
Cyber Security Trends in 2021: Espionage Activities Increasingly Threatening
In the following blog post, we will provide an overview of the major cyber security trends observed over 2020 and
Explore our comprehensive archive organized by taxonomy. Discover a wealth of information categorized by subject, theme, or type to enhance your research and understanding.

In the following blog post, we will provide an overview of the major cyber security trends observed over 2020 and

In this second blog post in our series on Geopolitics in Cyber Threat Intelligence, we will explain what is meant

The cyber-threat landscape increased significantly this year due to the COVID-19 pandemic caused by accelerated digitization and the sudden shift

Our declassified threat intelligence analysis on a APT28 spear phishing campaign delivering Zebrocy malware to target at least a government

In this blog, we explain how TIBER-EU tests are conducted and describe the role of the Threat Intelligence Provider in

You can find here the latest threat intelligence updates on the new BlackWater Malware campaign using the Beirut tragedy to

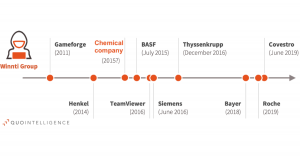
Learn more about the Golden Chickens Malware-as-a-Service tool updates observed in recent malware campaigns against the financial, retail, and chemical

This post is the first part of a two-part blog series in which we will explain the TIBER-EU framework and
This post is the first in a series of five short blogposts, in which we will explain why geopolitics is
Newly uncovered DNS tunnelling technique, and new campaign against South Korean gaming company Executive Summary In January 2020, QuoIntelligence (QuoINT)
Try searching our blog

New Wave of Vishing Campaigns Against Identity Providers Targets Okta, Microsoft, Google, and Cryptocurrency Platforms | France To Ditch US Platforms Microsoft Teams, Zoom For Sovereign Platform Citing Security Concerns

In this outlook report, QuoIntelligence assesses the expected threat landscape for 2026, examining key developments across eCrime, malware evolution, hacktivism, and state‑sponsored activity.

North Korean Threat Actors Expand Contagious Interview Campaign With Malicious VS Code Targeting Developers | European Commission Proposes New Cybersecurity Package To Strengthen Resilience and Capabilities

VoidLink: A Modular Linux C2 Framework Targeting Cloud and Container Environments | Fundamental Disagreement Between US and Denmark Over Greenland, Europeans To Send Troops