COVID-19 Pandemic: Response Checklist for CIOs and CISOs
We outlined some recommended measures for CIOs and CISOs to help address the potential cyber security impact of the increase
Explore our comprehensive archive organized by taxonomy. Discover a wealth of information categorized by subject, theme, or type to enhance your research and understanding.
We outlined some recommended measures for CIOs and CISOs to help address the potential cyber security impact of the increase
In order to address the potential impact of the spread of COVID-19 across Europe, here’s a few points the Chief
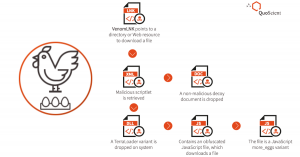
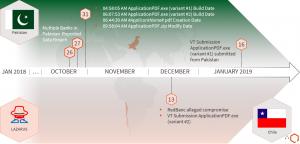
Note: This article was initially written by the QuoINT Team as part of QuoScient GmbH. Since the foundation of
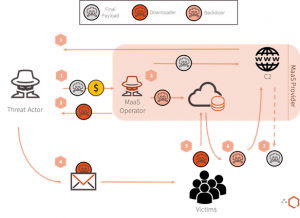
This blog post provides an overview on a specific Malware-as-a-Service (MaaS) used within the e-Crime threat actor landscape. It also
Try searching our blog

New Wave of Vishing Campaigns Against Identity Providers Targets Okta, Microsoft, Google, and Cryptocurrency Platforms | France To Ditch US Platforms Microsoft Teams, Zoom For Sovereign Platform Citing Security Concerns

In this outlook report, QuoIntelligence assesses the expected threat landscape for 2026, examining key developments across eCrime, malware evolution, hacktivism, and state‑sponsored activity.

North Korean Threat Actors Expand Contagious Interview Campaign With Malicious VS Code Targeting Developers | European Commission Proposes New Cybersecurity Package To Strengthen Resilience and Capabilities

VoidLink: A Modular Linux C2 Framework Targeting Cloud and Container Environments | Fundamental Disagreement Between US and Denmark Over Greenland, Europeans To Send Troops