate, encouraging users to engage with the site and proceed with their ticket selection:
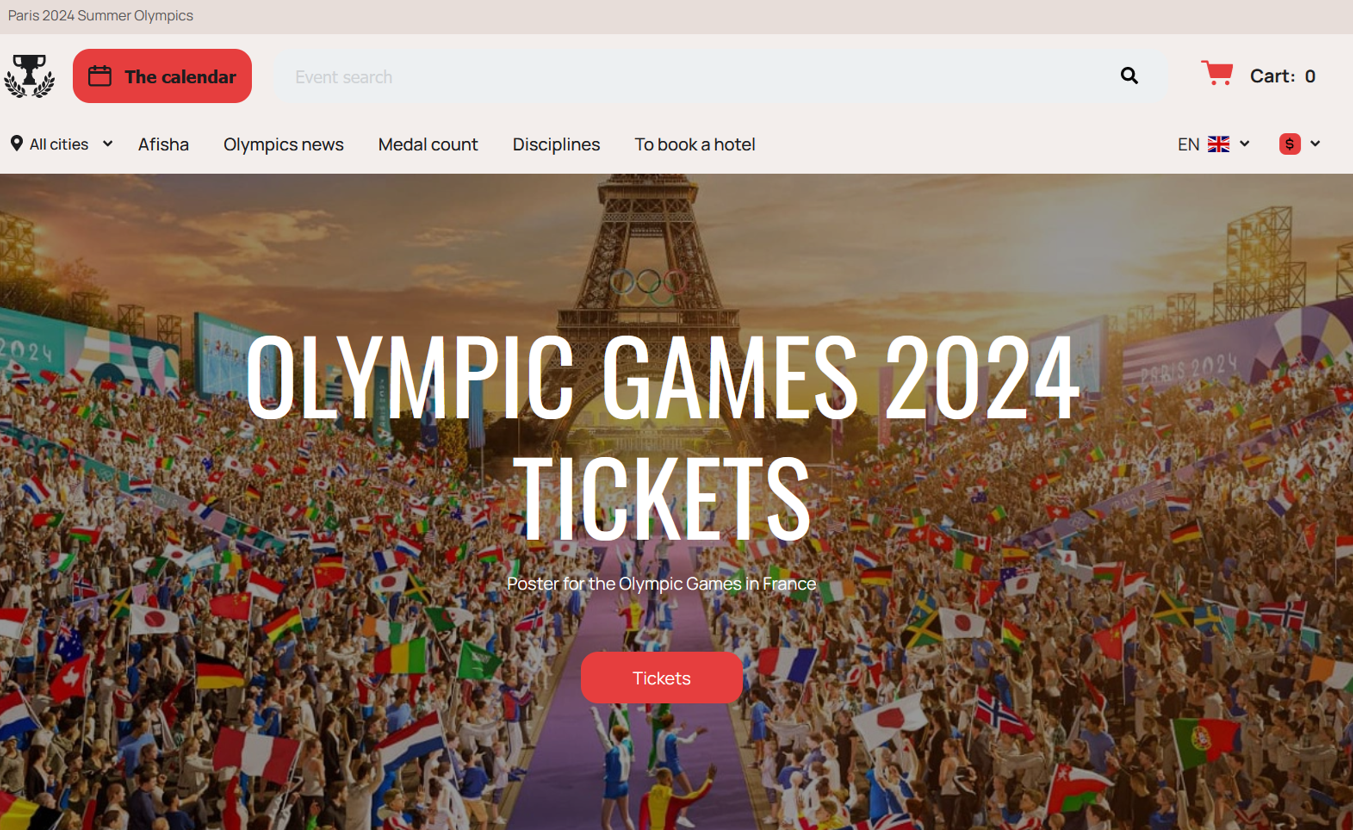
Figure 4 – Landing page of the domain ticket-paris24[.]com. Source: QuoIntelligence.
While these two websites appeared to be specifically targeted and meticulously crafted for the Olympics, boasting high-quality design, we later discovered that Ticket Heist employed the same UI framework. The differences between the sites were minor, mainly involving variations in content and the languages used within the websites
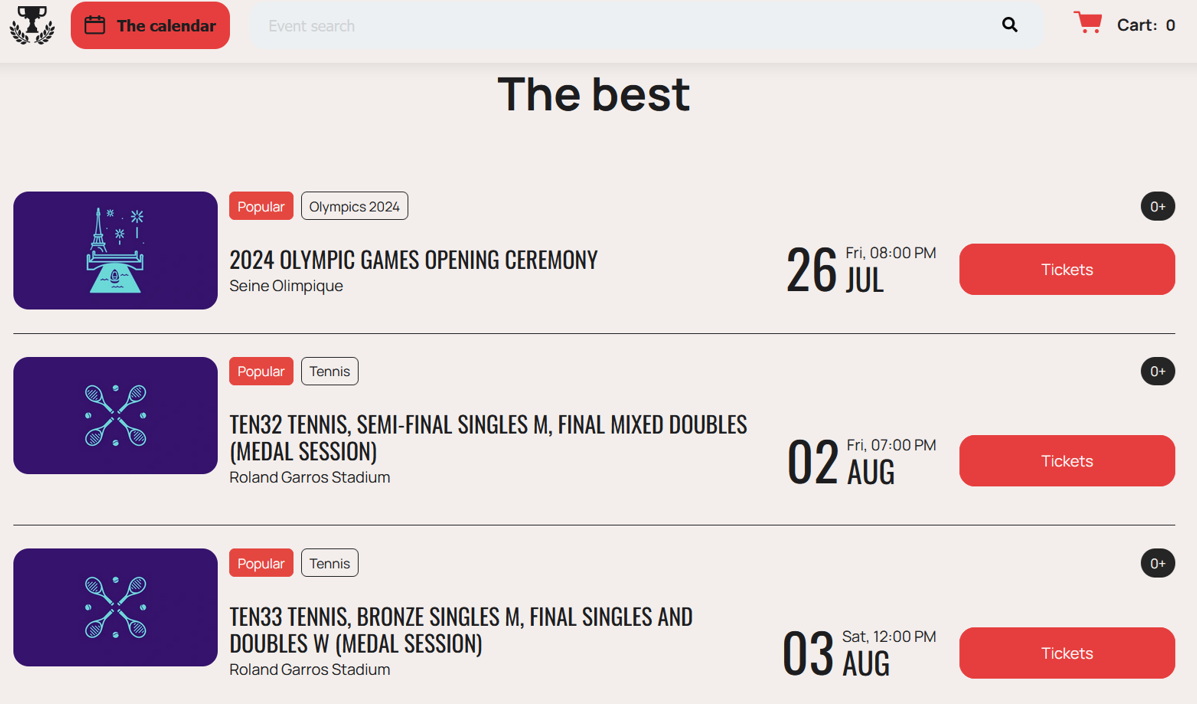
Figure 5 – Tickets available to be purchased on ticket-paris24[.]org. Source: QuoIntelligence.
The content and presentation of these websites varied depending on the event the attackers targeted. However, the footer, forms, and privacy policy pages remained strikingly similar, if not identical, across all sites. These sections featured identical copy-and-paste mistakes and translation errors, indicating a possible common origin.
For example, within the privacy policy page, there is a reference to the publication date listed as 2 July 2019, same date found on most of the websites later discovered. However, the domain was only created on 22 February, and the first time both websites were scraped and indexed online was on 28 April where the content was not displaying a “404” HTML page. Similar minor mistakes are found in the footer of the websites, where the page “Events” remains untranslated and appears as the Russian word “Afisha”.
Although there is no direct correlation between the launch of the official ticket sales and the fraudulent website, we identified that on 17 April, over 250,000 tickets were made available on the official website. It is unclear whether the authors of the fraudulent website released their content in late April to exploit the official press release about ticket discounts or if this timing is purely coincidental.
To gather additional information and potentially unmask the attackers, QuoIntelligence decided to impersonate a user attempting to purchase a ticket for a random event and track the website’s behavior with various inputs, both valid and invalid. Since the fraudulent websites utilized Stripe as their payment system, it became apparent that the attackers’ goal was not to steal credit card information, but rather to approve the transaction if the victim had sufficient funds to buy the ticket, leaving the victim unresponsive to further requests.
Using a virtual card created specifically for this purpose and charged with EUR 1, no transactions were successful, as expected. This reinforced our initial hypothesis that the attackers are intent on completing the transaction only when the card has sufficient funds.
However, an interesting detail emerged during our analysis: a favicon and a company name associated with the website that appeared to have little to do with its intended purpose:
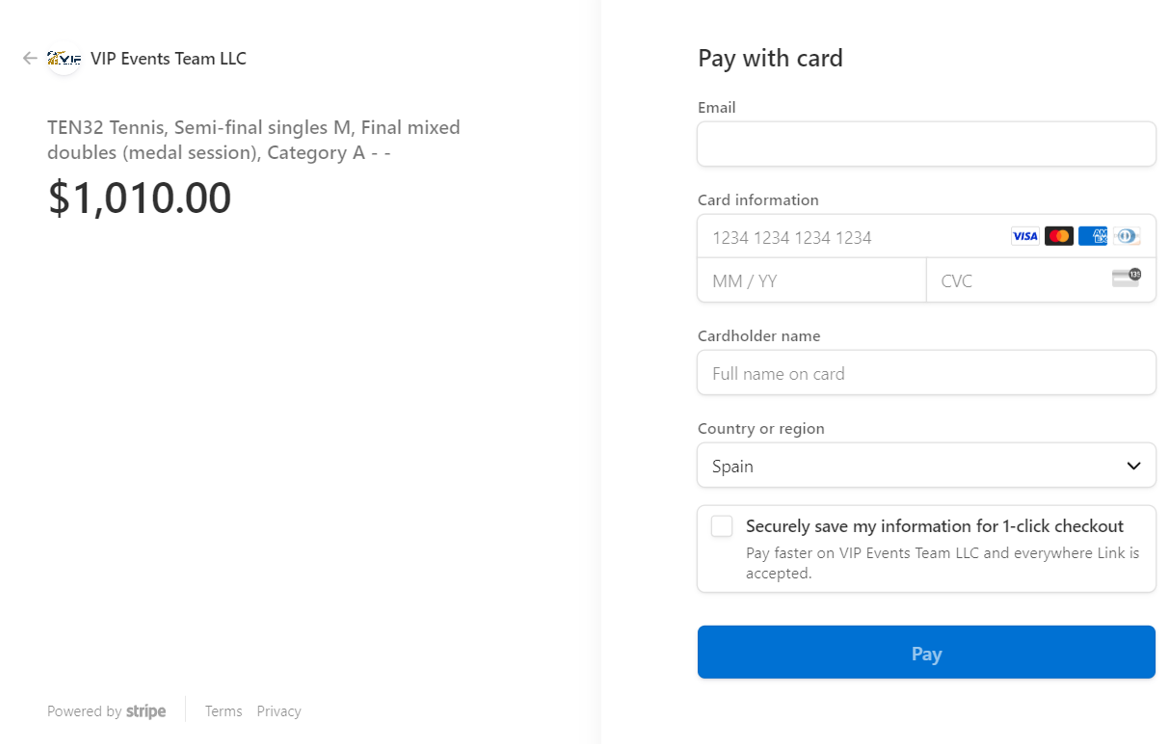
Figure 6 – Redirection to Stripe’s payment page. Source: QuoIntelligence.
In Figure 6, the company associated with the fraudulent website, VIP Events Team LLC, is currently active and was legally formed on 26 November 2021. However, the company has never had an active website. At the time of analysis, the website vipeventsteam.com displayed a WordPress database error and has not been scraped since the company’s creation. The domain was registered on the same day the company was formed. There are no mentions of VIP Events Team LLC on Google, social media, TrustPilot, or any other available OSINT sources. This company is likely based in the US because the icon used on the Stripe payment page matches the one found on the US company registration page.
Interestingly, although the company appears to be US-based, specifically in New York, the “Contact Us” page of the ticket-paris24[.]com website lists the company behind the fraudulent site as being located in Georgia:

Figure 7 – Contacting information in the footer and “Contact Us” page. Source: QuoIntelligence.
Lastly, a comparison of ticket prices between the official Olympics website and the detected fraudulent websites reveals significant inflation on the latter. For example, a random event and seat location on the official website could cost less than EUR 100, whereas the same tickets and locations on the fraudulent websites were priced at a minimum of EUR 300, often reaching EUR 1,000; a preliminary analysis of the fraudulent websites showed that no tickets were priced below EUR 300, further indicating the fraudulent nature of these sites.
Given the extracted information and the fact that selling tickets outside the official website is considered fraudulent based on the event’s Terms of Service (ToS) and Frequently Asked Questions (FAQs), coupled with the numerous inconsistencies detected within the website, we conclude that the likelihood of these websites being malicious and used for fraudulent activities is very high.
Pivoting on the Infrastructure
Based on internal telemetry from this campaign, all detections pointed to a single IP address: 179[.]43[.]166[.]54, making the mapping and pivoting from this indicator straightforward. Although each website had unique SSL certificates, making certificate-based pivoting unfeasible, we noticed a consistent pattern in the domain and unique subdomain structures of the detected sites. Specifically, the subdomains often included:
- jswidget
- widget-frame
- widget-api
By combining various pivoting methods, such as analyzing these subdomain patterns, DNS records, and common JavaScript files across the websites, we identified 708 domains with active websites created between 2022 and 2024. On average, 20 new domains were created monthly, with a notable spike of over 50 domains in November 2023 and more than 98% of the domains are classified as clean by crowdsourced analyzers and vendors at the time of reporting.
Lastly, all the domains are being managed through Cloudflare although the traffic is not being proxied into their infrastructure.
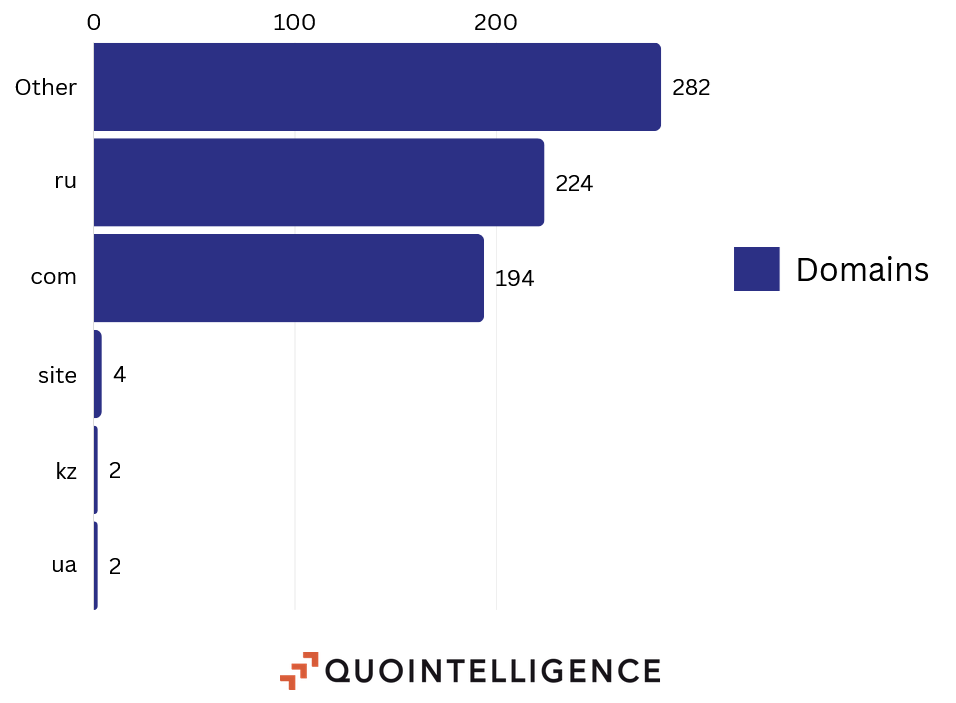
Figure 8 – Domains grouped by TLD part of Ticket Heist campaign. Source: QuoIntelligence.
Identified Victimology
Identifying the exact victimology is challenging due to limited visibility into the affected victims. However, based on the domain registrars used and the website content, we can roughly estimate which countries or groups of individuals are more likely to be targeted.
The majority of the websites primarily target Russian individuals worldwide, potentially exploiting their need to bypass sanctions to access certain events. Additionally, other potential victims have been identified in neighbouring countries such as Estonia, Lithuania, Latvia, and Kazakhstan.
Some outliers in Ticket Heist were detected where the attackers decided to take advantage of the UEFA EURO 2024 football event, with multiple English-language websites offering tickets for this event:
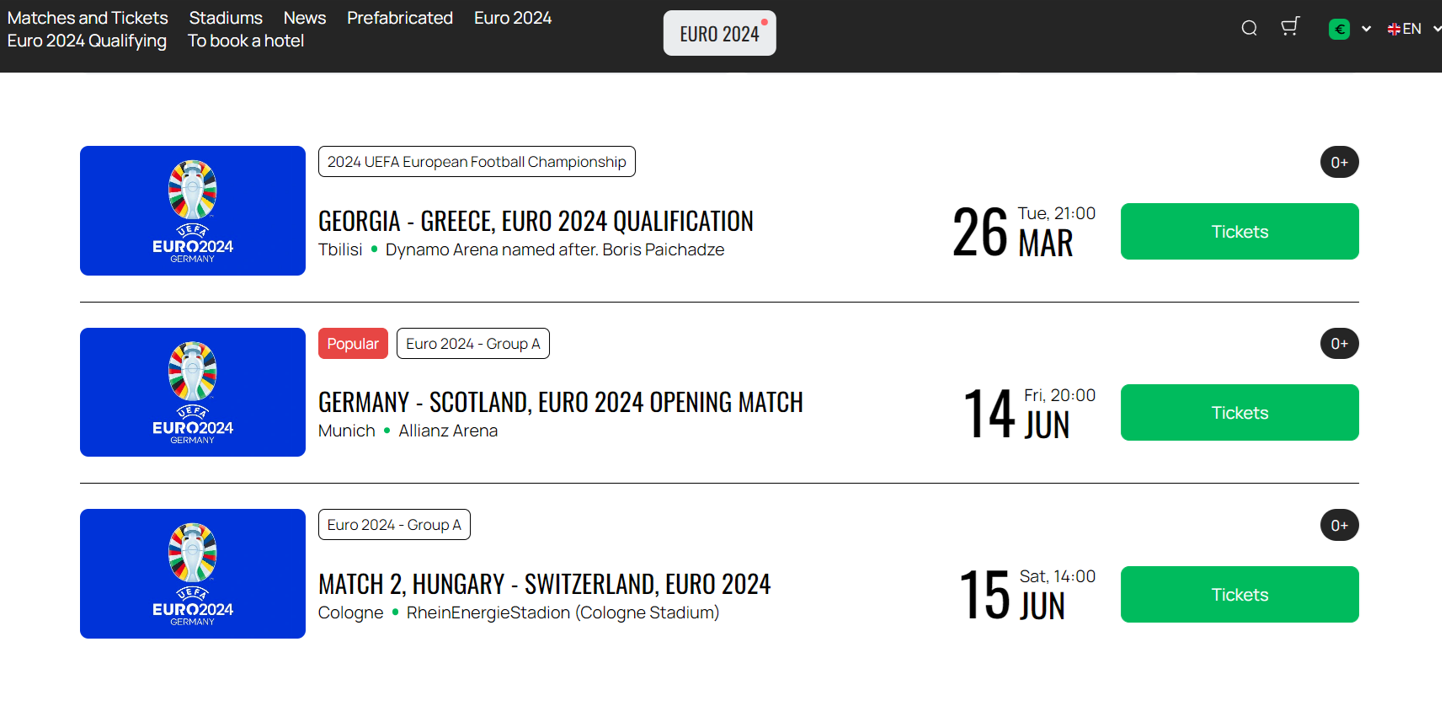
Figure 9 – Tickets to UEFA EURO 2024 football matches on multiple fraudulent websites. Source: QuoIntelligence.
The fraudulent ticket sales extend beyond sporting events to various activities, including musical festivals featuring famous musicians, targeting also the following individuals or groups:
- Twenty One Pilots
- Iron Maiden
- Bruno Mars
- Ludovico Einaudi
- Metallica
- Rammstein
Conclusions
The impact of similar campaigns is always multifaceted and difficult to track, as they affect both individuals and organizations. More commonly, one or a combination of the following scenarios is likely to occur if these campaigns are successful:
- Financial Losses: Individuals who fall victim to these scams suffer direct financial losses from purchasing fake tickets. This impacts their personal finances and erodes trust in online transactions.
- Reputational Damage: Event organizers and official ticket vendors can suffer significant reputational damage. The association with fraudulent activities can diminish consumer confidence in their brand and services, potentially reducing legitimate ticket sales.
- Loss of Trust in Major Events: Continuous fraudulent activities targeting major events can erode public trust in the security and integrity of such events. This can result in decreased attendance and participation in future events, affecting the overall success and economic benefits they bring to host cities and countries.
Monitoring the evolution of similar campaigns is the only way to effectively detect and dismantle these fraudulent networks. The trend of exploiting major events for financial gain is likely to persist and may never fully stop, necessitating continuous adaptation of defensive strategies. Proactively gathering and profiling emerging threats and trends will be crucial. While methods may evolve over time, cybercriminals will always find ways to exploit users.
The cybersecurity community can find all the Indicators of Compromise (IOCs) that QuoIntelligence extracted here on our GitHub repository.
Research by Andrei Moldovan, Threat Researcher at QuoIntelligence.
Andrei brings extensive expertise in malware reverse engineering and criminology, backed by years of experience in a Security Operations Center (SOC). His passion for malware and offensive security drives him to shed light on unknown threats to combat cybercrime and cybercriminals.





