How DNS-over-HTTPS (DoH) has Changed the Threat Landscape For Companies

DoH provides the benefit of communicating DNS information over an encrypted HTTPS connection but presents security issues for organizations.
Supply Chain Attacks, Cybersecurity & Regulations: What to Expect in 2021

Supply chain attacks are on the rise in 2021. The recent SolarWind breach and COVID-19 are only exacerbating supply chain threats. More and more nations are working towards stringent frameworks to strengthen supply chain security. Read our article to find out which attack vectors, threat actors and new regulations to watch in 2021!
Brexit, Cybersecurity & Data Protection: Everything you need to know about the EU-UK Trade Deal

The Brexit transition period has ended. On 24 December 2020 the EU and UK reached the Trade and Cooperation Agreement (TCA), which regulates EU-UK relations.
QuoIntelligence provides a summary with everything you need to know about the EU-UK Trade Deal regarding Cybersecurity, Data Protection and Information-Sharing .
Cyber Security Trends in 2021: Espionage Activities Increasingly Threatening

In the following blog post, we will provide an overview of the major cyber security trends observed over 2020 and provide an outlook into potential developments in the coming year. Namely, we will address the ongoing COVID-19 threat, ransomware and phishing trends and especially focus on the increasing threat QuoIntelligence sees in industrial, political and military espionage for 2021.
Part II of V: Why Geopolitics is Integral to Cyber Threat Intelligence

In this second blog post in our series on Geopolitics in Cyber Threat Intelligence, we will explain what is meant by geopolitics, how it is intertwined with cybersecurity, and how QuoIntelligence includes geopolitics in its cyber threat intelligence analyses.
APT28 Delivers Zebrocy Malware Campaign using NATO Theme as Lure

Our declassified threat intelligence analysis on a APT28 spear phishing campaign delivering Zebrocy malware to target at least a government body in the Middle East using a NATO course as a lure.
BlackWater Malware Leveraging Beirut Tragedy in New Targeted Campaign

You can find here the latest threat intelligence updates on the new BlackWater Malware campaign using the Beirut tragedy to lure targets.
GOLDEN CHICKENS: Evolution of the MaaS

Learn more about the Golden Chickens Malware-as-a-Service tool updates observed in recent malware campaigns against the financial, retail, and chemical sectors.
The Importance of Geopolitics for Cyber Threat Intelligence
This post is the first in a series of five short blogposts, in which we will explain why geopolitics is an integral part of our cyber threat intelligence analyses. Each blogpost will outline an aspect of the importance of this approach for us, our clients, and the Cyber Threat Intelligence community.
WINNTI GROUP: Insights From the Past
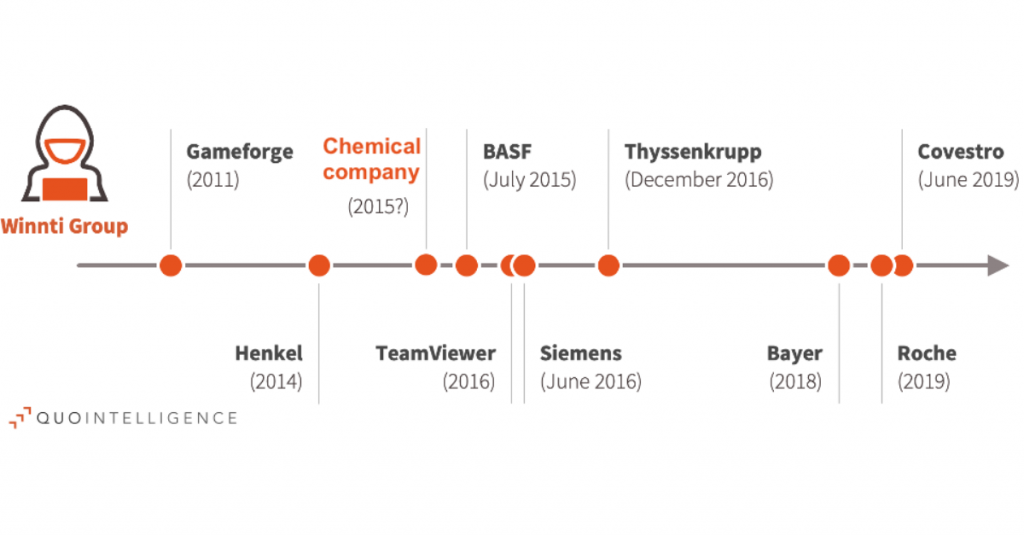
Newly uncovered DNS tunnelling technique, and new campaign against South Korean gaming company Executive Summary In January 2020, QuoIntelligence (QuoINT) detected a new Winnti sample uploaded to a public virus scanner from a German location. Following our preliminary analysis, we assessed with high confidence that the sample was used to target a previously unreported German […]