We provide analyses on current events in our Weekly Intelligence Snapshot. Subscribe now to receive intelligence and news on the geopolitical and cyber threat landscape.
Revised Jan 26, 2022 — updated to include recent data and graphs.
In early 2021, we released our annual outlook, in which we forecast a rise in supply chain attacks and APT activity, among additional threats. Cybersecurity continued to be pressing concern for organizations in 2021, as ransomware and large-scale supply chain attacks surged. While law enforcement activity increased in response, it did not significantly impact the scale or lucrativeness of cybercrime. QuoIntelligence expects a continuation of these trends in 2022.
Additionally, we see threat actors evolving and adapting their attack vectors, toolkits, and tactics, techniques, and procedures (TTPs) to remain active as cybercrime remains profitable. In addition to cybercrime, we expect to continue seeing geopolitical tensions reflected in cyber space through espionage and sabotage activity. Geopolitical tensions, especially in the Indo-Pacific, between Russia and NATO states, and Middle East will spill over into the cyber domain.
Ransomware Attacks Will Continue to Pose a Major Threat to Organizations Despite Law Enforcement Disruption Campaigns
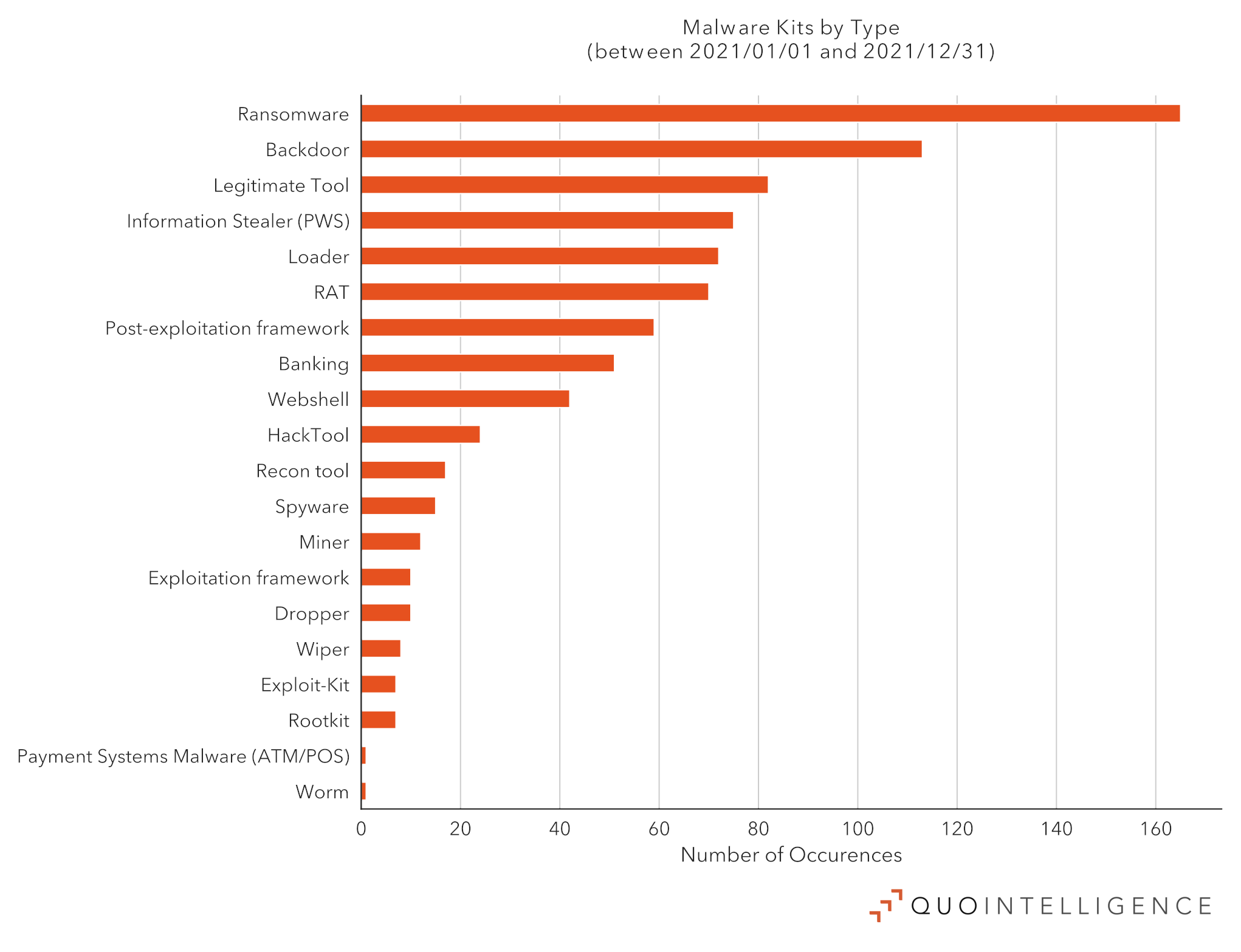
In 2021, ransomware attacks surged as they remained lucrative for eCrime actors and continued to constitute a top threat for all sectors. The most frequent type of malware kit recorded by QuoIntelligence in 2021 was ransomware. In addition, ransom demands increased, with the highest ransom demand of EUR 42.3 million (USD 50 million) in Bitcoin.
RaaS and IAB: the evolution of Ransomware business models
The ransomware business model evolved throughout 2021. While ransomware groups continued resorting to double extortion, Ransomware-as-a-Service (RaaS) also surged. RaaS is a business model in which ransomware developers enable affiliates to use their ransomware variants and earn a percentage of each successful ransom payment. This model allows actors without technical knowledge the ability to launch ransomware attacks by signing up for a service. For instance, Ryuk and REvil evolved their business models to include affiliate and partners through RaaS.
In addition, we also observed an increase in the use of Initial Access Brokers (IAB) and expect this to grow in 2022. IABs gain initial access to a victim’s network and sell this access to ransomware operators. In 2021, we witnessed partnerships between ransomware operators and initial access brokers rising, as initial access to victim networks become increasingly valuable. For example, Krebs on Security reported on Babam in December, an IAB that specializes in acquiring remote access credentials and who has published more than 270 posts on the Russian cybercrime forum Exploit since 2015.
Resorting to unusual extortion methods
Ransomware in 2022 will continue to evolve, with ransomware operators using new and more complex techniques in more targeted attacks. For example, QuoIntelligence observed how some groups, such as Ryuk/Conti and LockBit, shifted the focus from ‘big game hunting’ in 2020 to the low-end market in 2021.
Ransomware groups also began targeting small companies focusing on compromising a high number of targets. Smaller payments were made ranging from EUR 8,800 (USD 10,000) to EUR 45,000 (USD 50,000) since smaller companies often lack strong cybersecurity measures to be able to detect and mitigate a ransomware attack. In addition, by targeting smaller companies, cyber criminals hope to evade law enforcement attention, who are increasingly focused on larger-scale attacks on critical industries.
Ransomware operators are likely to intensify the ways they pressure victims into paying ransoms beyond the double extortion model. These include contacting customers of the impacted organization, threatening to notify journalists or cold-calling victims. These tactics are used by ransomware gangs, such as Sekhmet, RansomEXX, Conti, and Ryuk.
Remediation costs of cyberattacks increasing as governments punish paying ransoms, and insurers limit coverage
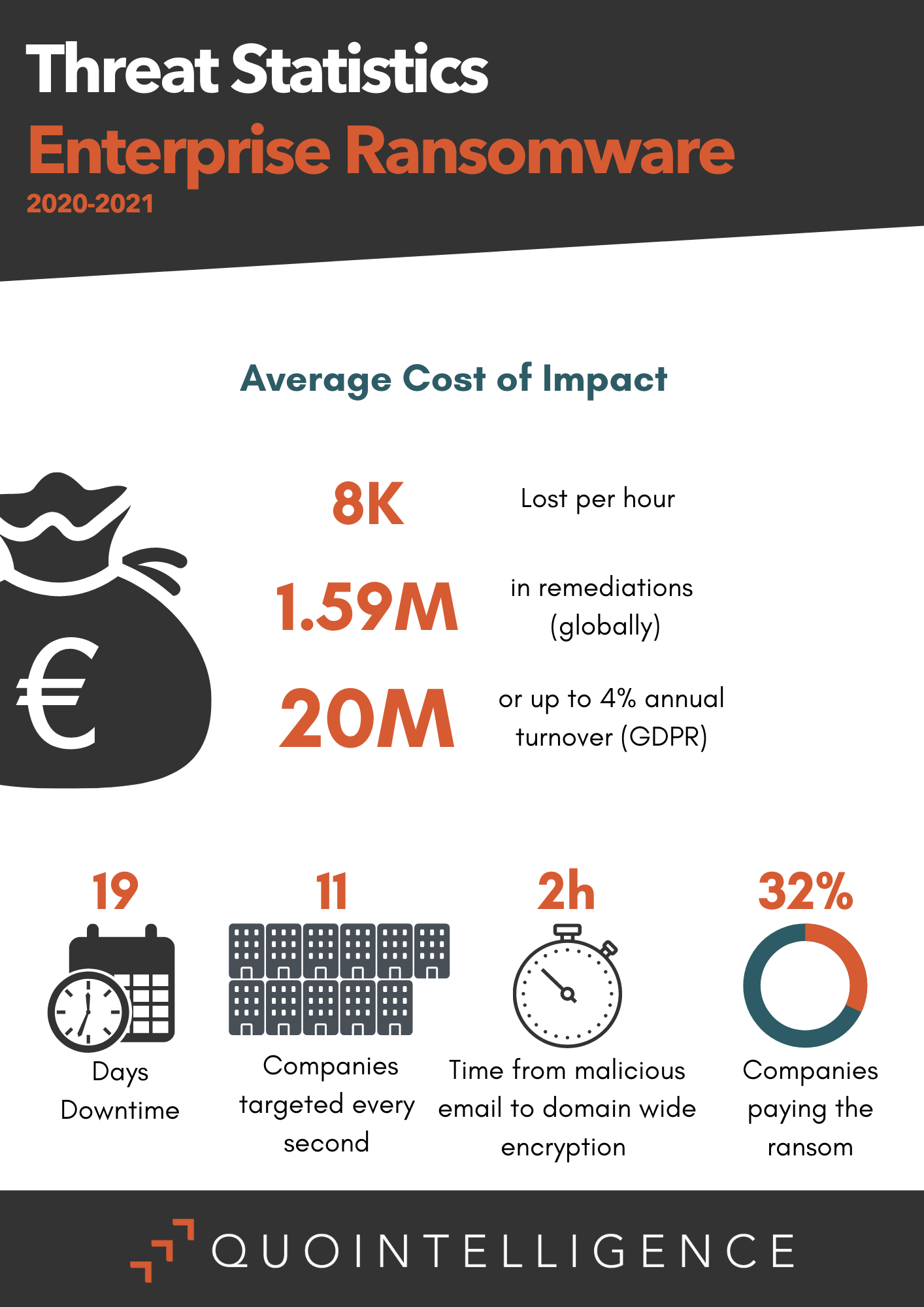
In 2021, law enforcement agencies increased disruption efforts, which we expect to continue in 2022. While increased law enforcement activity has not yet significantly interrupted the spread and profitability of ransomware attacks, the heightened attention from authorities led to some changes in the ransomware threat landscape. Several dark web forums used by ransomware groups, like XSS and RaidForums, announced they would ban any talk, promotion, or affiliate programs regarding RaaS. However, new, unregulated forums quickly started appearing.
Little effect
Overall, increased law enforcement activity did not considerably impact the threat landscape as new groups and business methods appeared to fill the void of groups taken down. For example, the disruption of the notorious TrickBot and Emotet has not had any significant effect on slowing the spread of ransomware. In fact, Check Point Research has recently found new samples of Emotet fast-spreading through surges in Trickbot activity used in ransomware attacks.
At the same time, increased government involvement could potentially further increase the cost for victims. As governments are attempting to de-incentivize ransom payments, they have notified companies that paying ransom demands could violate sanctions. In the US, regulators are considering implementing a mandatory reporting framework that will require companies to report on every incident. Similarly, insurers announced they will no longer reimburse victims for paid ransom.
In addition, cybercrime, specifically ransomware, is becoming a contentious geopolitical issue. The US is trying to limit safe havens for cyber criminals, such as through talks with Russia to increasingly target cyber criminals operating out of their region. However, criminals are likely to just move elsewhere.
Are you interested in testing how well your company is prepared for ransomware attacks? Talk to us about tabletop exercises
Digital Assets Increasingly Targeted
Cybercriminals and state-supported cyber threat actors linked to heavily-sanctioned countries, for example Lazarus which is linked to North Korea’s government, continue to show a focus on digital assets, especially in light of their continued attraction to new investors and users. This trend is likely to continue in 2022, resulting in crypto exchanges, wallets, and decentralized finance (DeFi) platforms remaining a popular target for cyberattacks.

According to a recent report by Elliptic, losses suffered by investors and users of DeFi platforms accumulated to more than EUR 10 billion (USD 12 billion) in 2021, a 600 percent increase compared to 2020. In December, the crypto company BitMart disclosed that assets worth EUR 132.95 million (USD 150 million) were stolen after wallets were compromised. In the same month, around EUR 106 million (USD 120 million) were stolen during a cyberattack on the DeFi platform Badger.
Cryptocurrency scams in 2022
These will increase as criminals profit from a lack of cybersecurity awareness, coupled with exploitable security vulnerabilities in DeFi platforms. For instance, Check Point researchers discovered that critical security vulnerabilities on a crypto platform could be exploited to hijack user accounts.
Governments are introducing new regulations to ensure companies are putting better cybersecurity measures in place to limit cyberattacks as DeFi remains less regulated than the traditional financial market. In addition, regulators are targeting the anonymity of DeFi platforms, as they as they are increasingly used by criminal groups, to launder funds for example. However, legislation is limited to domestic markets, which makes the legislation ineffective to regulate the inherently international DeFi market.
In addition, new legislation takes time to come into effect, potentially making it outdated to deal with current problems by the time it becomes operational. For instance, the US government passed an infrastructure bill aimed at regulating crypto exchanges that will only start to be enforced in 2023.
Key Industries Continue to be Cyberespionage Targets For Advanced Persistent Threats Groups
Last year, we predicted a rise in Advanced Persistent Threat (APT) campaigns targeting key industries for industrial and government espionage. Our forecast proved true as instability and geopolitical tensions endured worldwide. We expect espionage campaigns to continue in 2022.
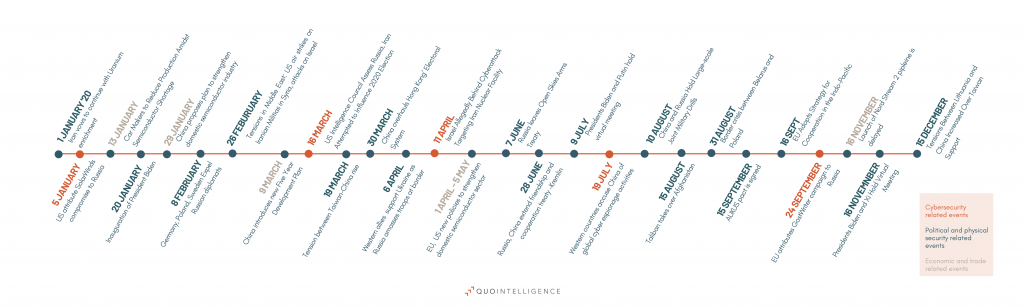 Click on image to enlarge
Click on image to enlarge
Geopolitical tensions will lead to increased espionage and sabotage cyberattacks
In terms of government espionage, the ongoing tensions in the Indo-Pacific, including between Taiwan and China, as well as in the South China Sea, will be accompanied by espionage campaigns extending to other countries, including the US, Europe, and Australia. While large-scale cyber warfare is unlikely, low scale cyberattacks that remain under the threshold of armed conflict will persist and likely increase alongside political tensions.
Similarly, tensions between Russia and NATO countries over Ukraine, as well as between the EU and border countries, will continue into 2022 and be accompanied by cyber espionage, small-scale cyber sabotage and disinformation campaigns.
Evolving tensions in the Middle East, including Israel’s expansion of settlements, Iran’s continued nuclear enrichment, the establishment of a Taliban-led government in Afghanistan, and other conflicts in Yemen, Syria, or Libya, could be accompanied by increasingly damaging cyberattacks, which could impact private industry as collateral damage.
Industrial espionage to remain a top threat in key industries
In terms of industrial espionage, the activity of state-sponsored APT groups will be directed by government priorities. Entities involved in the following areas will likely be targeted with espionage campaigns: environmental policy and technology, securing supply chains, military competition, and space exploration.
China’s Five-Year Plan: A Pursuit for GDP Growth & Technological Self-Sufficiency
Environmental policy and technology:
The growing awareness of climate change has made environmental policies a priority for policy makers. As governments are devising ways to combat environmental change, they are also investing in or mandating technological shifts, such as the focus on electric vehicles (EVs).
APT groups will, on one hand, target policy makers to gain an early understanding on how climate-related policies could affect their sponsoring nations, such as through new taxes or due diligence regulation. On the other hand, companies involved in new technology R&D and manufacturing, including batteries, chips, and materials needed to produce them, will be increasingly targeted as governments race to establish themselves as environmental tech hubs.
Securing semiconductor supply chains
The large-scale and continued disruptions of supply chains for semiconductors has already resulted in governments investing in attempts to make supply chains more resilient by ‘bringing suppliers home’. The EU, for example, has already announced investments into semiconductor manufacturers to ease reliance on Asia.
As the increase for chips will continue growing in the coming year with supply likely to continue lagging, industrial espionage will target all companies involved in the supply chain in order to boost domestic production. This includes R&D entities, including universities, chemical producers, and other key producers for technology such as machinery or clean rooms.
Military competition
As military conflicts are ongoing, and even intensifying in the Middle East, the Indo-Pacific, and possibly between Russia and NATO countries, espionage activities will do too. While governments and the military have always been valuable targets for APT groups, private military contractors and weapon producers will also continue to be targeted.
Space exploration
Governments are increasingly relying on private providers for space exploration, such as NASA on Space X. As states are picking up competition in space again, any entities, public or private, involved in space exploration are potential targets for state-sponsored APT groups. In July, Germany set up a new space command a military body with the responsibility for space operations, in reaction to “the increasing importance of space for the functionality of our state, the prosperity of our population and the increasing dependence of the armed forces on space-based data, services and products.“
Governments to increasingly ‘name and shame’ state-supported cyber activity
Cyberattacks are a priority issue for governments and in the coming year, we expect to see increased efforts in publicly attribute cyber campaigns and espionage activity to ‘name and shame’ adversaries. For example, in April, the US imposed punitive measures against Russia, including financial sanctions and diplomatic expulsions, in response to the SolarWinds espionage campaign and alleged Russian interference in the 2020 US Presidential elections.
In order to evade increased scrutiny, nation-state groups are likely to continuously evolve the sophistication of their techniques, including increasingly using false flag operations, increasingly diversify their TTPs and tooling, and increasingly expand their resources to non-nation state personnel – such as hiring or partnering with cybercriminals of various skillsets and motivations.
Did you enjoy this story? There’s more where it came from! Subscribe to our newsletter to receive the lastest stories straight into your inbox.
Did you enjoy this story?
Subscribe to our Weekly Intelligence newsletter and stay informed on recent cyber threats, breaches, vulnerabilities, research, and more.
As a subscriber, you can also download our full report on all incidents, warnings, and news of the week.





