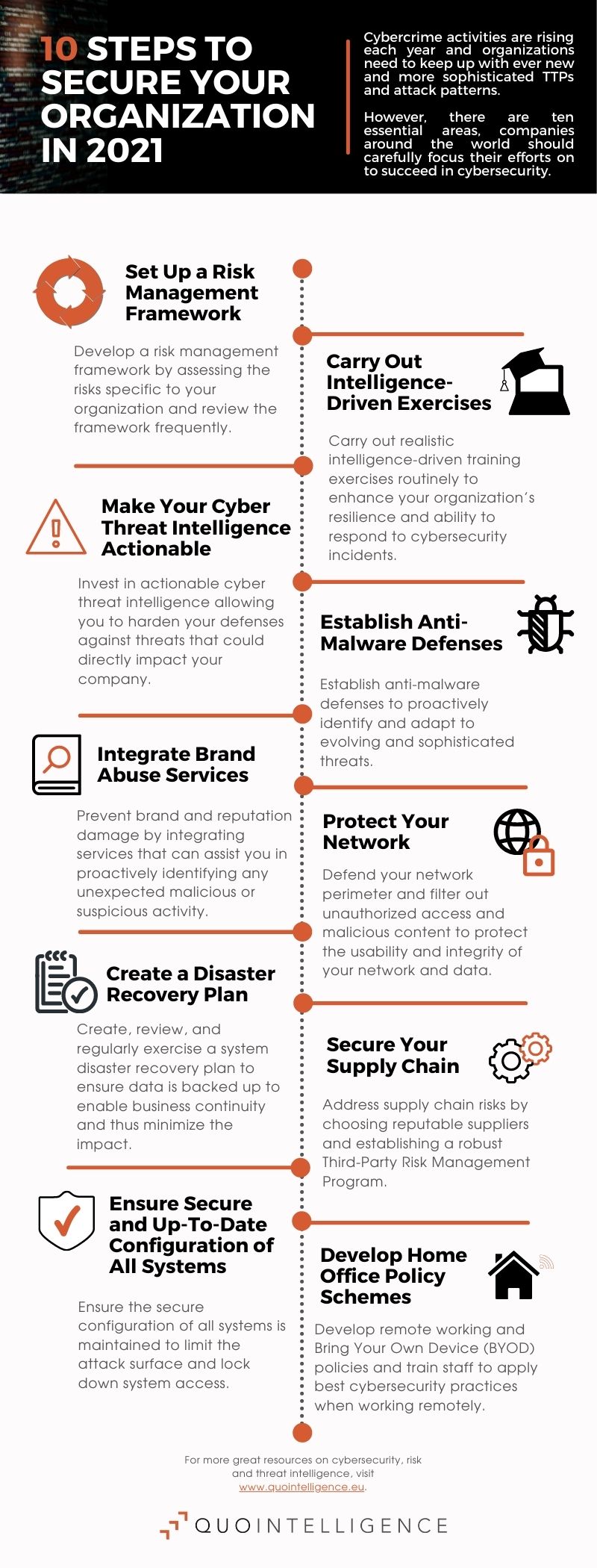
Cybersecurity is a growing area of concern across many organizations and cybercrime activities are rising each year and organizations need to keep up with ever new and more sophisticated TTPs and attack patterns.
QuoIntelligence helps you to protect your business from cyberattacks. Therefore, our threat intelligence services, risk intelligence, and intel-driven exercises proactively secure your assets and help you to mitigate cyber threats.
Here are ten essential areas every organization should focus their cybersecurity efforts on.
Join our community of cybersecurity and threat intelligence professionals. Subscribe now for weekly industry-relevant news, research and resources.
For more details and information, scroll below the infographic!
1. Set up a risk management framework and incident management policies
Cybersecurity risks are a reality for businesses regardless of their industry sector or size. A well-established and effective risk management framework is key to identifying existing and potential threats to an organization and mitigating the risks associated to them. Threat Intelligence services can help you to identify potential threats over time, better supporting security decisions, and framing your risk management policies. When setting up a risk management framework, assess the risks specific to your organization and review the framework frequently.
2. Carry out intelligence-driven exercises
Organizations can be unprepared if they do not exercise their incident response plans frequently. Carrying out realistic intelligence-driven training exercises routinely will enhance your organization’s resilience and ability to respond to cybersecurity incidents. Ultimately, these exercises will reduce response times, identify gaps, and potentially limit the impact on your business.
3. Make your Cyber Threat Intelligence actionable
Threat intelligence enables companies to make faster and more informed decisions as it gives insights into a threat actor’s Tactics, Techniques, and Procedures (TTPs); while also contextualizing a threat, taking into consideration economic, social, and geopolitical circumstances. Invest in actionable cyber threat intelligence allowing you to prioritize your time and resources on hardening your defenses against threats that could directly impact your company.
4. Establish anti-malware defenses
Malware strains are growing exponentially and becoming more sophisticated and adaptative. As cyber actors find new ways to penetrate their targets, anti-malware solutions are not enough to protect your organization. Businesses should be prepared with advanced hunting capabilities for quick incident response. Actionable intelligence can support this task by proactively fighting against targeted and non-targeted malware campaigns. Establish anti-malware defenses that allow you to proactively identify and adapt to evolving cyber threats.
5. Integrate brand abuse services
Reputational loss threatens the public’s view of a company or organization and therefore directly impacts your finances. Brand abuse can be used against you to damage your business’ reputation. In the worst case, it results in losing customers. Prevent brand and reputation damage by integrating services that can assist you in proactively identifying any malicious or suspicious activity.
6. Secure your supply chain
One of the most critical sources of cyber risk worldwide across all industries is the supply chain, as seen with the recent SolarWind breach. Outsourcing can be risky given the exposure companies need to allow to third-party suppliers. To address supply chain risks, choose reputable suppliers and establish a robust Third-Party Risk Management Program allowing access to systems and data at a minimum.
7. Create a Disaster Recovery Plan
Ransomware attacks are steadily rising and evolving, threating business continuity. A successful attack can result in a complete stop in operations, resulting in unexpected downtime, loss in revenue, and customer trust. As a result, organizations lose money and credibility. Having an effective disaster recovery strategy in place makes the difference allowing you to quickly recover from a ransomware incident and reduce financial impact. Create, review, and exercise a disaster recovery plan to ensure data is backed up resulting in a continuity of business to minimize the impact.
8. Protect your network to prevent data breaches
Ideally, organizations should have a good understanding of what constitutes normal activity on their network. Effective security monitoring and event logging should be able to identify any unusual activity. Defend your network perimeter and filter out unauthorized access and malicious content to protect the usability and integrity of your network and data.
9. Ensure a secure and up-to-date configuration of all systems
Unpatched and outdated systems represent one of the weakest and most targeted entry points to an IT system as they are substantially more vulnerable to outside cyber threats. Apply security patches to secure the configuration of all systems to limit the attack surface and lockdown system access.
10. Develop home office policy schemes
Cyber actors are leveraging the current shift to remote working to target organizations by exploiting vulnerabilities in telework technologies and abusing already strained bandwidths with Distributed Denial of Service (DDoS) attacks. Well defined remote working schemes can help organizations to mitigate this growing risk. Develop remote working and Bring Your Own Device (BYOD) policies and train staff to apply best cybersecurity practices when working remotely.