Threat actors to increase collaboration and develop new TTPs to continue to cash out, while geopolitical polarization complicates the cyber threat landscape
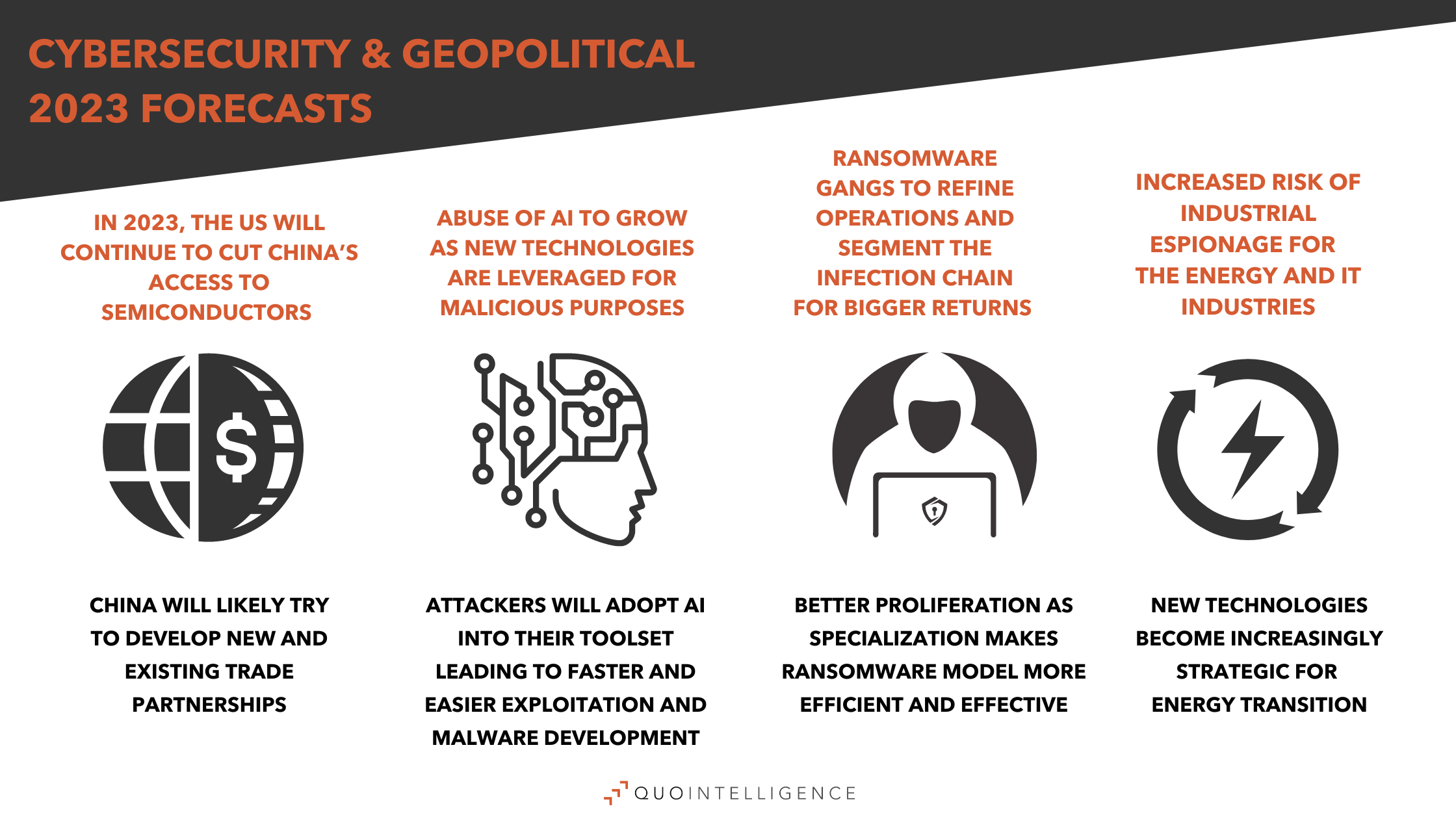
Early last year, we released our 2022’s outlook, in which we predicted a continued increase in Ransomware-as-a Service and in the use of Initial Access Brokers. We also forecasted that geopolitical tensions would lead to increased espionage and sabotage cyberattacks. These trends were particularly prevalent through 2022 and we expect them to continue in 2023.
In fact, in 2022, the war in Ukraine dominated the threat landscape, highlighting more than ever how geopolitical tensions are reflected in the cyber domain. It resulted in a notable rise in hacktivism, new threat actors and increased risk of cyber and physical sabotage against critical infrastructure. As we also anticipated, in 2022 eCrime actors continued to professionalize their processes and adapt their TTPs to gain efficiency and avoid disruption of their activities.
In 2023, QuoIntelligence forecasts increased collaboration between threat actors fostering their resilience, while geopolitical competition and polarization worldwide drive new cyberattacks and dominate threat landscape trends.
Ransomware gangs to continue refining the stages of infection and externalize services during attacks
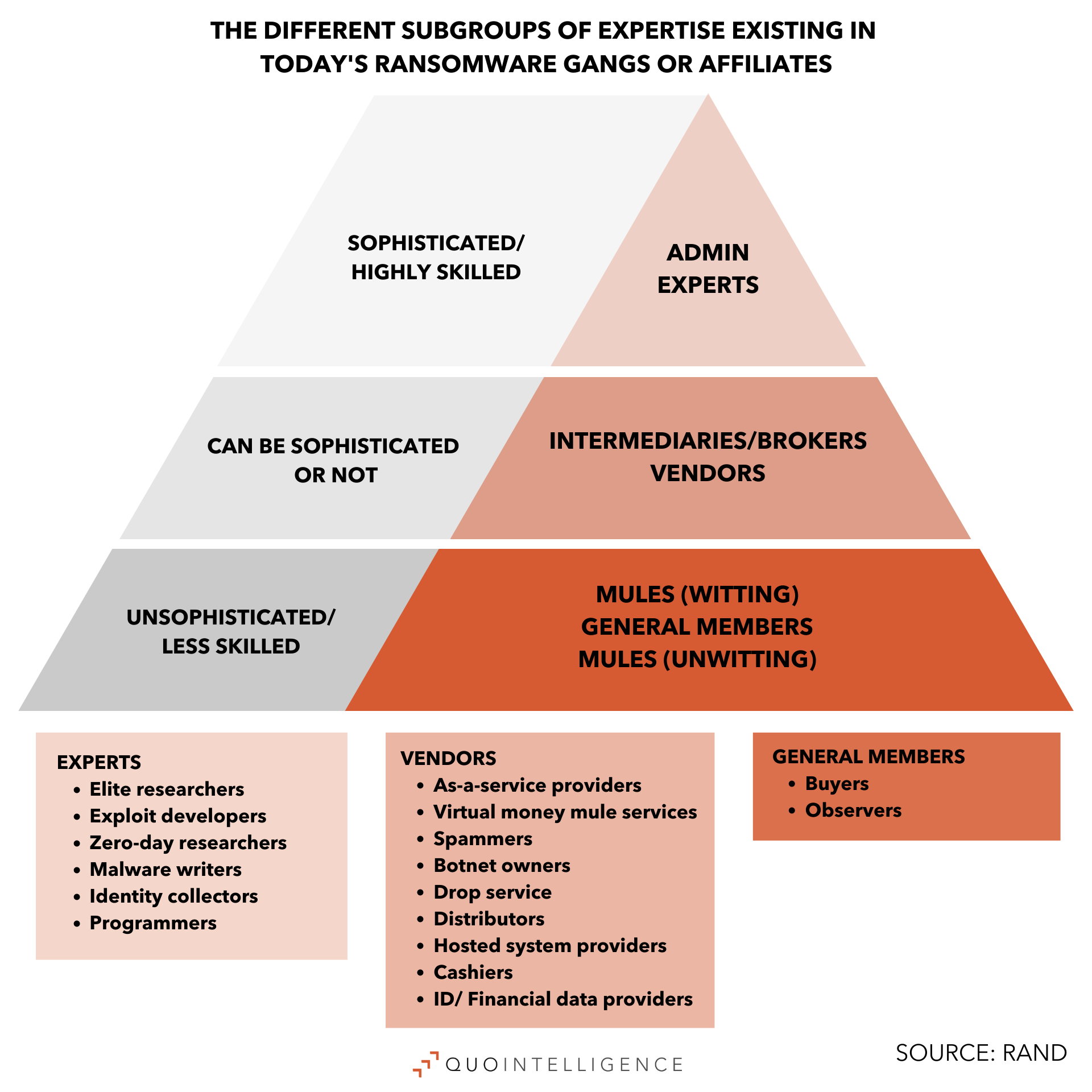
As we predicted for 2022, the infection stages of a ransomware attack are now more likely to be distributed across different operators — switching from one to another along the infection chain. So much so that Initial Access Brokers are now one of the main pillars of ransomware attacks. The specialization of actors on specific parts of the infection chain can make the ransomware model more efficient and effective, leading to better proliferation. This helps older ransomware groups to settle down by externalizing some of the elements of their business and allowing them to invest in more specific aspects of the business itself, such as ransomware development, or negotiation processes. Additionally, it also facilitates the spawning of new groups when others are disrupted, or operators switch their services from one ransomware client to another.
As this trend continues in 2023, we expect ransomware gangs to stay refining their model and remain one of the main threats across the cyber landscape. One of the best examples of disruption and reemergence as a smaller group is the case of Conti, while the best example of consolidation is Lockbit. Lockbit released its 2.0 version in 2021 and a year later it announced its 3.0 version with a few upgrades and innovations. Later, researchers published an interview with one of the founders of Lockbit who expressed their plan to grow. Following this pattern, it is likely that by the summer of 2023 Lockbit will announce its 4.0 version.
Newly specialized eCrime providers consolidate their business models by collaborating with ransomware gangs
In line with the aforementioned trend, we expect to observe providers specializing in a particular attack stage working together as part of the same infection chain. For 2023, we expect new Malware-as-a-Service (MaaS) operations to appear and the Phishing-as-a-Service model to gain stability and proliferate, as we already observed a peak of relevance in the landscape. Parallelly, we assess that it is very likely that more individuals, not only groups, will try to set up their own business with the rise of “traffers”, a more specific kind of Initial Access Broker which also often uses MaaS as part of its business.
Mobile: On-device fraud tech to circumvent fraud detection
The current evolution of mobile malware is steering toward fully-integrated On-device-fraud (ODF) technology on most banking trojans. This technology, already observed in many successful banking trojans, allows eCrime operators to initiate fraudulent transfers on the victim’s device, bypassing security controls. For instance, some trojans, like the Brazilian BrasDex trojan, integrate an Automated Transfer System (ATS) engine, a system that follows a script in order to initiate transfers without manual involvement. These types of trojans have seen a rise in popularity, with threat actors switching away from the previously popular overlay attacks due to ODF setups being more successful in circumventing fraud detection solutions.
In 2023, the spread of ODF technology in banking trojans will likely lead to significantly higher fraud success rates. As a result, financial institutions will need to implement measures to detect these fraudulent transfers.
On the other hand, we have observed threat actors running extremely targeted campaigns against singular banking institutions, in which SMS stealers were part of the attack chain. SMS stealers, whose only job is to exfiltrate incoming SMS messages, were used to capture one-time passwords (OTPs) in these instances. As part of a bigger attack chain, they require less intrusive permissions and can masquerade as a particular banking application, making them less prone to discovery as regular banking trojans.
We assess that, given a recent rise in attacks employing these techniques with major success, 2023 will likely see further campaigns targeting specific banks employing SMS stealers as part of the infection chain.
Make-or-break for Spyware as the industry is thrust into the limelight
With the blacklisting of NSO and its Pegasus spyware in 2022, the US set a precedent for the handling of spyware vendors. Companies selling access to spying tools will need to face stricter export license regulations and implement robust know-your-customer programs. This will expose more spyware vendors as well as organizations that use their products to public scrutiny and critique and force countries that have not yet done so to adopt legislation regulating the sale of spyware. Therefore, 2023 will be a make-or-break year for the industry as vendors will be forced to adapt to the changing legislation or will be similarly blacklisted.
Cobalt Strike alternatives to proliferate
Throughout 2022 we reported on alternatives to the widely used Cobalt Strike post-exploitation framework, such as Brute Ratel, Silver, and Manjusaka. For the last few years, Cobalt Strike has been one of the most leveraged offensive tools. However, as many security vendors have dedicated huge efforts to detect and prevent Cobalt Strike, other alternatives have emerged. We expect such alternatives to gain market share in the threat landscape throughout 2023, since they may be harder to detect or disrupt than Cobalt Strike.
Abuse of AI will grow as new technologies are leveraged for malicious purposes
State-of-the-art open-source Artificial Intelligence (AI) has made significant progress over 2022. Up to the point that now making AI models and technologies is not only available for experts, but also for users without deep AI knowledge. One of the most notorious examples is the artificial intelligence chatbot launched by OpenAI in November 2022, ChatGPT3. We have monitored and tested ChatGPT’s capabilities, confirming it to be useful for identifying vulnerabilities in code, writing malicious code, or even phishing emails. While it still needs the eye of a relatively experienced attacker to obtain useful results, ChatGPT makes the attacker’s job easier and quicker, likely reducing the time spent on successful exploitation of vulnerabilities and weaponization of the exploits. In line with the trait of using innovative ways to abuse technologies, we expect attackers to adapt to other new technologies that are being implemented or gradually adopted by companies such as Web 3.0, Metaverse, IoT devices, and Industry 4.0.
Threat actors to continue to use digital assets despite increased scrutiny on the sector
2022 was a particularly rough year for cryptocurrency entities, investors, and users. As we predicted in our annual outlook last year, cyber criminals continued to target digital assets. In particular, North Korean threat actors launched numerous campaigns targeting a large panel of organizations in the blockchain technology and cryptocurrency industry. Threat actors also connected cryptocurrency VIPs through Telegram to infect them with malware and impersonated cryptocurrency firms. The market value of all cryptocurrencies decreased, and regulators fined mixer platforms for cryptocurrency laundering. In November 2022, the bankruptcy of FTX, one of the world’s largest crypto exchanges, severely undermined trust in the sector. This led to a chain reaction of other bankruptcies and insurers denying — or limiting coverage to — clients with exposure to FTX.
In 2023, the US Securities and Exchange Commission (SEC) and Commodity Futures Trading Commission (CFTC) will seek to extend their current prerogatives to regulate digital assets. Legislators will probably support a comprehensive crypto bill to impose new restrictions and more supervision on crypto entities. The EU will also address this issue, as the European Parliament is set to adopt the regulation on markets in crypto assets (MiCA). This legislation will establish harmonized rules on cryptocurrencies to protect consumers and investors, foster financial stability, and prevent market manipulation and financial crimes.
Despite the increased scrutiny of the crypto sector, threat actors will continue to rely on digital assets to cash out. They will also continue to shift towards peer-to-peer cryptocurrency exchanges to convert or launder illicit funds as these platforms tend to be less strict in terms of identity and security requirements.
Increasing politization of the threat landscape will result in continued hacktivist attacks, new threat actors, and cyberattacks below war threshold
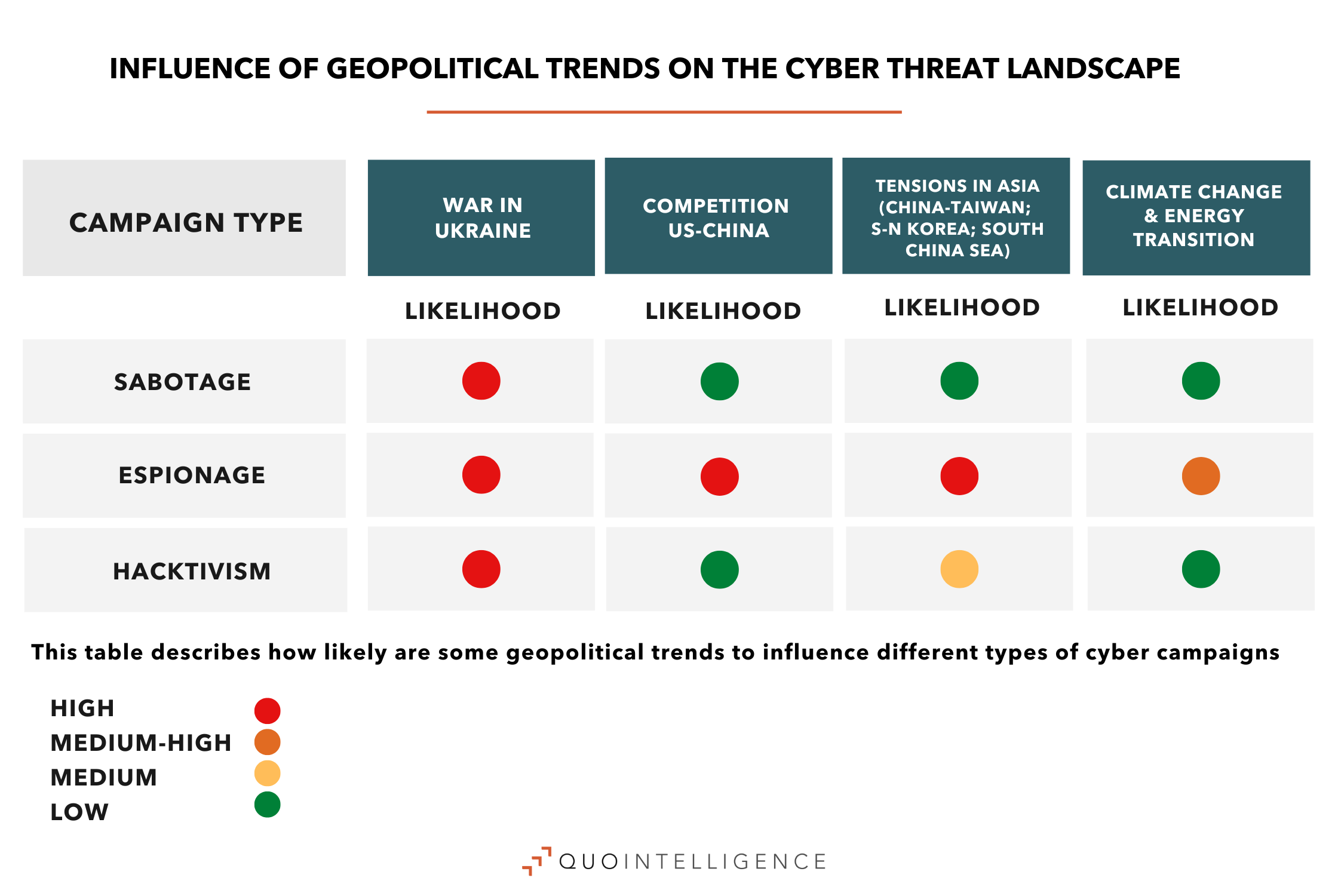
The war in Ukraine and rising geopolitical tensions worldwide resulted in increased politization of the threat landscape over 2022, with a rise in hacktivist activity that will likely continue in 2023. Not only did hacktivist attacks augment in number — like the numerous Killnet DDoS attacks against Western organizations — but also pro-Russia groups increasingly organized their structures for coordinated attacks. Nevertheless, this DDoS activity had limited impact on the targets, especially those with an anti-DDoS provider.
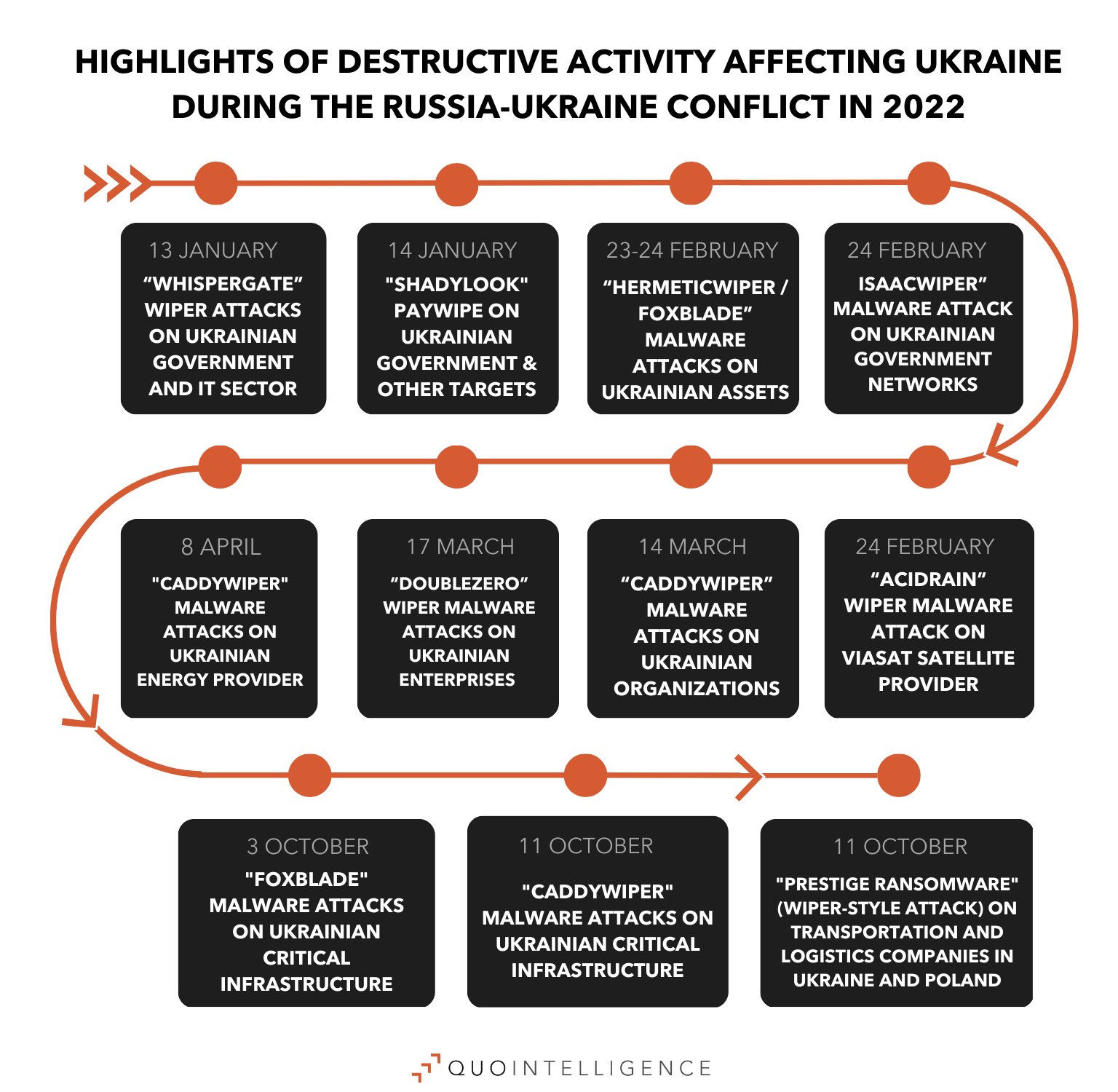
QuoIntelligence did not register cyberattacks on Ukrainian or its allies’ infrastructure that caused significant disruption. Yet, we recorded a high operational tempo of disruptive activities affecting Ukraine conducted by Russian-sponsored threat actors. The risk of potential cyberattacks and physical sabotage against critical infrastructure across Europe increased, particularly following the NordStream 2 pipeline sabotage incident. Also notable were Russian-backed APTs’ activities directed to other targets. For instance, Gamaredon, which consistently resorts to LNK files using mshta to fetch the payloads, targeted European institutions over 2022 and will likely continue to boost its intelligence collection against Ukraine and NATO allies this year.
In 2023, Russia will likely continue to resort to cyberattacks as an auxiliary to kinetic strikes in Ukraine. Cyber operations used during the war had a supporting character, being integrated into wider objectives of Russian Armed Forces, rather than being used as standalone measures. Beyond the scope of the ongoing Ukraine – Russia conflict, Moscow will likely continue to engage in cyber campaigns including sabotage and espionage, without exceeding the threshold of armed attack. As Russia has lost part of its economic and diplomatic power, and Russian state-sponsored cyberattacks launched during the 2022’s Ukraine – Russian conflict did not have significant impact compared to kinetic strikes, it will probably lead Russia to reassess its cyber capabilities.
Changes in geopolitical alliances will likely result in new state-sponsored cyber operations, as countries push for self-reliance and strategic intelligence gathering
As QuoIntelligence predicted, tensions in Asia increased in 2022, not only in the South China Sea, Taiwan, and Hong Kong, but also with North Korea reaching a record number of missiles fired in 2022.
For its part, China is showing willingness to continue enforcing its claims over the South China Sea in 2023. This is reflected in its extended mandate to its Coast Guard and maritime operations to persecute vessels involved in hydrocarbon exploration. Chinese-sponsored cyber operations will likely support intelligence gathering to allow more effective naval operations and increase economic pressure on rivals. As such, we will likely see more Chinese operations driven by the requirements set by agencies tasked with extending China’s influence over the subregion.
As instability grows in China and in the sub-region, this will likely increasingly lead investors and companies operating in China — or with Chinese suppliers — to quantify their exposure, reconsider continuing activity in the subregion, or move their production to cheaper and better-connected countries like Vietnam or India to avoid geopolitical risks.
Finally, we expect new geopolitical alliances to forge and old ones to vanish. As instability grows and geopolitical alliances shift, countries will boost efforts to reduce dependencies on foreign states. Still, some countries will have to resort to new strategic alliances to ensure provision of resources and counter common threats. Similarly, western countries will continue to end dependencies on Russian fuels, but also from Chinese strategical minerals and products. This is part of the continued drive toward self-reliance and resilience in strategic sectors such as semiconductors, telecommunications, energy, and rare earth materials.
US–China rivalry fueling risks of industrial espionage amid increasing competition for self-reliance in strategic sectors
As QuoIntelligence predicted in 2022’s outlook, increased polarization of the geopolitical landscape and growing economic competition between the US and China have fueled cyber espionage operations in 2022. In fact, as we anticipated, industrial espionage by APT groups remained a top threat for strategic industries throughout the year. Chinese state-sponsored threat actors launched new espionage campaigns, infiltrating entities in key sectors, and developed new ways to avoid detection and attribution. For instance, Winnti APT group reportedly conducted an intellectual property theft operation siphoning hundreds of gigabytes of intellectual property and sensitive data from technology and manufacturing companies in North America, Europe, and Asia.
The economic competition between the US and China increased in intensity with new US export controls restricting China’s access to advanced semiconductors. Meanwhile, despite substantial efforts to develop a self-reliant Chinese semiconductor industry, China remained dependent on foreign suppliers.
In 2023, the US will continue to cut China’s access to semiconductors and will probably extend restrictions to other advanced technologies, such as quantum computing and artificial intelligence. The Biden administration will also push its allies to adopt similar bans. In reaction, China will likely try to develop new and existing trade partnerships.
In the cyber threat landscape, development of domestic capabilities will likely be supported by espionage efforts, including through cyber operations. This will not represent a notable change of posture as China continuously engages in industrial espionage. However, increased pressure will likely translate into reassignment of intelligence goals as intelligence leaders are pushed to deliver results.
Geopolitical race to secure green technologies and increased pressure on businesses over environmental concerns
Climate change effects became more pronounced in 2022, not only impacting developing countries but also Western countries and economies. This observation, together with the energy crisis amplified by the war in Ukraine, intensified the global rush toward energy transition. Against this background, environmental activist protests and operations also increased in 2022.
In 2023, climate change and energy transition will remain pressing issues for governments, businesses, and society in general. Scrutiny of companies over environmental concerns will increase. In the regulatory landscape, the EU will adopt new regulations to achieve climate neutrality. Environmental activist groups could resort to more radical tactics targeting companies. Finally, in the cyber threat landscape, this will possibly translate in increased risk of industrial espionage for the green tech sector, as new technologies become increasingly strategic for energy transition.
CONCLUSIONS
Here are our three main takeaways from what we see for 2023:
-
New more efficient business models for eCrime
Threat actors will continue to develop new business models and TTPs to gain efficiency and avoid disruption to activity. As such, detection of initial access brokers’ activity will become increasingly important due to its role as a ransomware deployment precursor.
Mercury 2.0, our client platform, provides a curated knowledge base of Threat Actors and as-a-Service providers, their TTPs and other information on how to detect and mitigate them.
-
Governments to regulate for customer data protection and continuity of essential services
With cyber risks increasing for both private and public sectors we predict governments will adopt new regulations imposing cyber security requirements on companies to protect customer data and ensure critical entities are able to maintain essential services.
QuoIntelligence provides tailored intelligence reports highlighting legislation and regulation changes that may impact your technology, budget, and resources.
-
Cyber and Geopolitics increasingly intertwined
We expect continued worldwide instability, with new alliances forging and nations trying to achieve self-reliance in their strategic sectors. As such, geopolitical tensions will continue to heavily influence the cyber threat landscape with new politically-motivated threat actors and campaigns. Risk of industrial espionage will remain high for companies in strategic industries. Hacktivism will remain a tool for Russia to impose a cost on Western countries, however, its impact will not be significant enough to influence political decision-making.
QuoIntelligence provides early warnings of rapid changes on your threat landscape, analyzing the impact of geopolitical events on your business and how they influence the cyber threat landscape.



