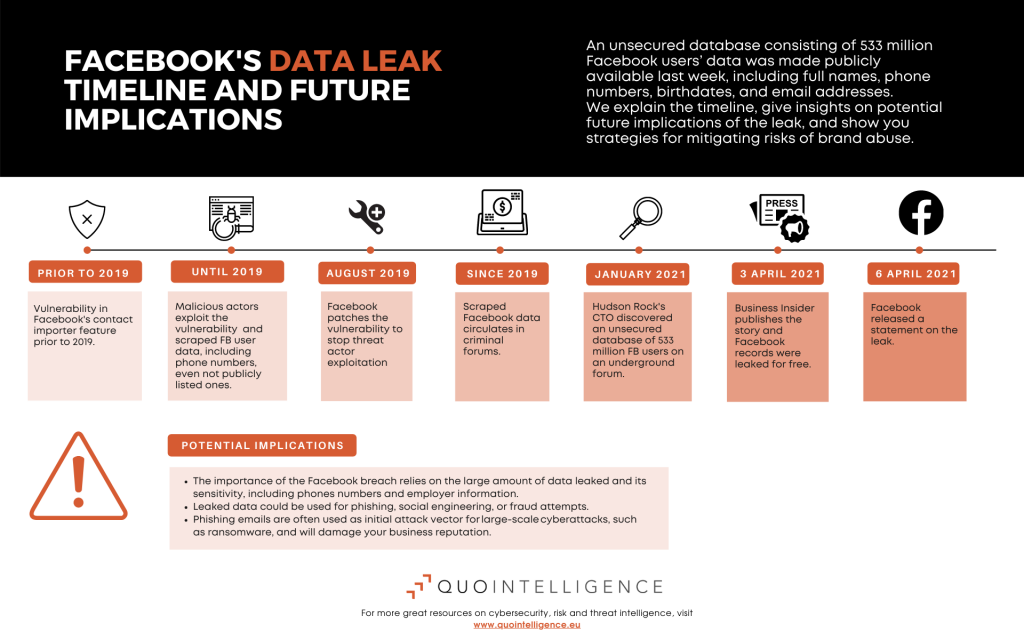
An unsecured database consisting of 533 million Facebook users’ data was made publicly available last week and raises the necessity of increased brand protection to prevent brand abuse. In January, the database was initially discovered when a threat actor was selling access to the underground forum’s data.
The compromised data includes personally identifiable information (PII) such as full names, phone numbers, birthdates, and email addresses. Facebook has not notified impacted users directly.
Are Large-Scale Leaks The New Normal?
The Facebook data leak highlights the normalization of large-scale leaks and a changing threat landscape for individuals and organizations, especially in terms of personal data and brand protection.
However, according to Facebook, the data was not obtained through cyber actors breaching Facebook’s systems but rather scraped by malicious actors who abused a contact importing feature.
The feature allowed users to discover other users via their phone number, even if they had not listed their phone number publicly on their user profile. Facebook updated the feature and indicated the scraping activity occurred before 2019 when the company fixed the security issue.
Click on the infographic to zoom in.
Brand Abuse with publicly available PII data
The leaked Facebook database is just one example of publicly available databases that consist of vast amounts of personal information.
This week, user data was reportedly also leaked from the social media app Clubhouse, LinkedIn, and ParkMobile.
Like the Facebook, LinkedIn, and Clubhouses databases, the personal information included in many databases is not obtained by breaching systems but through a collection of publicly available information.
While the data included in these leaks might not be highly confidential, threat actors can use it to conduct social engineering and spear-phishing attack campaigns.
Source: Mercury
Emails and social engineering primarily used for cyberattacks
The more information available about an individual, the more trustworthy and realistic a phishing email will look and, thus, more effective. While phishing emails and social engineering techniques are nothing new, they remain an effective and evolving tool for attackers.
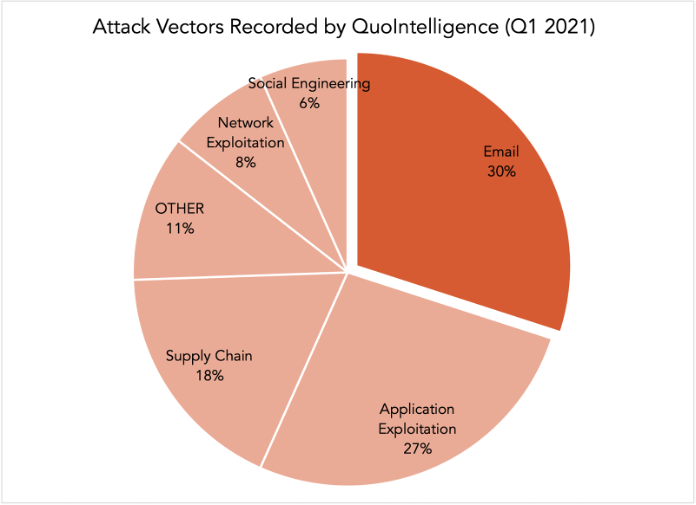
Consequently, emails and social engineering techniques combined constituted the initial attack vector in almost 40 percent of cyberattacks QuoIntelligence recorded in the first quarter of 2021.
Combined with other data leaks or simple OSINT research, malicious actors can use this information to craft highly realistic phishing emails. Phishing emails can be the initial attack vector for large-scale cyberattacks, such as ransomware, which cost victims EUR 620,000 on average in 2020.
Ransomware attacks not only incur direct costs, such as paying the ransom demand, regulatory fines, and business downtime. In addition, phishing emails abusing an organization’s brand name can damage the long-term reputation of the brand and result in indirect costs, such as the loss of customers.
Therefore, the Facebook data leak is of particular importance for companies because the data set included employer information.
Why the Facebook data breach aftermath could lead to more brand abuse
While companies usually announce data breaches and notify their users, rarely do they provide the exact data that is compromised.
Therefore, breaches may go unnoticed if affected users do not specifically search for their data in databases such as Have I Been Pwned.
In order to proactively mitigate the threat of leaked data being used for phishing, social engineering, or fraud attempts, organizations need to be aware of any data leaks that might impact them.
QuoIntelligence monitors underground forums and other leak sites to detect any leaked data that might impact our customers early on. We support mitigating strategies, such as early warnings on impending phishing campaigns or takedown services, in order to avoid costly damages down the line.
Make sure your brand and assets are protected against brand abuse!