QuoIntelligence expects the fragmented eCrime ecosystem to drive mass-targeting cyberattacks, AI to consolidate its central role in social engineering attacks and disinformation, and geopolitical tensions to shape the 2025 cyber threats.
In early 2024, we released our annual outlook, in which we forecasted that cybercriminals would refined their extortion tactics, techniques, and procedures (TTPs) making more victims and avoiding detection. We also predicted that artificial intelligence technologies would mark 2024, with threat actors increasingly incorporating them in their attack chains. These trends were particularly prevalent throughout 2024 and we expect them to continue this year.
Looking ahead to 2025, QuoIntelligence predicts that the fragmented eCrime ecosystem will likely drive an increase in mass-targeting cyberattacks, with small and medium-sized businesses being the primary targets. AI is also expected to remain a critical tool for social engineering and disinformation campaigns. Meanwhile, geopolitical tensions will continue to shape the cyber threat landscape, with Russia likely focusing on upcoming elections in Germany and Poland, while China is expected to escalate economic espionage and intensify pressure on Taiwan.
Ransomware: Disruption, Fragmentation, and Proliferation Favoring Opportunistic Targeting
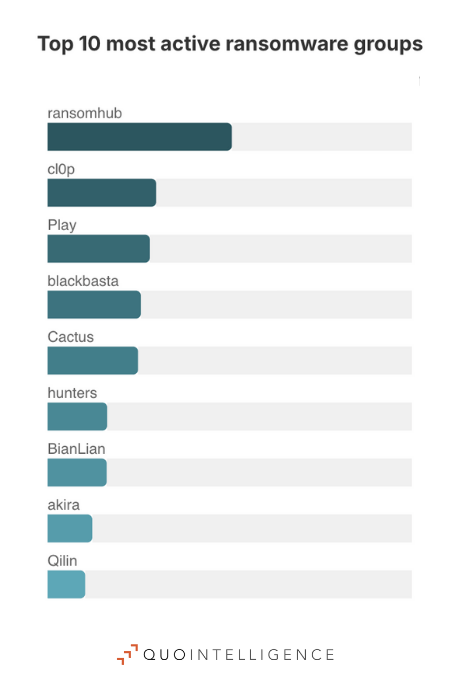
The ransomware ecosystem underwent a series of changes in 2024 with the disruption of the prominent Lockbit ransomware. Nevertheless, QuoIntelligence does not anticipate a decrease in ransomware activity in 2025 as threat actors will highly likely adapt to law enforcement actions. As such, we expect 2025 to be marked by new disruption of the ransomware ecosystem, further fragmentation and proliferation resulting in increased threats for small and medium enterprises. Despite likely law enforcement disruptions, we expect ransomware to remain the most prominent and impactful threat.
In February 2024, a coordinated international law enforcement operation—codenamed Operation Cronos—disrupted the LockBit ransomware group. This effort culminated in the shutdown of servers across multiple countries, several arrests, the freezing of more cryptocurrency accounts, and the extensive collection of data on LockBit’s network. Following this operation, the FBI announced the recovery of over 7,000 LockBit decryption keys.
Because LockBit had been the most active ransomware group until the end of 2023, its disruption significantly reshaped the ransomware landscape. Several affiliates, including highly skilled operators, likely broke away to form their own Ransomware-as-a-Service (RaaS) schemes or joined similarly mature groups such as RansomHub, Play, and Akira. In August 2024, law enforcement agencies took down Radar/Dispossessor—a group that had surfaced earlier in the year after LockBit’s disruption.
Within weeks of Operation Cronos, LockBit’s affiliates resumed posting victims on their Dedicated Leak Site (DLS), republishing data from previously targeted organizations, issuing exaggerated claims for media attention, and attempting to rebuild their reputation to attract new affiliates. In December 2024, LockBit announced the upcoming release of LockBit 4.0 variant, suggesting a possible resurgence in 2025. However, the group is unlikely to regain its position as the most prolific ransomware gang due the loss of its reputation and trust among affiliates following Operation Cronos. These efforts could involve targeting high-value entities while also conducting mass opportunistic attacks on under-protected sectors—such as healthcare and academia—to secure quick financial gains.
Infostealers To Remain Central to eCrime as Cybercriminals Show Renewed Resiliency to Law Enforcement Pressure
Coordinated global law enforcement operations targeted major malware droppers and infostealers throughout 2024, significantly disrupting key components of the eCrime ecosystem. While these efforts dealt substantial blows to malware and infostealer infrastructure like RedLine and MetaStealer, QuoIntelligence expects cybercriminals to adapt, improving their infrastructures. Infostealers are anticipated to remain a dominant threat in 2025, continuing to enable credential theft and serve as critical entry points for cybercrime activities.
In May 2024, Europol, in coalition with international law enforcement agencies and supported by various private partners, announced “Operation Endgame“. This operation, the largest of its kind, targeted major malware droppers, including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot. This effort significantly impacted the Malware-as-a-Service (MaaS) ecosystem commonly used by Initial Access Brokers (IABs) or within attack chains. However, in October 2024, researchers detected new attacks involving the Bumblebee loader, likely signaling its resurgence after LEA disruption. This finding underscores the resilience of the eCrime ecosystem. While some malware droppers may disappear for good, new ones will inevitably surface, and older variants could reemerge with enhanced capabilities—further obscuring their activities.
Infostealers were also the target of coordinated law enforcement efforts. In October 2024, law enforcement agencies (LEAs) from the US, the Netherlands, the UK, and Belgium announced the Magnus operation, which targeted the infrastructure behind the RedLine and MetaStealer infostealers. The operation resulted in the seizure of critical servers, domains, and other assets—such as source code, license servers, and communication channels—essential for RedLine and MetaStealer operations. This action significantly disrupted the distribution and command-and-control (C2) systems cybercriminals relied on for large-scale data breaches and credential theft. Alongside Operation Synergia II, which targeted ransomware, phishing, and infostealers, Operation Magnus inflicted substantial damage on the eCrime ecosystem, given RedLine and MetaStealer’s widespread use for initial access and follow-on attacks.
Data collected by LEAs may facilitate additional disruption operations in 2025. As such, we expect existing infostealers to learn from previous LEA actions and improve their infrastructures to become more resistant to LEA operationsAdditionally, cybercriminals will likely transition to more professional infostealers such as Lumma Stealer, StealC, and Vidar. Meanwhile credentials harvested by RedLine and MetaStealer will likely continue to circulate on underground marketplaces to maximize profits for unsold credentials. QuoIntelligence assesses that infostealers will remain a dominant threat in 2025, as the primary initial access vector for various criminal activities.
Further LEA Disruption Expected, eCrime Ecosystem To Adapt
In 2024, law enforcement significantly disrupted the eCrime ecosystem, weakening established groups but inadvertently creating opportunities for new actors to emerge and existing ones to adapt. In 2025, QuoIntelligence predicts that this fragmentation will drive a rise in mass-targeting cyberattacks, with small and medium enterprises bearing the brunt of these financially motivated threats.
Law enforcement operations are crucial to disrupt the eCrime ecosystem, shattering criminal operations and infrastructure, creating internal conflicts, and eroding their credibility and recruitment capabilities. However, law enforcement actions also create opportunities for new groups to emerge and for experienced operators to refine their processes and recruit.
In 2025, we anticipate new law enforcement disruptions, further fragmentation of the eCrime ecosystem along with the proliferation of ransomware gangs and providers. This landscape favors opportunistic targeting rather than “Big Game Hunting” as emerging groups often privilege mass targeting for faster gains while mobilizing less resources. In this configuration, small and medium enterprises are more at risk of being victims of financially motivated cyberattacks.
Vulnerable Network Devices and Drivers: Attackers’ Go-To Vectors
In 2024, attackers increasingly exploited network edge devices, targeted file transfer technologies, while also expanding their use of the Bring Your Own Vulnerable Driver (BYOVD) technique to evade security measures. In 2025, QuoIntelligence expects BYOVD attacks to become more widespread among skilled threat actors as well as being integrated into Malware as a service (MaaS) tools designed to bypass security measures.
In 2024, we observed a notable increase in the exploitation of vulnerabilities affecting edge devices like VPN appliances, network and IoT devices. Attackers favor these devices due to their powerful capabilities, occupying privileged positions within corporate networks, and offering limited transparency into their underlying code and operating systems. Continuing the trend from 2023, attackers also targeted several file transfer technologies in 2024.
State-sponsored groups and nexuses were among the first ones to resort to the Bring Your Own Vulnerable Driver (BYOVD) technique which exploits legitimate but vulnerable drivers to gain unrestricted access to targeted systems, successfully bypassing standard security measures. Throughout 2024, we observed more threat actors leveraging this technique, notably in ransomware attacks. The technical cost of BYOVD attacks has decreased due to the availability of open-source BYOVD exploitation tools and vulnerable driver libraries.
In 2025, we expect the BYOVD technique to become even more prevalent, especially as threat actors take advantage of unpatched, outdated, or third-party drivers. Additionally, BYOVD attacks are likely to be natively integrated in MaaS options developed to evade or disable security measures such as ZAM, AuKill, and Terminator.
Open-Source Project Security: Persistent Risks and Lessons from 2024 Incidents
In 2024, incidents targeting open-source projects revealed significant vulnerabilities that are likely to persist moving forward, as even the best security measures cannot entirely prevent infiltration by highly determined attackers.
In March 2024, the discovery of the infiltration of a rogue developer into an open-source project highlighted the risks of supply chain attacks targeting widely used software libraries. Over more than two years, an individual infiltrated the development team of the XZ compression library , ultimately inserting malicious code into the repository. Fortunately, security researchers detected the backdoor and reverse-engineered the code within three days of its initial release, averting significant harm. Similarly, in April 2024, security researchers thwarted a phishing attempt targeting an OpenJS Foundation JavaScript project, preventing a potential takeover.
These incidents have heightened awareness within the open-source community about the rising threat of social engineering attacks exploiting the openness of these projects and their chronic understaffing. This risk will persist in 2025, as determined and resourceful attackers could still leverage such vulnerabilities in open-source projects, calling for enhanced vigilance and robust security measures. As open source maintainers are now on high alert, any suspicious activity involving open-source projects will be highly scrutinized.
AI To Fuel the Next Wave of Social Engineering and Information Operations
Throughout 2024, AI was primarily exploited for social engineering campaigns and disinformation operations. QuoIntelligence expects these activities to remain the predominant forms of AI abuse in 2025. While we do not foresee large-scale offensive AI tooling, threat actors are highly likely to increase their attempts in this domain.
In 2024, we observed that threat actors increasingly leveraged AI technologies to assist with their activities, aiming to enhance both efficiency and quality. This trend was especially pronounced in social engineering campaigns (e.g., phishing, vishing, SMS), which allowed cybercriminals to significantly expand their operations, reaching more victims and in multiple languages. Researchers also uncovered other AI-enabled Tactics, Techniques, and Procedures (TTPs)—such as Large Language Model (LLM)-assisted vulnerability research, scripting, and operational command techniques. However, these remained relatively marginal uses of LLMs. Furthermore, security guardrails on most LLM platforms still prevent threat actors from efficiently creating offensive tools, thus not substantially lowering the barrier to entry for less-skilled criminals. We also observed a heightened use of deepfakes in 2024, deployed by threat actors not only in disinformation campaigns but also in financial frauds, extortion schemes, and efforts to circumvent Anti-Money Laundering (AML) protocols and Know Your Customer (KYC) checks. Threats actors have also developed malicious LLMs available in underground marketplaces. Several malicious LLM applications—such as malware development services—are already being advertised in underground forums. To date, however, no active attack has been definitively attributed to these tools. In a 2024 study, researchers demonstrated that these models can generate highly functional and evasive code, although they have yet to produce successful exploit payloads. Additionally, many malicious LLMs advertised on the underground are scams, exploiting low-skilled cybercriminals who seek to leverage AI for more advanced and sophisticated activities.
Looking ahead to 2025, we anticipate an even greater reliance on AI among threat actors, primarily for social engineering and disinformation campaigns. Demand for deepfakes in underground forums will likely grow, with sophistication increasing and prices becoming more affordable—lip-sync or deepfake videos already cost between USD 150 and 200 per minute. LLM technologies are expected to advance. Nevertheless, LLMs are subject to AI hallucinations, providing nonsensical or inaccurate responses, which are the result of perceived patterns or objects that are nonexistent. This phenomenon will likely hinder the creation of sophisticated offensive tooling in 2025. At the same time, as more developers rely on AI for coding, these hallucinations could introduce additional security risks by generating errors, bugs, and vulnerabilities, as well as exposing organizations to data poisoning.
Ukraine War and Elections in Europe in Russia’s Cyber Crosshairs for 2025
Russia’s cyber and influence campaigns will persist in 2025, focusing on supporting its war efforts in Ukraine. QuoIntelligence expects the 2025 German and Polish elections to be the targets of disinformation and espionage campaigns.
Since Russia’s invasion of Ukraine in February 2022, Moscow has focused heavily on the conflict, including mounting offensive cyber operations to bolster its military efforts. We anticipate these operations will persist into 2025—particularly during the first quarter—as Russia aims to secure additional territory before potential negotiations sought by newly elected US President Donald Trump. In parallel, Russia has been conducting influence campaigns to sway public opinion and election outcomes. Notably, the Doppelgänger, CopyCop, and Portal Kombat networks have consistently worked to manipulate narratives and influence European elections throughout 2024.
Against this backdrop, the German federal election in February 2025 and the Polish presidential election in May 2025 are highly likely to become targets of Russian disinformation. Information operations will likely exploit existing societal divisions to erode support for Ukraine and shape public opinion. Additionally, Russia could also resort to physical sabotage in conjunction with its disinformation efforts. Meanwhile, Russian state-sponsored APT groups—including APT28 (Fancy Bear) and APT29 (Cozy Bear)—are likely to engage in cyber espionage aimed at identifying potential policy shifts and actors sympathetic to Russian interests. Despite the possibility of a ceasefire or conflict resolution in Ukraine, pro-Russia hacktivist groups will likely persist in attacking Western targets, fueled by anti-Western narratives. The Kremlin remains unlikely to abandon its stance critiquing what it perceives as Western decadence and immorality. As a result, we expect European organizations to remain prime targets for pro-Russia hacktivist attacks.

Increased US-China Rivalry Expected in 2025: Broader Tariffs and Large-scale Espionage
In 2025, QuoIntelligence anticipates escalating US-China tensions leading to increased tariffs, intensified Chinese economic and political espionage, and heightened risks of conflict in the Taiwan Strait.
In 2024, US-China relations remained defined by intense economic competition and strategic rivalry in the Indo-Pacific region. The Biden administration implemented legislation and measures to restrict China’s access to critical, cutting-edge technologies, complicating Beijing’s long-term ambitions for economic supremacy and technological self-reliance—both vital to sustaining economic growth and the legitimacy of the Chinese Communist Party.
In 2025, the Trump administration’s “America First” agenda is likely to escalate tensions by imposing higher tariffs on Chinese imports to reduce the US trade deficit and restore domestic manufacturing jobs. Concurrently, as China advances its 14th Five Year Development Plan and its “Made in China 2025” strategy to bolster its manufacturing sector in advanced technologies, it is expected to intensify economic espionage efforts to counter the effects of increased tariffs and export controls. Chinese state-sponsored threat actors, such as APT10, APT41, and APT27, are likely to target companies and research institutions specializing in semiconductors, AI, and quantum computing. Chinese political espionage may also increase as Beijing seeks to anticipate and respond to the Trump administration’s foreign policy moves. China is likely to continue large-scale cyber espionage operations, such as the recently uncovered campaign targeting major US telecommunications operators. In response, the Trump administration may adopt a more offensive cyber strategy, leveraging private-sector expertise to strengthen US cyber defenses and deter adversarial activities. Additionally, a potential reduction in US support for Taiwan under Trump could embolden China to escalate its actions in the Taiwan Strait, advancing its goal of reunification with the island.
Here are QuoIntelligence’s main takeaways for 2025:
- Small and Medium Enterprises Increasingly At Risk In a Fragmented Cybercrime Landscape: The disruption of major ransomware operators, malware droppers, and infostealers in 2024 has fragmented the eCrime ecosystem. This has weakened established groups but opened opportunities for new actors and existing ones to evolve. In 2025, this fragmentation is expected to fuel a rise in mass-targeting cyberattacks, disproportionately impacting small and medium-sized enterprises.
- AI To Solidify Its Role as a Key Tool for Social Engineering Attacks and Disinformation: The use of AI in cyber operations has primarily focused on social engineering attacks and disinformation campaigns. These applications are expected to remain the dominant forms of AI exploitation in 2025. While large-scale offensive AI tools are unlikely, there will likely be increased attempts by threat actors to develop and deploy AI-driven capabilities.
- Geopolitics To Drive Cyber Espionage and Information Operations: The war in Ukraine and the intensifying US-China competition will continue to shape the global cyber threat landscape. Russia’s cyber and disinformation campaigns will likely focus on supporting its efforts in Ukraine, with particular emphasis on influencing the 2025 German and Polish elections. Meanwhile, escalating tensions between the US and China may lead to intensified Chinese economic and political espionage and increased risks of conflict in the Taiwan Strait.





