In early May, Colonial Pipeline, the supplier of over 45% of fuel to the East Coast, suffered a massive ransomware attack that encrypted its infrastructure. The company had to shut down some of its operations and IT systems, leading to a gas and oil shortage in the US.
The FBI blames the attack on DarkSide, a relative newcomer to the ransomware community which is anything but inexperienced.
Their most recent attack crippled Colonial Pipeline’s distribution and caused socio-economic damages. The resulting oil shortage increased prices, and closures of gas stations display just how impactful cyberattacks on Critical National Infrastructure (CNI) can be.
But the attack didn’t just cause issues for the government and its people. The attack on CNI was also denounced by several underground forums and service providers. Our research shows that DarkSide will feel some repercussions themselves.
Although Colonial Pipeline paid the group USD 4.4 million in ransom, the cybercriminal community denounced the attack. Some forums want to avoid further disruptions and possible law enforcement crackdown by casting out ransomware activities from their platforms and forums.
Dark Times for DarkSide
According to DarkSide ransomware operators, the group lost control of its public infrastructure, specifically its blog, CDN servers, and payment servers.
Additionally, reports indicate that an unknown source withdrew cryptocurrency from DarkSide’s payment servers, sending it to an unknown address.
The political response to Colonial Pipeline attack
An anonymous US official confirmed to NBC News that Colonial paid a ransom of almost USD 5 million to the cybercriminal group. It’s still uncertain when the transaction happened, and US President Joe Biden declined to comment on the ransom.
Still, the US prepared a response to the cyberattack on Colonial Pipeline. Ransomware is undoubtedly still a leading issue on the threat landscape. Therefore, US government departments and security vendors are increasing their scrutiny on ransomware groups for targeting critical infrastructure.
The political response isn’t the only concern for the cybercriminal group, though.
Cybercriminal prosecution as a result of the attack
QuoIntelligence noticed that three major underground forums – XSS, ExploitForum, and RaidForums – started disallowing any kind of ransomware services and ads hosted on their platforms.
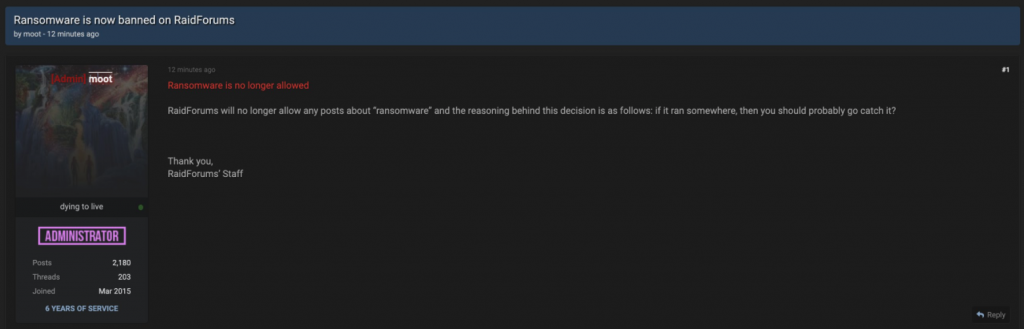
Currently, the forums only permit link sharing for leaked data and ransomware group blogs. These actions indicate that the dark web forums are distancing themselves from attacks on CNI and therefore, distancing themselves from DarkSide’s attack on Colonial Pipeline.
The XSS forum had the strongest response to DarkSide, freezing the ransomware group’s deposit of around BTC 22 (approx. EUR 756,341). However, they are allowing potential affiliates of the group to claim an unofficial reimbursement for their services.
Further, other ransomware operators are also backing away from the whole idea of Ransomware-as-a-service (RaaS).
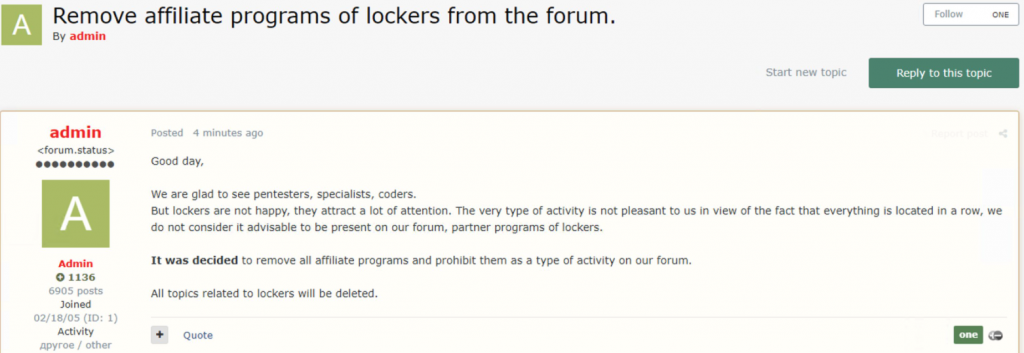
During Dark Web monitoring, QuoIntelligence noticed an individual allegedly tied to REvil ransomware operators announcing their plans to start working privately and stop advertising RaaS offerings. Moreover, REvil reportedly claims to no longer target the healthcare, education, or government sectors of countries to avoid the spotlight.
Avaddon ransomware operators followed suit, devising plans to go private and exclude the sectors mentioned above in the future.
DarkSide’s ransomware attack against critical national infrastructure was stepping over the line. Consequently, it is likely to result in increased government scrutiny on ransomware operators. While ransomware groups might retreat from targeting critical infrastructure, they will likely continue targeting private organizations.
Will the ransomware community change its approaches?
Ransomware communities are distancing themselves from DarkSide. Could this be a sign that ransomware operators will more carefully vet their targets in the future to make sure not to target CNI? Could this mean the end of ransomware? Unfortunately, there’s no reason to believe so.
The reality is, that ransomware operators will likely refrain from targeting CNI for its high risk of intensified law enforcement but will continue to target the private sector. In fact, our research shows that ransomware activities are not decreasing at all. DarkSide is continuing to target private organizations:
- DarkSide attacks Toshiba and Brenntag: After the attack on Colonial Pipeline on 7 May, DarkSide conducted confirmed activity on Toshiba’s French and European branches. Toshiba Tec shut down networks between Japan, Europe, and its subsidiaries to “prevent the spread of damage” and implemented recovery protocols data backups.
- A separate attack on German chemical distributor Brenntag resulted in the loss of sensitive data exceeding 150 Gigabytes. The company paid approximately EUR 3.2 million (USD 4.4 million) to recover their encrypted information.
- Irish HSE compromised:
An unknown attacker compromised the IT systems of the Irish Health Service Executive (HSE). Anne O’Connor, HSE’s COO, confirmed the attack was a “zero day threat”. The attack compromised several systems, causing disruption in services and delaying the distribution of the COVID-19 vaccine. - Reportedly, the Irish HSE received a Bitcoin ransom request, but the Irish Minister of State claimed they wouldn’t pay it.
- QNAP reports eCh0raix ransomware: QNAP, a Taiwanese corporation specializing in Network Attached Storage (NAS) devices, reported eCh0raix ransomware (also known as QNAPCrypt) affected QNAP devices. Following the detection, the company released a security advisory.
- QNAP released another security advisory for an unrelated event, warning of a zero-day vulnerability in the Roon Server. Cybercriminals have previously exploited similar vulnerabilities for delivering ransomware payloads.
- Avaddon targets AXA: Avaddon took credit for the attack on a Southeast subsidiary of AXA, a multinational insurance group. The cybercriminal group threatened to publish 3 Terabytes of stolen sensitive data if AXA didn’t comply with its requests by a set deadline. In addition, Avaddon threatened to extend its AXA attack to a full-on Distributed Denial of Service (DDoS).
- Both the FBI and Australian Cyber Security Centre (ACSC) warned of intensifying Avaddon activity.
- REvil offers triple extortion software: According to CheckPoint researchers, REvil is now offering Distributed Denial-of-Service (DDoS) attacks and voice-scrambled VoIP calls. Its affiliates can use these extortion tools to further pressure their targets into paying their ransom requests on time.
- Babuk shares its source code:
Monitoring the Dark Web, QuoIntelligence noticed Babuk operators claiming to have shared its ransomware source code. An unknown team has received the source code and will continue developing it under a new brand.
The overview of recent activity above shows that neither DarkSide nor other ransomware operators are showing signs of slowing down. As long as affected organizations are paying ransom, ransomware providers will continue targeting the private sect.
The Ransomware Community Is Here to Stay
However, considering the reactions to the DarkSide’s attack on Colonial Pipeline, ransomware operators will likely increase caution. They’ll have to work harder to avoid critical infrastructure and better vet both the intended targets and the scope of their attacks.
Still, it’s evident that threat actors will continue to conduct attacks and develop new pressure tactics to gain the ransom demand from victims. After all, the attacks following Colonial Pipeline show that organizations are still willing to pay.
We expect that ransomware operators will find new ways to advertise, promote, and support their services.
Join our newsletter, to stay up-to-date on all ransomware activies around the globe. Did you know? As a newsletter subscriber, you can access our full Weekly Intelligence Snapshot for free via Mercury.
