As with all malware, there is no way to stop all infostealer malware attacks all the time.
And there is never a positive outcome if you are a victim of one. Information stealer attacks are invisible and target organizations and individuals from every sector.
Their goal is always the same: steal sensitive information. Anything from login credentials and financial information to sensitive business data and intellectual property. Anything that cybercriminals can use to commit fraud, identity theft, and carry out other types of cybercrime.
How likely are you to be targeted, and are you already a victim of this dangerous attack vector and don’t know?
Let us start by looking at the makeup of a typical infostealer malware attack:
Preying on Network Weaknesses and Virtually Undetectable
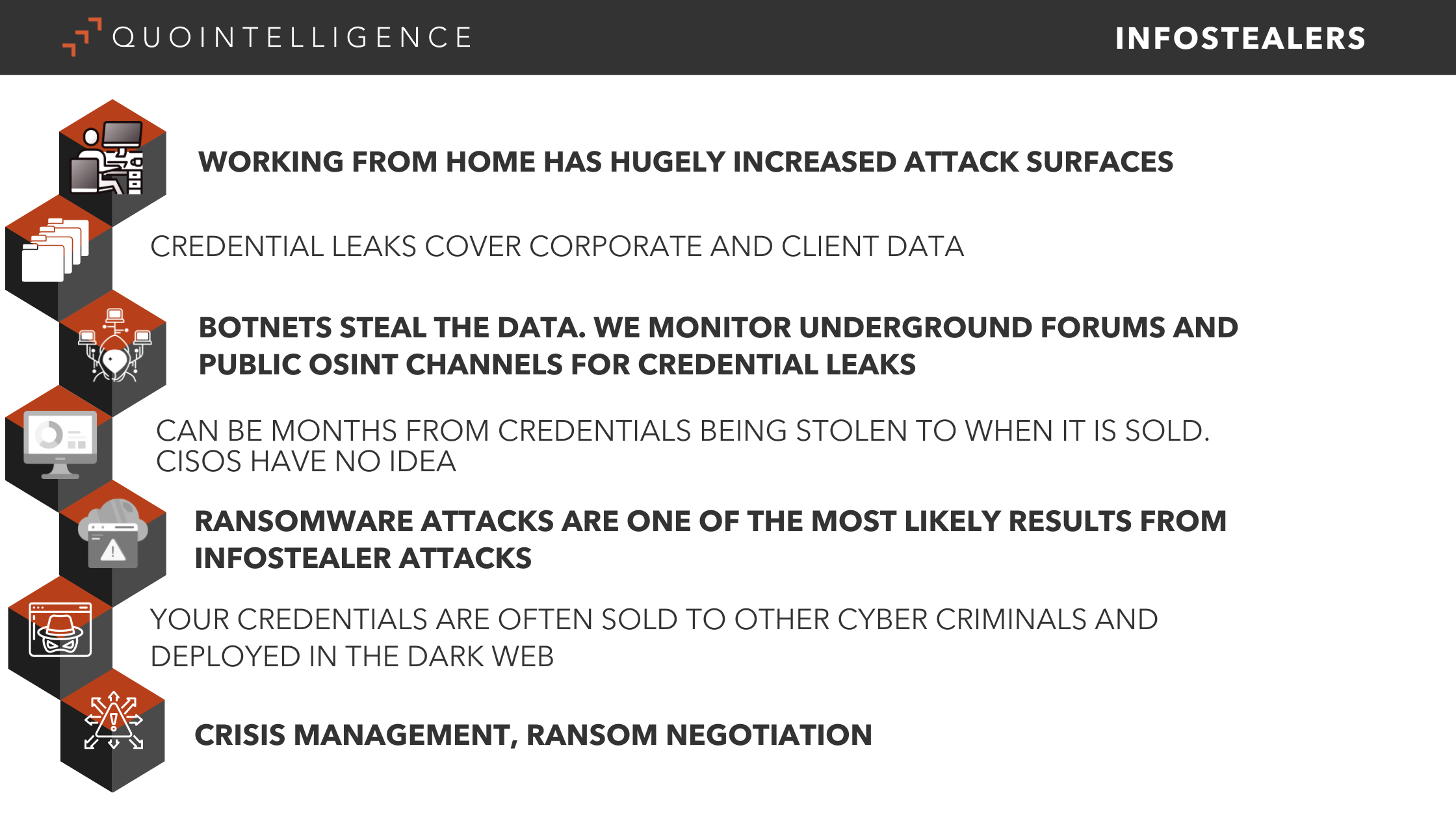
Cybercriminals have developed — and continue to update — infostealer malware. This overshadows the many benefits that working from home offers your organization. Infostealers leverage the often weaker security measures installed in home-based employees’ computers, and servers which aren’t properly configured to gain access to an organization’s network.
The computers of remote workers have become the playground of malicious actors who are using a combination of infostealer malware to steal credentials together with social engineering to carry out high-profile breaches. They’re also using fatigue attacks to circumvent the more secure and extra layer of MFA (multi-factor authentication).
Just by accessing business email via an infostealer attack, hackers can use employees’ work accounts to enter the company’s computer and cloud systems. This leaves your organization vulnerable to a wide variety of attacks, including but not limited to:
- Data Theft
- Data Encryption
- Ransomware
- Financial Fraud
Virtually undetectable
Threat actors are able to make this activity virtually undetectable. This affords them precious time to retrieve as much critical information as they wish, carry out identity theft, destruction of infrastructure, and more.
Ultimately this can cause serious interruption to an organization’s activity, loss of customer data and trust and potentially massive financial loss — even closure of the business.
Gathering all this data gives cyber criminals plenty of options. They can either sell it to other bad actors or use it themselves. In either case, a very common next step is to launch a ransomware attack.
- Ransomware attack
Customers are worried about their personal data, business partners about cross-contamination, and regulators worried about consumer protection. Investors are also watching the business closely are looking at the short and long-term financial impacts and brand viability.- Paying the ransom puts your organization at risk of being targeted again.
- If you refuse to pay the ransom, your data will be sold in the dark web. Unsurprisingly, there is a market for credentials obtained via infostealer attacks and it is booming. Dark Web users communicate privately, without being tracked or monitored by private companies, the government or law enforcement. Removing data from the Dark Web is mostly implausible.
The simple, natural conclusion from this is that companies should take preventative anti-ransomware measures across all end points to prevent infostealers from extracting and encrypting sensitive information.
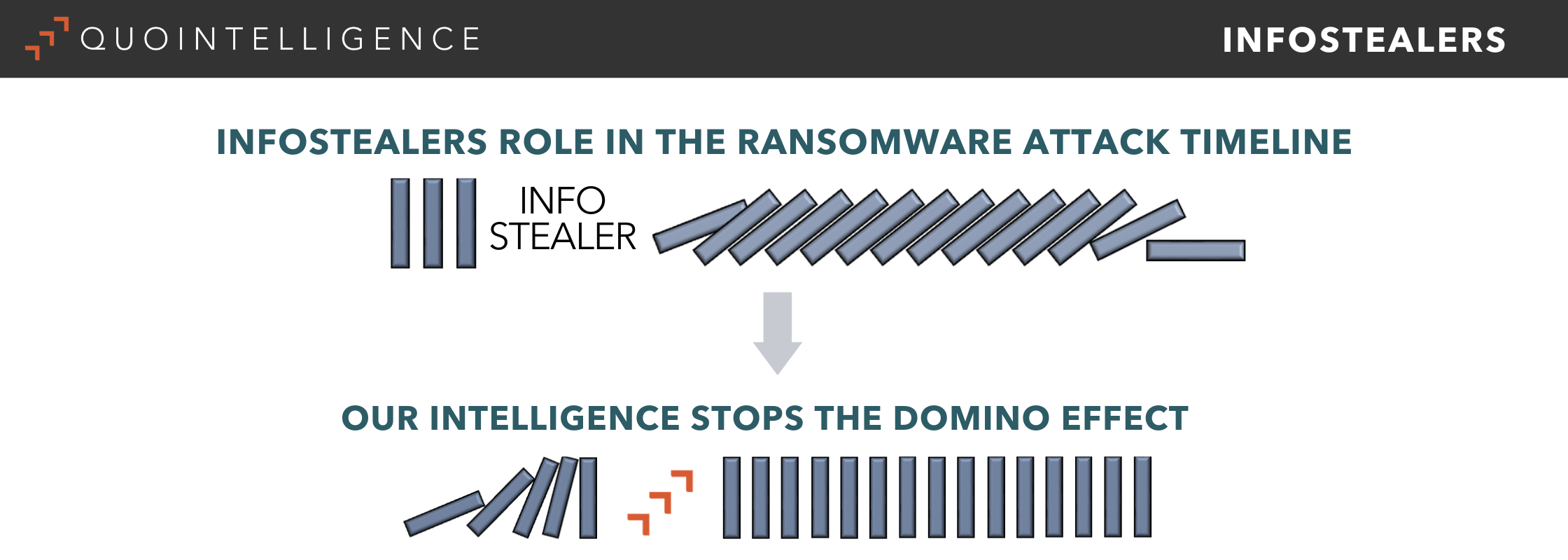
Threat Intelligence and the “Domino Effect”
Consider an organization’s operations as a row of dominoes. If any one of them falls, all the following dominoes fall as well. When a threat actor successfully carries out an infostealer malware attack, it has the effect of knocking over a single domino. The effect can be catastrophic.
Threat Intelligence — a vital element
There are many actions a CIO or CISO can and should do to avoid looking at a metaphorical table of fallen dominoes. One element to implement is a robust Threat Intelligence function as part of the overall cybersecurity strategy and operations. The QuoIntelligence Intelligence Analyst Team has put together a Technology Brief on the powerful threat of infostealer malware. They assess that infostealer attacks will remain in the threat landscape and continue to grow. We see various Infostealer families continuously updating methods to include more capabilities and functionalities while maintaining low detection rates.
Of the several courses of action QuoIntelligehnce recommends, one is to actively monitor and register logs to identify suspicious network or local activity within corporate environments (if you would like to find out more we will be happy to hear from you: Let’s talk).
By including threat intelligence in its approach, an organization is effectively preventing the infostealers from pushing over that single domino.
Conclusion
As we have observed, infostealer malware is here to stay and growing. The ease of access to various infostealers that bad actors enjoy means they are a popular choice. The relatively high level of success using this tool further ensures their continued existence.
Once an organization has become a victim of an infostealer attack, it may not realize until much later. By that time the damage is done.
Having access to finished threat intelligence, tailored to your specific needs is one vital element to your defense against this dangerous attack vector.
If you wish to keep up-to-date with the latest developments on infostealer malware and other cyber and geopolitical threats, please request a free subscription to our Weekly Intelligence Snapshot issued every Thursday at 1900CET.
