The global COVID-19 pandemic has dramatically changed the way financial institutions conduct business. For one, many organizations have attempted to digitize former in-person interactions to abide by government standards for social distancing. In addition, employees moved from working in the office to working from home.
This increase in digitization allowed many financial institutions to maintain operations while keeping employees and customers safe and healthy. However, this shift to business operations also made organizations and customer reliant on the availability of secure online services.
This sudden shift created a larger attack surface, as it introduced and then relied on potentially untested or misconfigured remote technologies. This new remote environment also creates a headache for security personnel as they now have to ensure patching efforts across all endpoints.
In addition to the increased attack surface, the pandemic and its aftermath will likely stress test organizations in more ways than just ensuring the immediate continuity of operations. As the pandemic is ongoing, a recession is likely to occur in the coming months. This could result in CISOs having less resources available due to potential budget cuts. Further, the exceptionalism of 2020 has likely caused alert fatigue in many information technology and cybersecurity personnel, which could potentially lead to a decreased attention on deterring cyberattacks.
A potential recession could lead to budget cuts
With a pandemic-related recession potentially hitting global markets within the coming year, CISOs could have their budgets scrutinized in the months to come. According to McKinsey, a staggering 70 percent of CISOs believe that their budget for the fiscal year of 2021 will shrink even if they ask for an increase. The combination of potentially less well-funded CISOs and the increased attack surface from accelerated digitization and remote working, will likely cause CISOs to divert resources from other, longer-term cybersecurity measures.
Caution fatigue may increase vulnerability to phishing scams
While the threat of spear phishing is well known, it remains the most frequently used attack vector, as threat actors continue to successfully leverage attacks with their help – COVID-19-related themes are no exception, as these types of malicious emails dominated Q1 and Q2. As can be seen below, ‘Email’ was the attack vector in over 60 percent of attacks that QuoIntelligence recorded in the previous year targeting financial entities in Germany.
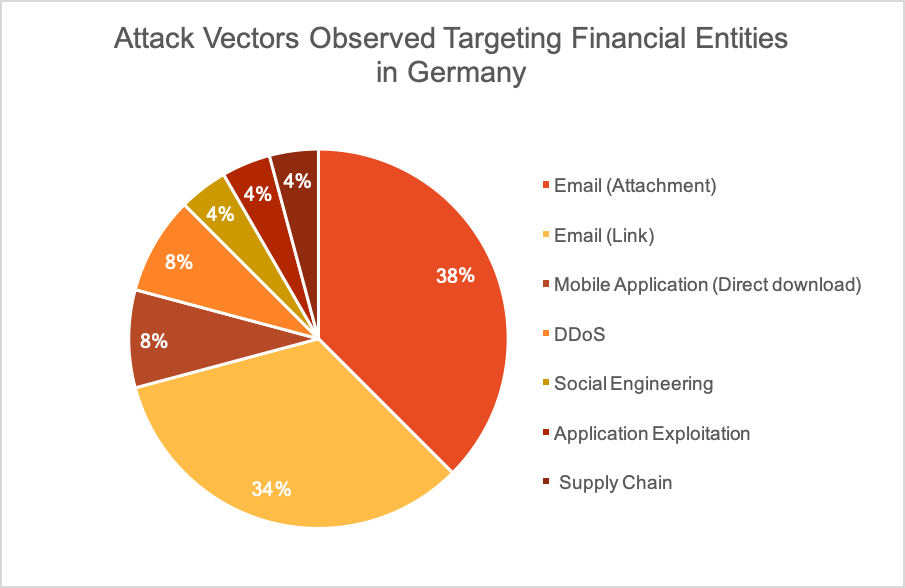
Organizations have prioritized education on proper cyber security awareness over previous years. However, the exceptionalism of this year and the constant state of alarm has likely caused widespread alert fatigue, meaning that we become desensitized to stress which leads to paying less attention to risky situations. This desensitization and less attention to spotting risks can have significant impacts on cybersecurity.
The risk of alert fatigue also extends beyond employees to the supply chain. Over the past year, cyber actors have increasingly targeted the trust relationship between organizations and their third-party suppliers. For example, cyber actors contact an organization by pretending to be one of their suppliers with allegedly unpaid bills or similar schemes to extort payments. As communication between organizations and suppliers is now heavily reliant on email communication, both sides need to be cyber aware.
These targeted cyberthreats combined with caution fatigue may make financial institutions even more vulnerable to potential cyberattack-related losses.
A larger threat landscape that’s here to stay
The first wave of COVID-19 may be over, but the second wave is currently in progress. And the increase in digitization is not going anywhere anytime soon. Employees will still be working remotely, and many businesses are considering making remote working permanent.
Many problems that stemmed from the first wave have yet to be addressed. CISOs are currently dealing with budgets for 2020 that were established prior to the pandemic. The increase in threat surfaces from remote working will mean that CISOs will likely have to put other priorities aside to accommodate business continuity from home and to establish and continuously monitor remote working environments. Remote workers are also being targeted by threat actors with a variety of scams, further making their security a top priority.
Digitization is here to stay and it is imperative that businesses adapt to the new reality by implementing resilient cybersecurity protocols.
- In case of a recession and related budget cuts, CISOs should leverage existing technology and attempt to automate standard procedures, such as scanning for vulnerabilities, maintaining and updating anti-virus signatures, and employ continuous monitoring.
- To combat alert fatigue, security protocols have to be enforced for employees, such as mandatory 2FA. This, along with employing least privilege access and blocking email attachments if their extension is not used within the company, helps to ensure an added line of defense to protect against human error.
The above recommended courses of action are by all means not all inclusive, but instead are a great start in protecting your organization’s increased attack surface. For questions or comments to help better protect your organization, please contact us to learn more.
Do you want to stay informed of cyber and geopolitical threats targeting your organization? Are you interested in receiving exclusive and unpublished intelligence?





