In late 2020, QuoIntelligence identified a malicious Word document.
The Word document contained technical indicators associated with an Agent Tesla malware campaign, a readily available Remote Access Trojan (RAT) that steals keystrokes and credentials. It ultimately led us to uncover the operation of a Nigerian eCrime gang.
Based on our investigation, we dubbed the eCrime gang “E.K.P.”. Further, we understand that they are located in Nigeria. We also learned that E.K.P is an operator within a service model known as Malware-as-a-Service (MaaS).
MaaS & RaaS: The All Skill-Level eCrime Conductors
Cybercriminals are increasingly adopting MaaS for conventional malware campaigns and ransomware deployments (Ransomware-as-a-Service or short RaaS). Due to the offered capability and low barrier-to-entry, it doesn’t take a lot of skill to conduct attack campaigns.
In this report, we highlight the daily operations of E.K.P and the various commodity tools used to both stage and execute attack campaigns.
Uncovering E.K.P
The Microsoft Word document that we discovered in 2020 was entitled ”Azerbaijan-Turkey Military Negotiation.doc”. Apparently a user from a VirusTotal in the Netherlands containing a weaponized macro uploaded it.
If the cyber attacker can successfully convince their target to open the document, the kill-chain will be launched, and the malware will be able to steal the information of the person who opened the file.
Word document titled Azerbaijan-Turkey Military Negotiations.doc that E.K.P. used as lure for their recent attack
E.K.P. Kill-Chain and Tesla Agent’s Connections to Other Malware Families
The macro embedded with the Word document obfuscates, i.e., creates difficult-to-read code, to another simple obfuscated script. This script then tries to download and execute a payload retrieved from a Command and Control (C2) URL.
Unfortunately, at the time of analysis, we could not retrieve the file.
However, we determined additional files associated with the same C2 URL: a widespread malware family known as Agent Tesla.
Agent Tesla is a readily available keylogger and Remote Access Trojan (RAT), written in .NET. Its primary function includes logging keystrokes and the clipboard to exfiltrate data ultimately.
At least this specific variant attempts to exfiltrate data from the victim using hardcoded Simple Mail Transfer Protocol (SMTP) credentials for an attacker-controlled mailbox.
Another malware family tied to the C2 Infrastructure is “Remcos RAT,” giving a cybercriminal complete control of an infected system.
Its capabilities include keylogging and surveillance through audio and screenshots.
Sir Pee and Day to Day Operations at eCrime gang E.K.P.
Based on what we have learned so far, we dubbed the cybercriminal gang E.K.P, and we understand that they are located in Nigeria.
E.K.P. starts the day by communicating with customers and its management to determine the needed actions for the day.
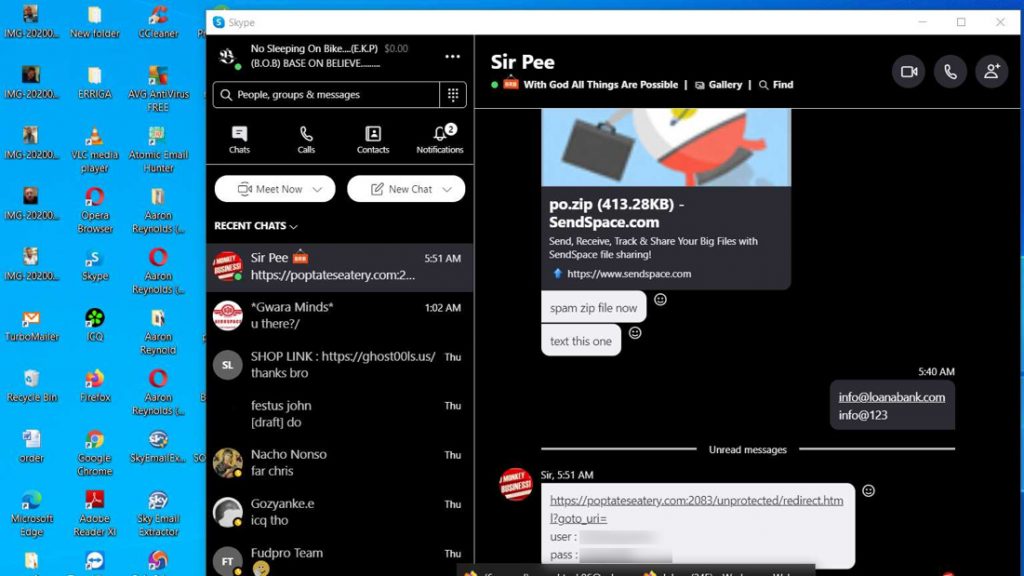
Screenshot of the conversation thread between E.K.P. members, their managers, and clients
Based on other conversation threads, the contact with the moniker Sir Pee appears to be the manager of E.K.P.
As you can see in the screenshot above, Sir Pee instructs E.K.P to “spam zip file now” and then sends the link to where the malicious file is uploaded.
E.K.P responds with login credentials for an email account to the domain loanabank[.]com. The domain appears to be a fake bank page.
Sir Pee, in turn, sends E.K.P credentials for a CPanel – a control dashboard to facilitate the management of a web hosting server.
Screenshot of Loanabank’s homepage – a fake bank domain
E.K.P.’s multi-functional, multi-vendor attacker toolset
Our observations indicate clearly that E.K.P uses various malware builder kits, services, and inboxes for conducting their operations.
After starting the day checking in with the apparent manager, E.K.P begins with their operational rounds by accessing their web shell on predilletastore[.]com[.]br.
According to our research, the site is likely a compromised WordPress website hosting a web shell. E.K.P. uses this for attack operations and to control compromised hosts remotely.
Further, the eCrime gang leverages it to store their attack tools such as payloads and files.
Screenshot of predilletastore[.]com[.]br – E.K.P. web shell
Based on their contact list, E.K.P seems to have access to a wide range of tools, especially if a potential customer requires capabilities outside the gang’s service catalog.
However, during our observations, E.K.P heavily relied on mainly three core malware builder kits.
Exploit Builder (version 1.5.0.1):
A premium product requiring a license. Exploit Builder enables E.K.P to create an exploit document (e.g., Microsoft Word or Excel) that delivers a malware payload to a victim host. At first, the gang creates a payload using Origin Logger. Secondly, they obfuscate the payload with the Cassandra Crypter service.
Origin Logger (also known as Agent Tesla):
Through our analysis, we confirm that the payload generated by Origin Logger is nearly the same as previously decoded Agent Tesla payloads.
The C2 panel interface matches the same panel that threat actors use for the malware Origin Logger, bundled with the C2 panel, and then sold to attackers.
As the name suggests, its primary purpose is logging keystrokes, clipboard data, HTTP cookies, taking periodic screenshots, and viewing the webcam of infected computers.
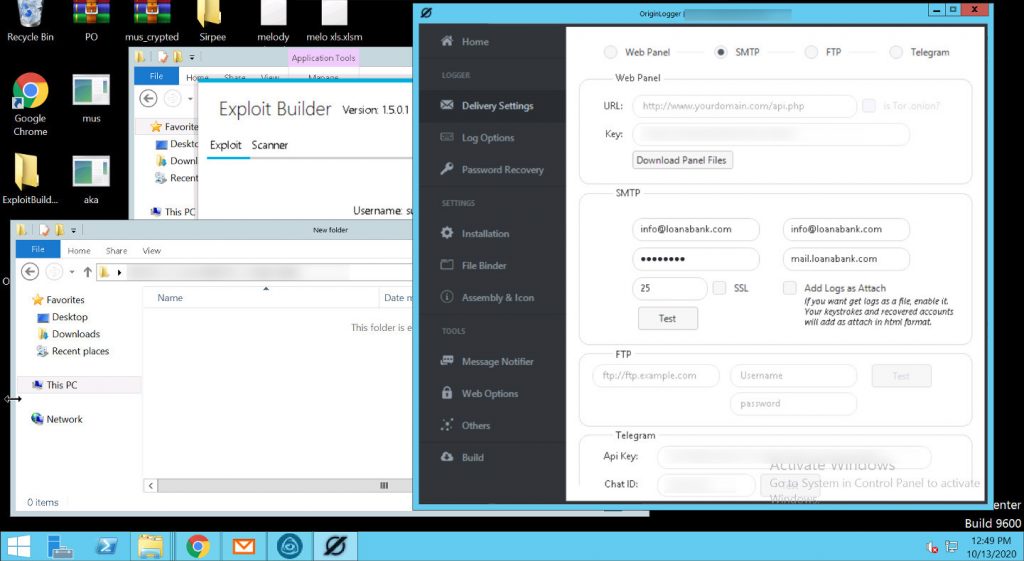
Screenshots showing Exploit Builder and Origin Logger
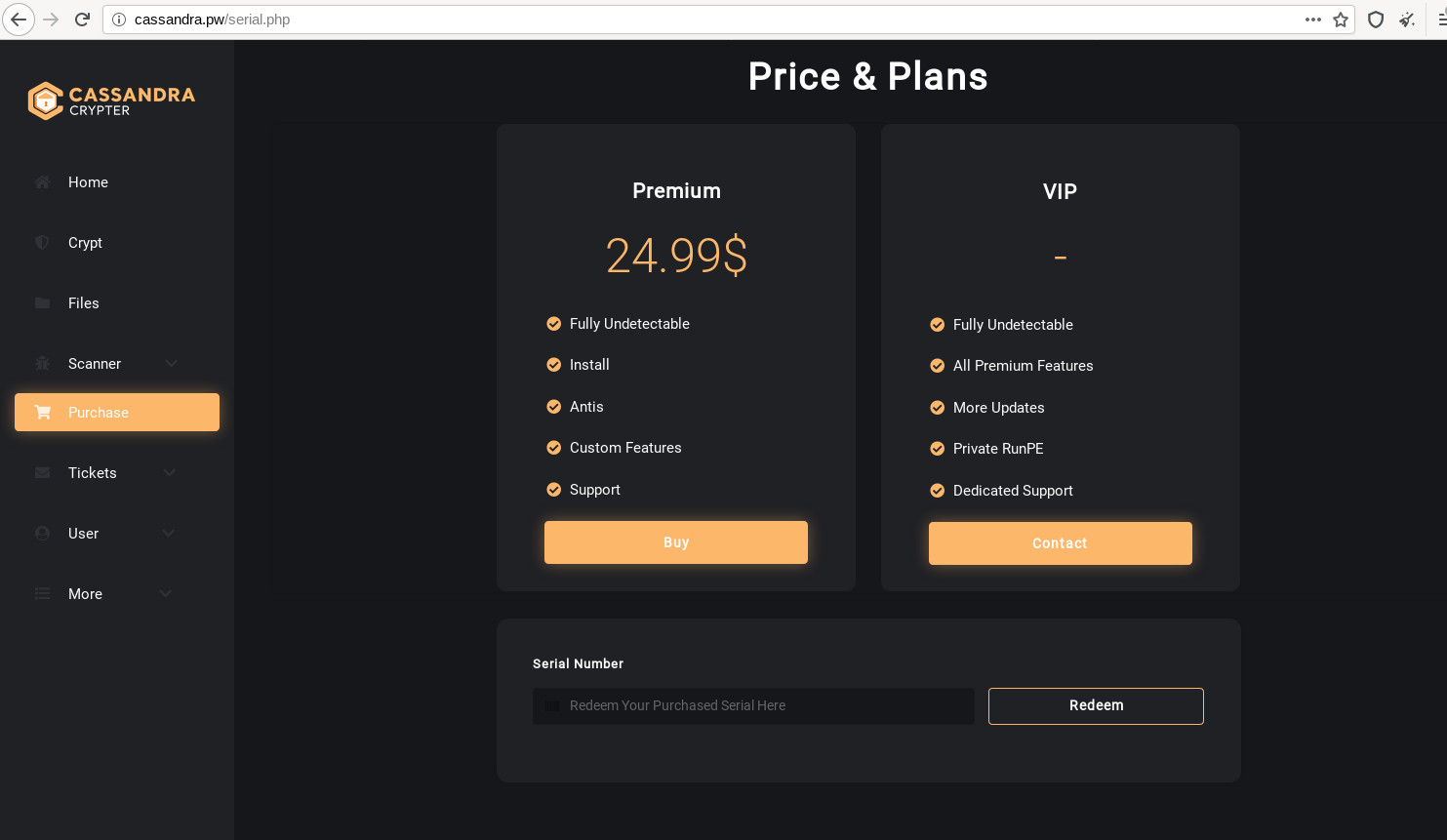
E.K.P leveraged the Origin Logger builder to create multiple variants to infect victims. For obfuscation of the payloads, the threat actor used the online service known as Cassandra Crypter.
Cassandra Crypter Service:
Based on their website, Cassandra Crypter Service describes itself as:
A cloud crypter which is coded by the coder of PoisonCrypter, it will be updated daily twice or even thrice (if needed). As a result, it will be giving you a FUD result and always fud for the premium users. It is working with both native and managed assemblies (running since 2018)
The customized obfuscation (e.g., ConfuserEx) of the .NET Agent Tesla payloads offered through Cassandra Crypter is available through two subscription plans: The Premium or VIP Plan.
The Premium Plan can be paid directly and works automatically, while the VIP Plan requires the subscriber to contact support first for personalization.
Screenshots of the Cassandra Crypter Dashboard and the service’s pricing plans
While E.K.P expedites the time spent preparing malware variants and malicious documents for the attack campaigns using different tools, they eventually get to the distribution part.
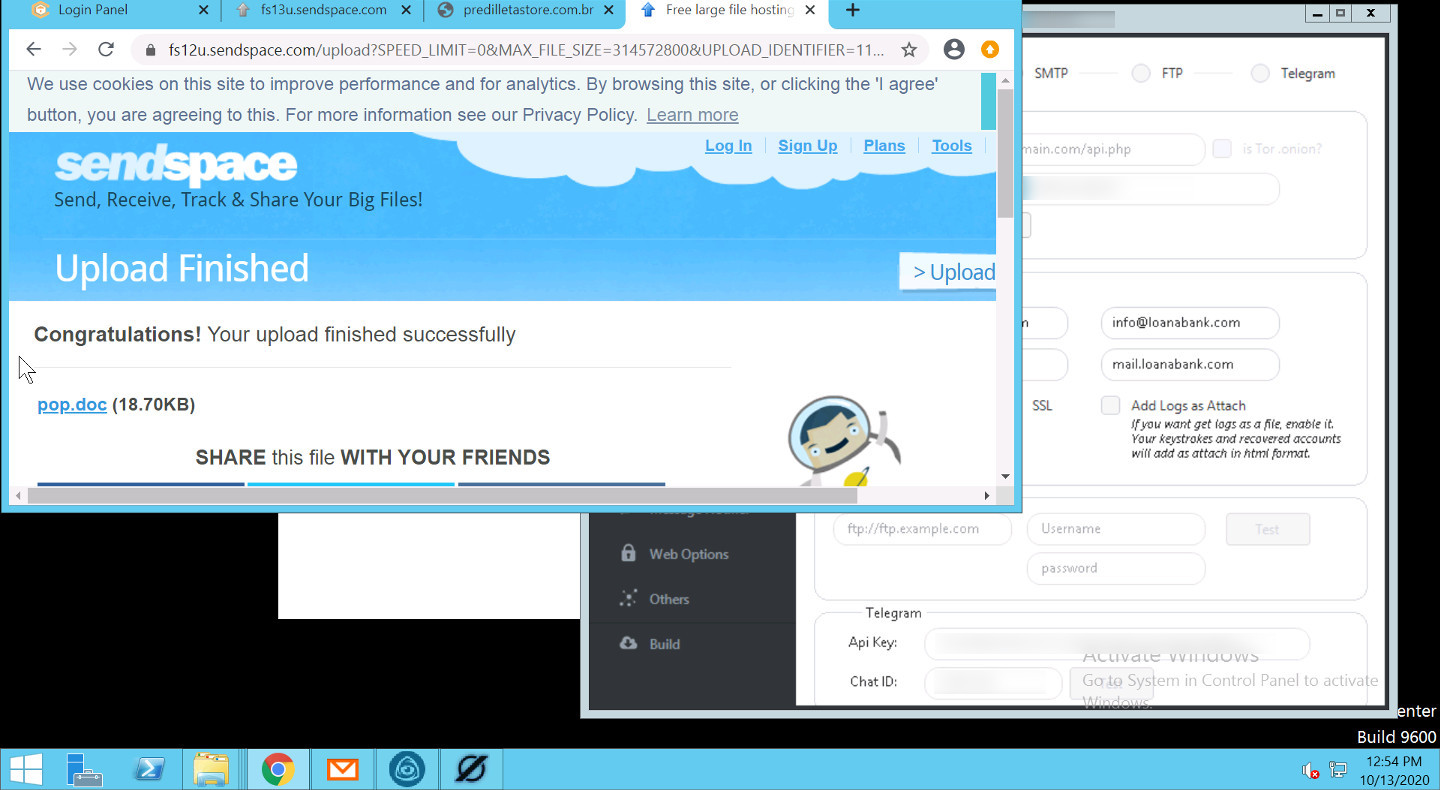
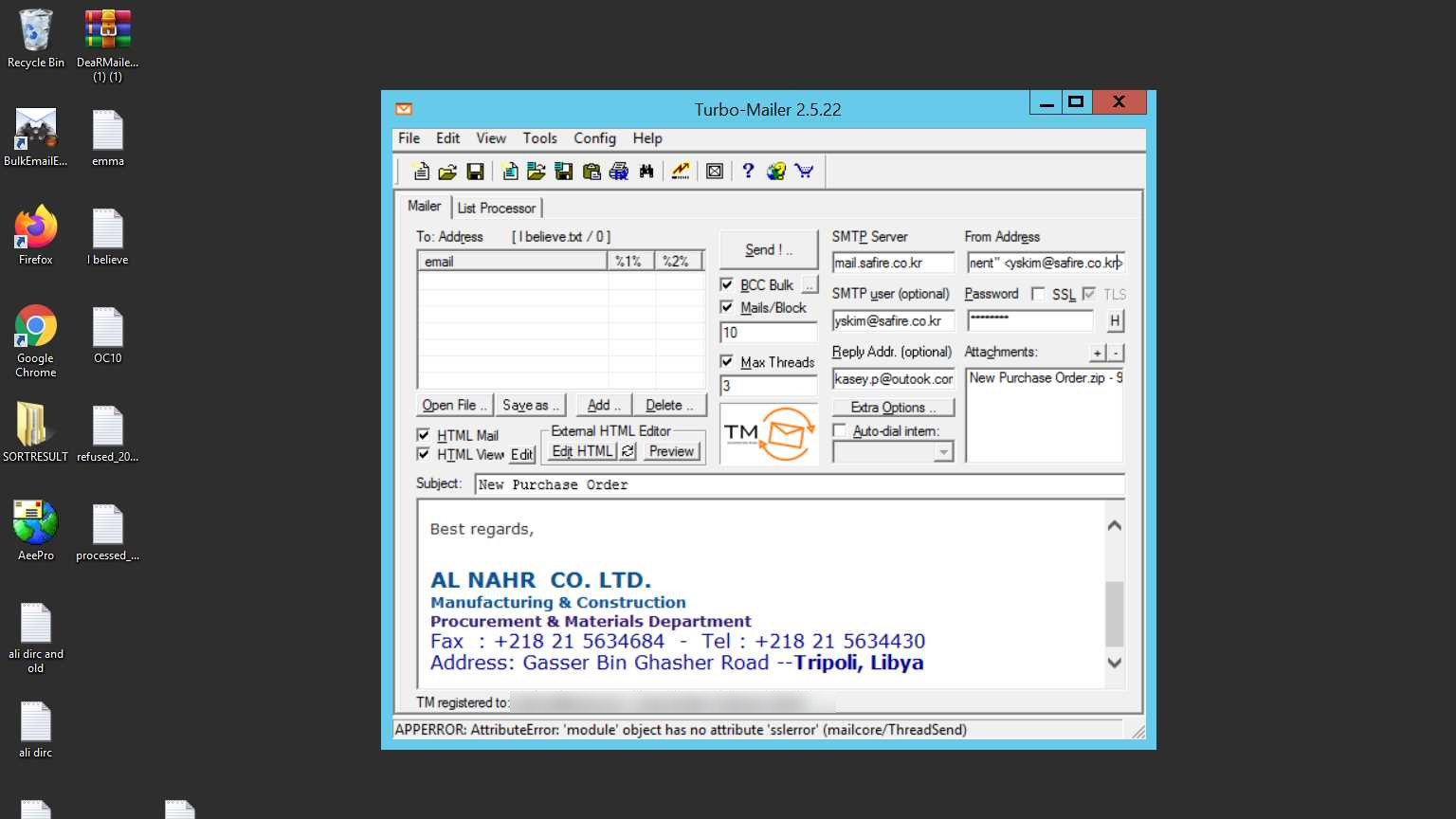
Consequently, they will check with their manager again for the target details. E.K.P communicates with multiple contacts throughout the day and even uses Sendspace – a free hosting site for instant file transfers – to receive and transfer documents for campaigns.
Screenshots of Sendspace and Turbomailer – both used by the Nigerian eCrime gang E.K.P.
Another tool that E.K.P frequently uses for mass emails is the Xleet Phishing Service, a service popular amongst threat actors to distribute spear-phishing emails throughout various attacks.
One of the services offered by the marketplace where Xleet is sold, is access to a compromised server that hosts the PHP web shell that enables ongoing access to the server.
QuoIntelligence recently analyzed campaigns attributed to top-tier threat actor “Cobalt” group, using a PHP-mailer script placed on a likely compromised server used to distribute spear-phishing emails.
The Raise of eCrime Toolset Services
This investigation is an example of the effectiveness of the cybercriminal underground offering competent toolset services.
Through Malware-as-a-Service (MaaS) and other subscription models, less-skilled individuals can execute low-effort cybercrime.
A similar, slightly more complex MaaS often used by APTs is the Golden Chickens (GC) MaaS.
Since 2018, QuoIntelligence has tracked and highlighted the evolution of the Golden Chickens (GC) MaaS and how different actors use it, including top-tier threat actors FIN6, Cobalt, and Evilnum.
By 2019, we uncovered eleven tools attributed to the GC MaaS and each customized per campaign for the threat actor purchasing the service.
In general, attributing attack activity to threat actors leveraging a MaaS is often complicated. The services offered can include both C2 infrastructure and malware variants. These are available to all MaaS customers, whether script kiddies or Advanced Persistent Threat (APT) actors.
E.K.P.: A Highly Active MaaS Provider Supporting Multiple Campaigns Simultaneously
Our investigation uncovered E.K.P’s day-to-day operation over a couple of months. It became clear that the threat actor is highly active, supporting multiple campaigns in parallel, and leveraging complete and straightforward toolsets to monetize activity.
E-Crime is a large ecosystem consisting of interconnected services, schemes, and affiliate networking in the cybercriminal domain. Overall, their primary goal is financial gain. QuoIntelligence will continue to observe threat actors like E.K.P, which are operating non-complex but effective eCrime services.
Apendix
Malicious document (maldoc)
- 7007f35df3292a4ecd741839fc2dafde471538041e54cfc24207d9f49016dc77
Maldoc name
- Azerbaijan-Turky Military Negotiation.doc
Maldoc C2
- https://cannabispropertybrokers[.]com/pop/8OwWKrFQ0gQoKt9[.]exe
AgentTesla (delivered by maldoc)
- cda07296d20a239bdb9cb5a2c9a814f69811bc85ced8bf32e998b906a413f416
REMCOS RAT packed
- 15170d0dbe467efc4e38156ed4e03702ae19af44c100d7df7a75c6dbdb7ac587
REMCOS RAT upacked
- 4d755262fd2c7f0539f919d300c7ebc3bd70267c002bcb8edd886a40e3f8ba75
REMCOS RAT C2
- 79.134.225[.]72:64843
MITRE ATT&CK Tags
| APK SHA1 Hashes | Main Activity Name | Impersonated Institution |
| de8929c1a0273d0ed0dc3fc55058e0cb19486b3c | com.neonet.app.reader.MainActivity | BBVA |
| b344fe1bbb477713016d41d996c0772a308a5146 | com.neonet.app.reader.MainActivity | Laboral Kutxa |
| 8a099af61f1fa692f45538750d42aab640167fd2 | com.neonet.app.reader.MainActivity | Correos |
| ab14161e243d478dac7a83086ed4839f8ad7ded8 | com.neonet.app.reader.MainActivity | BBVA |
| ded2655512de7d3468f63f9487e16a0bd17818ff | com.neonet.app.reader.MainActivity | CaixaBank |
| a5208de82def52b4019a6d3a8da9e14a13bc2c43 | com.neonet.app.reader.MainActivity | CaixaBank |
| 21112c1955d131fa6cab617a3d7265acfab783c2 | com.neonet.app.reader.MainActivity | Openbank |
| 6ea53a65fe3a1551988c6134db808e622787e7f9 | com.neonet.app.reader.MainActivity | Unicaja |
| 62236a501e11d5fbfe411d841caf5f2253c150b8 | com.neonet.app.reader.MainActivity | BBVA |
| 7f0c3fdbfcdfc24c2da8aa3c52aa13f9b9cdda84 | com.neonet.app.reader.MainActivity | BBVA |
| f918a6ecba56df298ae635a6a0f008607b0420b9 | com.neonet.app.reader.MainActivity | Santander |
| ffbcdf915916595b96f627df410722cee5b83f13 | com.neonet.app.reader.MainActivity | BBVA |
| 7b4ab7b2ead7e004c0d93fe916af39c156e0bc61 | com.neonet.app.reader.MainActivity | CajaSur |
| 34d0faea99d94d3923d0b9e36ef9e0c48158e7a0 | com.neonet.app.reader.MainActivity | BBVA |
| e6c485551d4f209a0b7b1fa9aa78b7efb51be49b | com.neonet.app.reader.MainActivity | BBVA |
| 1df3ed2e2957efbd1d87aac0c25a3577318b8e2a | com.neonet.app.reader.MainActivity | BBVA |
| 6a907b8e5580a5067d9fb47ef21826f164f68f3f | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 5d1c7ff3d16ec770cf23a4d82a91358b9142d21a | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 86ad0123fa20b7c0efb6fe8afaa6a756a86c9836 | com.neonet.app.reader.MainActivity | Grupo Caja Rural |
| 14a36f18a45348ad9efe43b20d049f3345735163 | com.neonet.app.reader.MainActivity | Cajalmendralejo |
| b506503bb71f411bb34ec8124ed26ae27a4834b9 | com.neonet.app.reader.MainActivity | BBVA |
| afe84fa17373ec187781f72c330dfb7bb3a42483 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 445468cd5c298f0393f19b92b802cfa0f76c32d4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 8491ff15ad27b90786585b06f81a3938d5a61b39 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 2714e0744ad788142990696f856c5ffbc7173cf4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 1ce0afe5e09b14f8aee6715a768329660e95121e | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 96a3600055c63576be9f7dc97c5b25f1272edd2b | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 9954ae7d31ea65cd6b8cbdb396e7b99b0cf833f4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 07159f46a8adde95f541a123f2dda6c49035aad1 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| ab19a95ef3adcb83be76b95eb7e7c557812ad2f4 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| db8eeab4ab2e2e74a34c47ad297039485ff75f22 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| dbf0cec18caabeb11387f7e6d14df54c808e441d | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 69d38eed5dc89a7b54036cc7dcf7b96fd000eb92 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| c38107addc00e2a2f5dcb6ea0cbce40400c23b49 | com.cannav.cuasimodo.jumper.actividades | BBVA |
| 279048e07c25fd75c4cef7c64d1ae741e178b35b | com.uklapon.mafin.chinpiling.actividades | Bankinter |
| ef8c5d639390d9ba138ad9c2057524ff6e1398de | BBVA | |
| e7c2d0c80125909d85913dfb941bdc373d677326 | ING | |
| 145bd67f94698cc5611484f46505b3dc825bd6cd | BancoEstado |


![Screenshot of homepage of Ioanabank[.]com Homepage of Ioanabank[.]com - a fake bank domain E.K.P. is using](https://quointelligence.eu/wp-content/uploads/2021/06/image4.jpg)
![Screenshot of E.K.P.'s web shell on predilletastore[.]com[.]br E.K.P.'s web shell on predilletastore[.]com[.]br](https://quointelligence.eu/wp-content/uploads/2021/06/image5-1024x561.jpg)